An Introduction to the Active Directory Features With the release of Microsoft Windows Server 2003 quite a few enhancements and features were introduced that were not previously available in Windows 2000. These enhancements were aimed at improving the scalability, efficiency, speed and performance of Active Directory, and addressed a few deficiencies or shortcomings of the earlier version of Active Directory utilized in Windows 2000 Server. When a domain controller running Windows Server 2003 is created, a number of Active Directory basic features are immediately installed and available to the Windows Read More
The Red Ring of Death

The Red Ring of Death is the term that was given to the red ring that appeared where the green lights should be on the front of Microsoft’s X-Box 360. It is called the Red Ring of Death because its presence meant that the machine was about to fail. Every gamer dreads this. Microsoft has taken the problem into consideration and has since released a new 360 that prevents this from occurring. Fundamentally, overheating causes the red ring of death. The 360 is inefficient where cooling is concerned. Therefore, if Read More
Preprocessor Directives
The C++ preprocessor is a program that is executed before the source code is compiled. A preprocessor command is called directives. It begins with a hash symbol (#). No white space should appear before the # and a semi colon is not required at the end of the statement. Things that can be done during the preprocessing stage are: Inclusion of the header file through #include directive Definition of a symbolic constant and macros through #define directive The #define preprocessor allows us to define symbolic names and constants. For example: Read More
Widescreen TVs
Widescreen TV's are TV sets that have a screen format that are wider than standard TV sets. The normal widescreen format is an aspect ratio of 16:9. This is the same aspect ratio of films shown in most cinemas and widescreens allow the viewer at home to watch movies in their original format. A widescreen TV refers to the shape of a screen. Most standard TV's produce an image that has an aspect ratio of 4:3; this aspect ratio is similar to that of a square. Widescreen TV's are shaped Read More
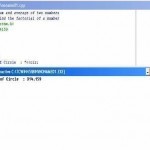
Windows Networking
Setting up a network of Windows computers is no longer a task that requires an Information Technology (IT) professional. A home network allows you to have a common printer for many computers, share removal drives, play multi-player games, store a single copy of files on a central server, and share a internet connection – the most common task. When setting up a home network, the central host computer should be running the newest version of Windows (normally the most powerful in a common household). Steps to Setting Up a Windows Read More
How to Connect SCSI to USB
Computer wire connections have been redefined and reset with the emergence of the universal serial bus or USB. Nowadays, almost all modern computers are equipped with USB terminals. Consumers or new computer buyers should always make sure that the personal computer units they will be purchasing have USB terminals. That is because almost all wires and memory storage gadgets that must be plugged into the PC have USB capabilities. The SCSI or small computer system interface wiring systems are not yet obsolete but most computer users simply prefer the USB Read More
Configuring Remote Access Servers
Installing and Configuring RRAS as a VPN Server How to install the Routing and Remote Access Services (RRAS) Click Start, and then click Manage Your Server. Select the Add or remove a role option. The Configure Your Server Wizard starts. On the Preliminary Steps page, click Next. A message appears, informing you that the Configure Your Server Wizard is detecting network settings and server information. When the Server Role page appears, select the Remote Access/VPN Server option and then click Next. On the Summary of Selections page, click Next. The Read More
Tabjacking

Tabjacking is a form of Internet threat. The tab feature in common Internet web browsers has paved a way for tabjackers to introduce malicious codes into user computers. Specifically, tabjacking refers to hijacking or an incident where a web browser tab falls under the control of an external party and the new tab is brought to a webpage that the external party is supporting or marketing. The controller of the code could also bombard the user with annoying advertising popups, and even worms, trojans and other parasites. The Tabs Feature Read More
HSL (Hue, Saturation, and Lightness)

HSL (Hue, Saturation, and Lightness) is a method for describing colors. HSL is also known by the abbreviations of HLS and HIS, while the L can often refer to luminosity or luminance rather than light. The HLS color model is graphically represented by a double cone or hexcone, this shape resembles a spinning top. The top and bottom ends of the cone, also called apexes, are the colors black and white. In this model, the hue is represented by the angular perimeter. The S part of HSL is graphically viewed Read More
How to Save Emails

In a basic email system, incoming and/or read emails are automatically saved onto the user’s browser-based email account. These messages can be accessed from any browser in the world. To access old emails offline, however, the user must download and install an email client and then download his/her emails to that client. This is relatively easy to do and there are a number of email clients that users can choose from. To make the selection easier, several free, cross-platform email clients are listed below. Mozilla Thunderbird Mozilla Thunderbird is a Read More


Share on: