Biometrics, or bio-identification, is the practice of measuring physical characteristics of a person to verify their identity. The most common biometric systems measure fingerprints or hand prints. More advanced biometric systems measure the users voice, features of the users eyes, or the geometry of their entire face. Futuristic systems measure the users ears, their smell, or even their DNA itself. Biometrics are more secure than passwords, but they can also be fooled. For example, one hacker discovered that fingerprint readers could be fooled by copying a fingerprint using the goo Read More
Packet Fragmentation
Every packet based network has an MTU (Maximum Transmission Unit) size. The MTU is the size of the largest packet that that network can transmit. Packets larger than the allowable MTU must be divided into smaller packets or fragments to enable them to traverse the network. Network Standard MTU Ethernet 1500 Token Ring 4096 Packet Headers Every IP packet has an IP (Internet Protocol) header that stores information about the packet, including: Version IHL Type of Service Total Length Identification Flags Fragment Offset Time to Live Protocol Header Checksum Source Read More
Role Based Access Control (RBAC)
The earliest forms of access control systems assigned privileges to users. These early access control systems allowed the system administrator to enable defined privileges for users like Bob and Doug. The addition of user groups improved that situation. The system administrator could now assign privileges to groups such as Sales or Accounting and add users into those groups. Role Based Access Control (RBAC) is the next evolutionary step in access control. Role Based Access Control (RBAC) enables privileges to be assigned to arbitrary roles. Those roles can then be assigned Read More
How Firewall Protection Works
Firewall protection works by blocking certain types of traffic between a source and a destination. All network traffic has a source, a destination, and a protocol. This protocol is usually TCP, UDP, or ICMP. If this protocol is TCP or UDP, there is a source port and a destination port. Most often the source port is a random port and the destination port is a well-known port number. For example, the destination port for HTTP is 80 and the destination port for DNS is 53. If the protocol is ICMP, Read More
ISAKMP
ISAKMP (Internet Security Association and Key Management Protocol) is a protocol for establishing Security Associations (SA) and cryptographic keys in a internet environment. ISAKMP defines the procedures for authenticating a communicating peer, creation and management of Security Associations, key generation techniques, and threat mitigation (e.g. denial of service and replay attacks). ISAKMP typically utilizes IKE for key exchange, although other methods can be implemented. ISAKMP is documented in RFC 2048: Internet Security Association and Key Management Protocol (ISAKMP). ISAKMP under IP (Internet Protocol) is documented in RFC 2407: The Internet Read More
Network Attacks
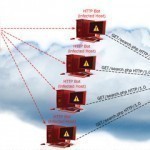
Understanding Network Attacks A network attack can be defined as any method, process, or means used to maliciously attempt to compromise network security. There are a number of reasons that an individual(s) would want to attack corporate networks. The individuals performing network attacks are commonly referred to as network attackers, hackers, or crackers. A few different types of malicious activities that network attackers and hackers perform are summarized here: Illegally using user accounts and privileges Stealing hardware Stealing software Running code to damage systems Running code to damage and corrupt Read More
IPsec
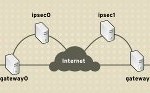
IPSec (IP Security) is a suite of protocols which was designed by Internet Engineering Task Force (IETF) to protect data by signing and encrypting data before it is transmitted over public networks. The IETF Request for Comments (RFCs) 2401-2409 defines the IPSec protocols with regard to security protocols, security associations and key management, and authentication and encryption algorithms. IPSec is a framework of open standards for encrypting TCP/IP traffic within networking environments. IPSec works by encrypting the information contained in IP datagrams through encapsulating. This in turn provides network level Read More
Firewalls
A firewall is a software component that restricts unauthorized inward network access. It allows outward information flow. It is set up to control traffic flow between two networks by configured permissions like Allow, Deny, Block, Encrypt, etc. It is normally employed to avoid illegal access to personal computers or corporate networks from external unsafe entities like the Internet. The firewall scrutinizes all the information flowing in and out of the network. If some data do not meet the necessary criterion, it is denied access into the network. A firewall’s key Read More
VPN (Virtual Private Network)
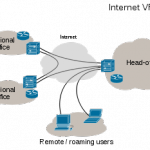
VPN A VPN (virtual private network) gives the end-user a secure means of connecting to a remote network over a remote or public Internet connection. The remote network can either be a private LAN such as those used at businesses, schools, the home, or one providing remote services to the user. The best way to conceptualize a VPN is that it creates a virtual tunnel through the Internet to the private network resource(s) located at the opposite end of the connection. The network traffic over the VPN is encrypted providing Read More
RADIUS Server
RADIUS (Remote Authentication Dial In User Service) is a system procedure that offers centralized entrance, approval, as well as accounting administration for individuals or computers to add and utilize a network service. Individuals often need “Authentication” when they try to fix to a network. People have to face far more problems while connecting their computers to a telecommunication network. For example, the telco wants to know the computer operator. When the identification is given, it may ask what services the user prefers. Plus, at that moment, the telco collects billing Read More


Share on: