HTML stands for Hypertext Markup Language, and is used to describe the visual appearance of a document to be displayed by a internet browser. HTML documents consist of document tags which act to directly describe the visual appearance of a web page or to provide a directive command such as inserting imagery or a link to another web page within a document. HTML documents are saved in text format and are designed to be viewed or edited on any operating system that is able to connect to the Internet. XHTML Read More
Convert Meters to Feet
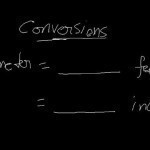
Convert Meters to Feet Automatically To Convert Meters to Feet, enter the number of meters to be converted into the meters box below. Meters: Meters (m) Results: Inches (in) 0 Feet (ft) 0 Yards (yd) 0 Rods (rd) 0 Miles (mi) 0 Micrometers (µm) 0 Millimeters (mm) 0 Centimeters (cm) 0 Kilometers (km) 0 Convert Meters to Feet Manually This chart allows users to convert Meters to Feet manually. For example, the chart below shows that 3 meters are equal to 9 feet and 10 inches. Meters Feet (decimal) Feet Read More
Why my Floppy Drive is being Accessed?

Most of us are using Windows PCs and sometimes some of your get into a situation where your floppy drive is randomly accessed every few minutes even though it has no floppy drive inserted. This is not dangerous for a computer system but is off course annoying to almost everyone. This occurs when some program (You are running on your computer, it could be any) considers that something should be written (or backed up) on a diskette. One of the cases, there can be a document in your recent history Read More
EVDO (EVolution-Data Optimized)
EVDO is an acronym for "Evolution Data Only" or "Evolution Data Optimized" which is a standard for high speed wireless networks used for Broadband Internet connectivity. EVDO enables computer users to have high speed Internet access without the help of a hotspot. Just by inserting an EVDO card into the computer, users get connected to the Internet within seconds and have Net access at DSL-compatible speeds. While traditional wireless networks assign a dedicated path between the source and destination for the entire duration of the call very similar to fixed-line Read More
Computer Crime Laws

The trouble with the current legal situation is that we the people are consistently electing moronic legislators who are ruining the country by trying to save it. We now have so many laws, no normal human can know them all — much less follow them all. In 1748, Montesquieu wrote in De L’Esprit des Lois “Useless laws weaken the necessary laws.” Today, we have so many useless laws that the government and police do not have the resources to enforce the necessary laws. The accepted solution, of course, is to Read More
Functions – Pass by value
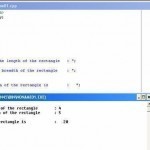
Functions A function is a named unit of a group of program statements. This unit can be invoked from other parts of the program. A programmer can solve a simple problem in C++ with a single function. Difficult and complex problems can be decomposed into sub-problems, each of which can be either coded directly or further decomposed. Decomposing difficult problems, until they are directly code-able as single C++ functions, is a software engineering method of stepwise refinement. These functions are combined into other functions and are ultimately used in main() Read More
Pirate Radio
Pirate radio is broadcasting outside of the rules laid down by the Federal Communications Commission (FCC). Pirate radio usually occurs on the FM band because that is where the most receivers are. Under Part 15 of the FCC rules, you can legally broadcast on the FM band if you broadcast using less that 100 milliwatts of output power and and antenna less than 3' long. In contrast, commercial FM broadcasters are required to broadcast using at least 100 watts of output power. 100 milliwatts will give your signal an effective Read More
How Does RAR Password Recovery work?

RAR Password Recovery is a password recovery software that is specifically designed to recover lost passwords for RAR and ZIP files. RAR Password Recovery is available from a number of sources and is available in both trial and full versions, although the trial version only allows users to recover passwords that are three characters long. RAR Password Recovery does not work with any other type of file, but is ideal for anyone who needs to recover a lost RAR o ZIP password. How RAR Password Recovery Works RAR Password Read More
Java Package
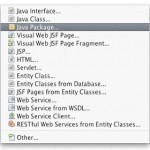
A Java package is a set of classes which are grouped together. This grouping helps to organize Java classes and codevent multiple Java classes with the same name. Using Java Packages To use a package in your Java source code, you must either import the package or use the fully qualified class name each time you use a class. Using Fully Qualified Class Names This example uses the Ammunition class from the ballistics package: ballistics.Ammunition caliber = new ballistics.Ammunition(); As you can imagine, using fully qualified class names can become Read More
How to Use an iPad

An iPad is a device similar to the iPhone that serves as a touch screen laptop. iPads are very sleek and portable, allowing the user to take the device virtually anywhere he/she goes. They include features from a wide variety of other Apple products such as iTunes, iBooks, and the Safari web browser. Because iPads are new to the market, many users are overwhelmed and do not understand the full functionality of the device they have purchased. In order to facilitate the user’s understanding of the iPad, several of the Read More


Share on: