The different nuclear processes will use different types of fuel. In general terms: Fission reactions will use fissile heavy elements Fusion will use fusible light elements The convection point is iron. Elements heavier that iron will have higher mass than its parts and yield energy when they break apart. Lighter elements that iron will have less mass than its parts giving away energy when they fusion. Very unstable substances will not be useful, they need to be stable under normal conditions but become unstable when bombarded with neutrons. Special isotopes Read More
User Authentication in IIS
Authenticating users in IIS is one of the initial steps in securing IIS. When a user attempts to access a website or an FTP site on an IIS machine, authentication is the process that verifies whether the user can indeed access the site. Authentication and permissions are closely coupled. After a user is authenticated, NTFS permissions determine whether the user can access folders and files and Web permissions indicate whether a Web or FTP client can read the website’s home or virtual directory. The authentication methods that authenticate users in Read More
How to Upgrade a CPU
You can upgrade an older microprocessor to a newer one in easy steps. Before going ahead, you should gather information about which new CPU you need and whether your motherboard is compatible with it or not. The compatibility of your new CPU with your motherboard can be ascertained by searching for specific information on the Internet, or checking with your trusted computer dealer. Preparing to Upgrade to a New CPU After purchasing the correct new CPU, make sure that adequate grounding is available before starting to replace the old CPU. Read More
IIR Filter
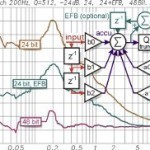
An IIR (Infinite Impulse Response) filter is a foundation element in Digital Signal Processing (DSP). It is one of two types of digital filters used in DSP applications and is an alternative to Finite Impulse Response (FIR) filters. The response in IIRs is considered infinite since there is feedback in the filter and they may be either analog or digital. IIRs are more efficient than FIRs for narrow transition bands, but it takes more time and money to develop a new IIR filter depending on the application. What are the Read More
VRRP (Virtual Router Redundancy Protocol)
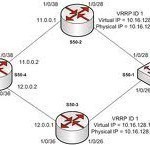
VRRP stands for Virtual Router Redundancy Protocol. The VRRP is a commonly used method to avoid network outages during important data transfers. Data transfer can be highly susceptible to failure when sent by a single router network. To combat this problem, VRRP creates a virtual connection between routers within the same network and ties them together. If the initial router used to send the data fails for any reason, another router automatically takes over the transfer. Is the VRRP a physical router? No. The VRRP is, as the name indicates, Read More
Reverse DNS
Reverse DNS is the process of using DNS to translate IP addresses to hostnames. It is the opposite of forward DNS, which is used to translate hostnames to IP addresses. Internet names are those used to refer to hosts on the Internet, such as www.byteguide.com and www.freebsd.org. IP addresses are the numbers that Internet routers use to move traffic across the Internet, such as 216.17.138.115 and 216.136.204.117. Reverse DNS Lookups One of the best ways to understand reverse DNS is to use the DNS testing tool, `nslookup` to do a Read More
How to Change a Facebook Layout
Changing a Facebook layout at the moment is only possible through single sided, third party applications. Most of the services that allow this only work on the user’s side and no one else is able to see any of the changes that have been made. It is important to note that a majority of the Facebook layout services take the form of spyware/adware, which generally make them bad for computer systems. The other problem with these limited Facebook layout services is the fact that they do not work on all Read More
How to Disable Mac OSx Firmware Password Protection
Launch the Open Firmware Password Application. Click the authentication icon and enter your Administrator credentials. You will be prompted for a password. Locate and click the Change button. This will launch an Open Firmware Password window. In the Open Firmware Password window, locate and click to deselect/uncheck the “Require password to change Open Firmware settings” option. Click the OK button to commit your changes. Locate and re-select the lock icon.
Brute Force Attack

A brute force attack consists of trying every possible code, combination, or password until the right one is found. Determining the Difficulty of a Brute Force Attack The difficulty of a brute force attack depends on several factors, such as: How long can the key be? How many possible values can each key component have? How long will it take to attempt each key? Is there a mechanism that will lock the attacker out after a number of failed attempts? As an example, imagine a system that only allows 4 Read More
Laser Sight
A laser sight is a device that shoots a laser at a certain target. It is often used within many military applications, especially with guns. Basically, the laser sight is a visible laser light that allows the shooter to see where the bullet will hit. It is located (or structured to fit) above the body of the small arm at a precise angle facing down, so that the laser will point directly at the spot where the bullet will most likely hit. However, as with all devices, the laser is Read More


Share on: