A stored procedure is, in simplest terms, a command. Stored procedures are used to perform a wide variety of tasks on a computer and can be pre-programmed with any number of parameters or variables. While stored procedures are always used to interact with a database, they can be used for many different applications, such as use in employee databases, restaurant or retail records, or even in regular websites. How a Stored Procedure Works A stored procedure can be created by using any standard programming language and database, such as Java Read More
How to Play DOS Games under Windows
MS-DOS (Microsoft Disk Operating System) has many enjoyable game software titles that may not be playable on Microsoft Windows without having a few changes made to their configuration. Try the following options in order to play a DOS based game on a Windows Operating System: Compatibility Settings In Windows, compatibility may be possible with some DOS titles. The process requires having the ability to install the DOS game from the install media or having the game files available to be launched through explorer. Go to the installation directory for the Read More
What Causes Earthquakes?
An earthquake is caused when two blocks or plates of the Earth slip past each other in the lateral, vertical, or a combination of directions in a sudden manner. Due to the large pressures that develop between the Earth’s plates along fault lines at the Earth’s surface, one of the bodies will eventually give way. This resulting movement results in one of the plates moving above or to the side of the other during the resulting earthquake. A common question that arises amongst students and the general public is what Read More
rtvscan.exe

The file rtvscan.exe is a legitimate part of the Symantec Internet Security Suite, which was developed by the same makers of the popular Norton-Anti Virus software. Its main purpose is to execute virus-scanning in real time conditions. This means it can scan every file that enters your system against possible security threats or virus infections. Thus, being “real-time” would signify that it can monitor all process activities, file accesses, and even the registry for any sign of virus activity. This process is not a harmful file. Even if there are Read More
Conference Call Center
A conference call center is a centralized location where an individual, small business or large corporation can go to conduct a conference call or to allow other parties to join a conference call or listen in to a conference call. A conference call is a telephone call in which more than one party can listen in to a telephone call or participate in a telephone call. Conference calls in which other parties join the call just to listen to the audio of the call and not to participate or interact Read More
Automated Meter Reading
Automated Meter Reading (AMR) refers to the technology used for automating collection of water and energy (electricity or gas) consumption data for the purposes of real-time billing and consumption analysis. At any given time, the AMR system gathers real-time data and transfers the information gathered to the central database through networking technology. Benefits of Automated Meter Reading The primary benefit of this technology is more accurate and precise measurement of water, electricity or gas consumption. Consumers will be billed the amount that exactly corresponds to what they have consumed. On Read More
Task Manager Has Been Disabled By Your Administrator
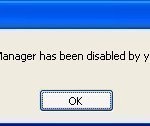
Computer malware has evolved at a rapid rate in recent years. A common trend among the fake anti-virus programs that the Trojan virus deploys on the Internet is disabling the computer’s Task Manager. The associated virus does this in order to make it more difficult to remove infections from computers. When this happens to a computer, the registry editor must be used to remove the malware. Depending on the nature of the computer infection and the configuration of the Windows computer, several methods can be used to repair the problem. Read More
D-Link Default Password

D-Link is a computer equipment brand that specializes in producing networking devices such as routers, modems, and network storage devices. D-Link routers, in particular, are often found in both residential and commercial environments and a wide variety of individuals use them to maximize the potential of their Internet access. D-link routers often contain two or more wireless antennas, WPA encryption, and multiple Ethernet ports. D-Link Default Password Like most wireless devices, all D-Link routers are equipped with a control panel that allows users to change their settings, configure the router Read More
Parallel Printer Cable
This cable can be used to connect a parallel printer to the parallel port on a PC. The phrase parallel cable can be ambigous as it shelters numerous different specifications, not all of which are simple PC to printer type. The parallel port socket on a computer uses 25 pins. There are two types of parallel printer cable that are widely used for PCs. The old "standard" IBM Printer cable and the newer IEEE 1284 bi-directional cable commonly sold today. 25 pin male connector 36 pin Centronics male connector Parallel Read More
Stem Cell Research
Stem cells have been widely publicized over the last decade as being the key to huge health breakthroughs. While only time will tell just how stem cells will be used in the future, millions of people around the world are either involved in stem cell research or closely monitor it for news of advances. What are Stem Cells? Stem cells are found in practically all multi-cellular organisms. Their defining characteristic is that they are able to renew themselves, usually through a process of mitotic cell division. Besides having the ability Read More


Share on: