A Call Center Software is generally an end-to-end software solution for customer support, service and satisfaction. Such software are used by enterprises and companies to provide quality assistance to their customers. It also helps automate the entire call center process, in turn improving speed, quality, performance and productivity. Call Centers are broadly classified as Inbound and Outbound. Inbound Call Centers receive calls and support tickets from customers and are focused on servicing. Outbound Call Centers make calls to potential and existing customers and are focused on marketing and sales. Both, Read More
How to Launch Yahoo Messenger
Yahoo Messenger is an instant messaging software provided by the popular search engine company, Yahoo. Yahoo Messenger allows users to communicate with each other via instant messages, SMS messages, and emails. Yahoo Messenger also allows users to view each other’s Yahoo profiles and share files. Although there are some slight differences, Yahoo Messenger is available as both a desktop instant messaging software of the same name and a browser-based messenger called Yahoo Web Messenger. How To Launch Yahoo Messenger Users can launch Yahoo Messenger by downloading and installing the Read More
IrDA
IRDA, or Infrared Data Association, is an organization that creates standards for two-way, interoperable, infrared devices. IRDA devices differ from regular infrared devices, such as remote controls and infrared computer mice, because they are able to receive data as well as transmit it. However, IRDA technology can be found in a wide variety of electronics, such as digital cameras, MP3 players, smartphones, and HPC devices. IRDA technology allows these devices to wirelessly share data fast with personal computers in either direction, but requires a direct line-of-sight between the two devices. Read More
Spreadsheet Software
Spreadsheet software is very important in the modern world of records and organization. Spreadsheet software allows users to make lists, organize budgets, perform calculations, and much more. While not all spreadsheet software is the same, the general goal is to provide the user with a simplified way of organizing and presenting information. This article will list a number of free spreadsheet programs that users can use to increase business, educational, and personal organization. Microsoft Excel Microsoft Excel is, perhaps, the most widely used spreadsheet software in the world. Microsoft Excel Read More
Linear Queue
Implementation of operations on a linear queue: Creating an Empty Queue Before we can use a queue, it must be created. The purpose of initializing the queue is served by assigning -1 (as a sentinel value) to the front and rear variables. Note that the valid range of an index for the array is 0 to CAPACITY-1. .cf { font-family: Lucida Console; font-size: 9pt; color: black; background: white; } .cl { margin: 0px; } .cb1 { color: green; } .cb2 { color: blue; } .cb3 { color: maroon; } void Read More
Telephone Tone Frequencies
The Low Tone is a generic tone used with various interruption patterns for the specific tones listed below: Line Busy Tone Reorder Reverting Tone No Circuit Tone No Such Number Vacant Code Group Busy Tone Deposit Coin Tone Vacant Position Tone Dial Off-Normal Tone Trouble Tone Dial Jack Tone Dial Test Signal Class of Service Low Tone is 480 Hz and 620 Hz at -24 dBm0/frequency. On some systems manufactured before 1974, Low Tone was 600 Hz modulated at 120, 133, 140, or 160 Hz at 61 – 71 dBrnC. Read More
Kinetic Hydropower
Kinetic hyrdopower is power created by using turbines under water to collect energy. However, unlike hydrodams that are large, bulky and often times a danger to the ecosystem, kinetic hydropower is an effective way of creating electricity without putting too much of a footprint on the area in which the turbines are installed. How Does Kinetic Hydropower Work? By harnessing the power of the moving water, underwater turbines that are grouped together are able to spin and, with the continuous momentum provided by the water, generate electricity. To make it Read More
Symmetric and Asymmetric ciphers
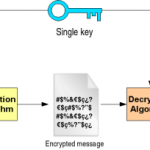
In a symmetric cipher, both parties must use the same key for encryption and decryption. This means that the encryption key must be shared between the two parties before any messages can be decrypted. Symmetric systems are also known as shared secret systems or private key systems. Symmetric ciphers are significantly faster than asymmetric ciphers, but the requirements for key exchange make them difficult to use. In an asymmetric cipher, the encryption key and the decryption keys are separate. In an asymmetric system, each person has two keys. One key, Read More
The History of Satellite Television
In order to understand the history of satellite television, you first have to go all the way back to the 1950's during the space race between the USA and Russia. The first satellite to orbit the earth was Sputnik, launched by the Russians in 1957. It was 6 years later until the first communications satellite was launched. This satellite was developed by both large corporations and government entities. It was called Syncom II and flew in an orbit circling 22,300 miles over the Atlantic Ocean. Using this satellite, the first Read More
Encrypting File System (EFS)
An Overview of EFS Encrypting File System (EFS) enables users to encrypt files and folders, and entire data drives on NTFS formatted volumes. NTFS enables you to set permissions on files and folders on an NTFS formatted volume which controls access to these files and folders. EFS enables you to encrypt files and folders to further enhance the security of these files and folders. Even when an unauthorized person manages to access the files and folders because of incorrectly configured NTFS permissions, the files and folders would be encrypted! Only Read More


Share on: