The Bonjour service is an Apple, Inc. implementation of a service discovery protocol. It permits an application to find devices, services, and other computers on a network without configuring a DNS server or directory service by making use of the multi-cast network protocol. Although Bonjour started as a proprietary Apple networking protocol, the company has submitted a draft specification in order to be considered an International standard. Since early 2010, Bonjour has been bundled with iTunes and various Adobe software packages designed for the Windows Operating System (OS). Since that Read More
TL1 (Transaction Language 1)
TL1 (Transaction Language 1) is an element management protocol used primarily in the telecommunications industry. TL1 was designed by Bellcore (now Telecordia) in 1984 for use with its OSS (Operations Support System), NMA. TL1 is an MML (Man Machine Language), which means that TL1 messages should be readable and writeable by humans as well as machines. TL1 provides a CLI (Command Line Interface) to enable a user to a control a Network Elements (NE’s). TL1 also provides Network Elements with the capability of sending events to an OSS or Enterprise Read More
Plenum Cable
The plenum is hidden space within a building which is used for HVAC (Heating, Ventilation, and Air Conditioning) and to run cables. Plenum space is normally above a suspended ceiling or under a raised floor. Buildings without plenum spaces will have cabling and HVAC ducts within plain view. The plenum space is normally used to accommodate the communication wires for the building's computer and telephone network. Recent studies have shown that wiring and cabling within the plenum space could be dangerous and be exposed to fire/burning possibilities. Plenum cable is Read More
The Certificate Enrollment Process
While encryption can be a robust security technology, users have to implement a public key infrastructure (PKI) to make it beneficial and trusted within an organization. The Windows 2000 and Windows Server 2003 PKI implementation resides in Certificate Services. A public key infrastructure is the collection of technology, protocols, services, standards, and policies that control the issuing and management of public and private keys using digital certificates. Certificates are the core of the PKI. Encryption is used to protect data messages as they are transmitted over the network and digital Read More
Bluetooth Mouse – Advantages and Disadvantages

Bluetooth technology has become commonplace in modern society and has expanded the ways in which people communicate with each other. Bluetooth has allowed for drivers to talk on the phone without using their hands, teenagers to listen to music without plugging their headphones into their MP3 players, and computer users to be more mobile by using bluetooth keyboards and mice. While the rest of these devices have shown great progress and innovation, this article will focus specifically on bluetooth mice and show the advantages and disadvantages of owning such a Read More
Why is My Computer So Slow?
Your computer may have slowed down its execution speed below the expectation due to various reasons and complications. If your computer is running slower than usual and you are considering it to be inspected by a computer repair expert and spending money on getting your computer back to its normal level of performance, you should read about the common causes that make a computer slow. While these issues may not be what's causing your computer to run slowly, there is a chance that you can repair your computer without spending Read More
Flame Effect
STEP 1: Create a new file at 72 dpi. Make a text box and type any text in thick font. STEP 2: Go to layer menu and click on flatten image as shown in the figure. STEP 3: Diffuse the image by the steps as shown below. This step can be used any number of times to diffuse the figure, in this particular case it has been done 3 times. STEP 4: Now blur the image as shown in the figure below. STEP 5: Again go to the filter menu Read More
PERL Tutorials
Installing a Perl Script Tutorial This tutorial will show you how to install a simple Perl script and how you can use it on your website. To learn more on how to get a Perl script installed and running, you can use the sample simple script in the tutorial. Upon running it, it will produce a website with some simple text on it. Perl Variables Tutorial This is a tutorial that will teach you how to declare variables in Perl. It will also tell you how to use them in Read More
What is Interferometry?
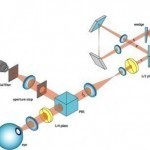
Interferometry is a series of techniques that uses a series of superimposed electromagnetic waves to extract data and other insights regarding the waves. The device used to measure the waves is an interferometer. Interferometry is primarily used in the fields of fiber optics, engineering metrology, optical metrology, seismology, oceanography, astronomy, particle and nuclear physics, quantum mechanics, bio-molecular interactions, and remote sensing. How does Interferometry Work? Interferometry provides a high resolution depiction of the spatial relationships for specified wavelengths. Two or more radio antenna that a known distance separates collect electromagnetic Read More
What does URL Stand For?

What is a URL? Uniform Resource Locator (URL) forms part of the Uniform Resource Identifier (URI) and serves as a pointer to where resources are located and the procedure to fetch them. In layman terms, URL is termed as a Web Address. Any link to a file or resource within a website can also be termed as a URL. These links can be any web page within the web site, image file, Java applet, form and so on. The actual URL of a website would be in binary form, but Read More


Share on: