A stent is a synthetic mesh tube used as a medical apparatus to support an open artery during surgery such as angioplasty. Stents are used in cases where arteries are weak, blocked or have become constricted. Insertion of stents into an artery enhances blood flow and averts the future constriction or blockage of the artery. Patients who have undergone a stent procedure must consume blood thinning medication such as Aspirin and Persantine, in order to decrease the threat of a blood clot forming in the stent. Such medication may have Read More
How to Show Hidden Folders
Hidden files and folders are those that the Windows Operating System (OS) keeps the user from seeing when navigating the file system with “My Computer” or “Windows Explorer.” The folders and files that are hidden by the OS will contain system files that should not normally be accessed or modified by the end-user. Unfortunately, a large amount of computer malware and spyware makes use of this feature of the Windows OS in order to hide their presence from the end-user. A common task that you may have arise as a Read More
ATSC (Advanced Television Systems Committee)
ATSC (Advanced Television Systems Committee) is a group which defines the standards for digital television transmission in the United States and many other counties. ATSC is the digital replacement for the earlier analog standard, NTSC. The ATSC standards are created by the Advanced Television Steering Committee, whose charter members are the Electronic Industries Association (EIA), the Institute of Electrical and Electronic Engineers (IEEE), the National Association of Broadcasters (NAB), the National Cable Television Association (NCTA), and the Society of Motion Picture and Television Engineers (SMPTE). The ATSC standards include high Read More
dBm

A dBm is a standard unit for measuring levels of power in relation to a 1 milliwatt reference signal. dBm is similar to dB, or decibel, except that where dB is relative to the power of the input signal, dBm always relates to a 1 milliwatt signal. In other words, dB is a relative measurement and dBm is an absolute measurement. A minus sign before the dBm indicates a loss and a plus sign or no sign at all before the dBm indicates a gain. The dBm Formula The dBm Read More
How to Remove Malware

New computer malware is discovered daily on the Internet. As computer security companies successfully combat emerging threats, computer virus authors grow more creative in designing attacks that take advantage of the many computer users that have not taken appropriate security measures or updated anti-virus software to defend against new attacks. Once a computer is infected, the infection should be removed as quickly as possible in order to prevent additional malware from being installed, making recovery more difficult. How to Remove Malware Step 1 – Download the Bleeping Computer, RKill application, Read More
What Generation is my iPod Touch?
All generations of the iPod Touch feature a 3.5-inch (diagonal) touchscreen. The first and second generation of the iPod Touch is available in 8 GB, 16 GB and 32 GB sizes. The third generation of iPod Touch is available in 32 GB and 64 GB sizes. Immediately, this tells you that if you have a 64GB iPod Touch, it is third-generation. How to Tell if your iPod Touch is First-Generation The first-generation iPod Touch is identifiable by its antennae cover, on the back of the device. If your device has Read More
Anonymous Surfing

Anonymous browsing is simply browsing the World Wide Web with most of one’s identity hidden. This is primarily done through what is known as an anonymous browser based proxy. These websites hide information such as the computer’s location and IP address when users use them to browse the web. For example, when the user tries to access something on a certain part of the web, the proxy will talk to that file as the user’s ambassador, maintaining the user’s privacy. The practice of anonymous browsing can also maintain the user’s Read More
How to Uninstall Hotbar

The HotBar add-on is an add-on program for Internet Explorer that personalizes email, as well as the functionality and visual appearance of browser applications. While performing the functions noted above, HotBar also makes multiple connections with “hotbar.com” and “reports.shopperreports.com”. Hotbar also monitors phrases the user enters into search engines and reports them to third parties in order to allow the user to be targeted by embedded ads, as well as targeted pop-ups. HotBar also disables certain pop-up blockers, and due to increased computational processes, slows browser speed and overall system Read More
Molality

Molality is the number of moles in a solute per kilogram of solvent. It is often confused with the term molarity, which is an alternative unit for concentration that measures the number of moles of solute per liter of solution. Molality is commonly used when experiments require significant temperature changes. This is because a solute’s molality remains the same with increasing temperature, since it is based on mass instead of volume, unlike molarity. How to Calculate Molality Step 1 – Divide the solute mass by the solute’s molecular weight. E.g. Read More
Spoolsv.exe Error
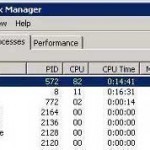
The Spoolsv.exe file is an executable program that runs the printing processes on a computer using the Windows Operating System (OS). The program normally runs in the background on most computers and the user should leave it in this state unless he/she determines that the file is the source of system problems on the computer. If the file is closed, it will display an error that states: “Spoolsv.exe – Application Error. The memory could not be written. The instruction at “0x77fcc2co” referenced memory at “0x00000000.” Computer malware infections cause many Read More


Share on: