Authentication in IIS Authentication in IIS verifies whether a user attempting to access a particular website, can indeed access it. Authentication is the process that verifies whether the user can access the site which he/she is attempting to access. The authentication methods which can be used to authenticate users in IIS 6 are listed below. Each authentication method can be used to authenticate users attempting to access Web sites. However, only Anonymous access and Basic Authentication can be used as an authentication method for FTP sites. Anonymous access: This authentication Read More
How DLP Projectors Work
DLP (Digital Light Processing) projectors works in similar ways to a lot of other micro display devices. A high output lamp creates white light that is then sent onto a color wheel. This color wheel separates the three basic colors of light, red, blue and green. That light is then sent into a small computer chip, called the DMD (Digital Micromirror Device). From there the hundreds of thousands of tiny mirrors inside the DMD reflect the colors back out to the screen to create whatever image is being displayed. Since Read More
Magnetic Levitation Vehicles

A magnetic levitating vehicle (MagLev) is a vehicle that uses a strong electromagnetic field to resist gravity and keep the vehicle floating out of the ground. The technical name is Electromagnetic suspension. The principle of the Electromagnetic suspension is to charge with the same pole the base of the vehicle and the rail with a magnetic field strong enough as to generate a force stronger than the weight of the vehicle and have suspension. When and Where Was Maglev Invented? The first patent for a MagLev was granted in 1968 Read More
How to Use Net Send
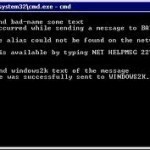
The Net Send command is used to send network messages to other computers, messaging names, or PC users on a computer network, or LAN. In order for the Net Send utility to work, the Windows Messenger service needs to be installed on the client computer and messages can only be sent to acknowledged names on the local network. If the targeted recipient of the message is not online or does not have Messenger services enabled, they will not receive the Net Send message. A common task for new users of Read More
Difference Between SD & SDHC Memory Cards

The Secure Digital (SD) memory card format was developed for portable devices across a wide range of product categories and is the unofficial industry standard for memory card format. SDHC is the high capacity variant of the memory card format. It has a slightly different communication protocol from the SD type and does not necessarily work on the same devices. Newer computing devices typically support both formats, however, older devices will not necessarily do so. Consumers often want to determine the differences between SD and SDHC memory cards. SD Memory Read More
Understanding the Department of Defense Network Model
Department of Defense Network (DoD) Network Model Introduction Back in 1960, systems were primarily made up of mainframe computers, and were typically owned by fairly large companies and government institutions. Because mainframe computers run different proprietary software, and due to mainframes not being able to communicate between each other, special code (interface) had to be defined so that one mainframe could interrelate with a another mainframe. When an operating system changed between the two mainframes that were exchanging data, the interface had to be rewritten so that the two mainframes Read More
SSID (Service Set IDentifier)
The SSID (Service Set IDentifier) is a token that identifies a 802.11 (Wi-Fi) network. The SSID is a key that the wireless network administrator sets. Users must know the SSID to connect to an 802.11 wireless network. However, network sniffing/scanning allows users to determine the SSID. By default, the SSID is part of the packet header for every packet sent over the WLAN. SSID access points continuously broadcast radio signals that enabled client machines receive. Based on the automatic or manual configuration, the client can connect to the access point. Read More
How to Decrypt Cisco Passwords
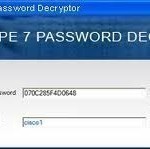
If ‘service password-encryption’ is not configured on the Cisco device, simply read the plain text passwords from the configuration file. If ‘service password-encryption’ is configured on the Cisco device, most of the passwords are encrypted with a weak encryption algorithm (Type 7) that is easy to decrypt. Once there is access to the Cisco configuration file, the passwords can be decrypted fairly easily. ‘service password-encryption’ is enabled using the following command: TopBits-Cisco (config)#service password-encryption Network administrators often store IOS configuration files on TFTP (Trivial File Transfer Protocol) servers. One server Read More
DMZ (DeMilitarized Zone)
DMZ is short for DeMilitarized Zone. In military jargon, a DMZ is an area of land that serves as a buffer between two enemies. The most well known DMZ in the world is the DMZ that protects South Korea from North Korea. In network security jargon, a DMZ is a network that serves as a buffer between a secure protected internal network and the insecure Internet. A DMZ usually contains servers which provide services to users from the Internet, such as web, ftp, email (SMTP, POP3 and IMAP4), and DNS Read More
Possible Defenses against Botnet Attacks
"Malicious botnets", networks of "zombie" computers controlled and commanded by outsiders with nefarious intentions ranging from Directed Denial of Service (DDoS) attacks to simple spamming and ad insertions are considered by Internet security experts as the major threat in the coming months and years. The Federal Bureau of Investigation (FBI) has recently announced that it has identified at least one million 'captive' computers in the United States. At the same time, various Internet security experts believe that there are anywhere from three to 35 million bots operating in the world-wide Read More


Share on: