While Vista is the most up to date operating system from Microsoft, many in the private and business sectors are less-than-pleased with its reliability, features and performance. For many, Windows XP has been a reliable, safe operating system to use offering enhanced performance and compatibility with the vast majority of network components and software. If you bought Windows Vista and installed it on a computer that once had XP and are now unsatisfied with the results, here are some tips on how to replace Vista with XP. Replacing Vista with Read More
How to Use a Flash Drive

Using a flash drive is a simple process that requires access to a computer and an understanding of how to drag a file from one folder to another. Once that is done, files are on a flash drive. So long as the computer is working and the files aren’t corrupted, they’ll transfer over in a few seconds per file. On top of that, depending on the size of the file will determine how many can fit on the flash drive. The first step in using a flash drive is to Read More
MPLS (Multi Protocol Label Switching)
MPLS stands for Multi Protocol Label Switching. The MPLS is often referred to as the layer in between the Data Link and Network layers because of where it operates. The MPLS serves as a method to forward packets of data easily by using labels. What are the Data Link and Network layers? In the seven-layer OSI model, a model used to explain how a computer operates and communicates within itself. The Data Link and Network Layers are parts of this model, and correspond to the second and third layers respectively. Read More
How to Monitor CPU Temperature
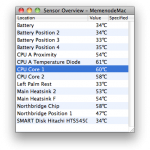
Excessive heat damages electronics. Monitoring CPU and other computer components’ temperature help them run properly. To make the most of monitoring software, users must ensure that ACPI functionality is enabled in their motherboard BIOS. Why CPU Temperature is so Important When the first affordable PCs were offered to the general public in the early 80’s, system engineers and designers took into consideration the heat that system components emitted and ensured that their case and cooling designs handled the appropriate amount of heat so system damage or instability was rarely an Read More
How Does WiFi Work?

Over the past decade, WiFi/wireless networking has become very popular. Low cost and simplicity are some of the reasons why WiFi is so popular. Today, it is almost impossible to buy a laptop that doesn’t have a wireless card built into the screen, which is why WiFi’s popularity continues to grow. What Does WiFi Stand For? WiFi refers to the 802.11 wireless networking standard that is promulgated by the IEEE. Every time a standard is updated, a new letter is added to the end of the designation. This normally equates to an Read More
502 Proxy Error
A 502 proxy error message is normally sent from the Internet to a computer through a proxy server. Internet Security and Acceleration (ISA) set up proxy errors to help protect networks from external and internal web-based threats. Computer users who encounter the 502 proxy error commonly face the problem of determining whether it was generated correctly or as a result of outdated software or server misconfiguration. When does the 502 Proxy Error Occur? A 502 proxy error may occur if the ISA Server site and content rule are configured to Read More
How to Measure Signal Quality
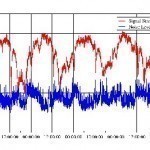
Most people usually look to Signal to Noise Ratio to measure the signal quality of either audio or video communications. Signal to noise ratio is usually written either S/N or SNR. Most of the time the signal to noise ratio is measured in decibels. A decibel is a measure of power or loudness. Not to get too technical, Signal to Noise Ratio is a great way to easily determine which audio or video component produces a clearer signal or can transfer a clearer signal to a speaker, TV set or Read More
What is SIP Trunking?
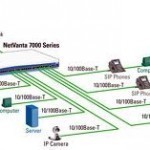
Some ITSPs (Internet Telephony Service Providers) offer a service called an SIP trunk, which allows PBX services to use VoIP (Voice-over-IP) services outside of the enterprise network via the same connection as that used for the Internet. As a result, SIP trunking services can save an organization a significant amount of money as it eliminates the need for additional VoIP hardware or software for the organization’s network. The minimum equipment required to use SIP trunking is a PBX, ITSP, and an edge device for coordinating the routing of SIP traffic. Read More
How to Enable Autologon in Windows Vista
Login process Login is the process in which end-user or personal access to a computer is managed by the detection of user provided credentials. A user can access a computer by providing a username and password which is then verified by Windows User Accounts. In case of network login, the user name and password is verified by Windows Authentication. Users can then log out of the computer, once access is no longer needed. The log out process ensures that unauthorized users do not have access to the computer, which prevents Read More
Free Forum Software
Forum software is a type of software that allows users to create and install a forum on his/her website. A forum is a type of online, community message board that users from all over the world can access in order to meet each other, share information, and support a similar cause. Forum software can include various functions and features depending on the particular program. Forum software can also vary on whether it can be installed automatically or if the user has to manually set it up on his/her website. This Read More


Share on: