Using the IP Security Monitor Snap-In to Monitor IPSec The IP Security Monitor snap-in, a new feature in Windows Server 2003, can be used to monitor and troubleshoot IPSec activity. The IP Security Monitor snap-in provides enhanced IPSec security monitoring. As long as the IPSec policy is active, you can monitor how the IPSec policy is functioning within your networking environment through the IP Security Monitor. The main administrative activities which you can perform through the IP Security Monitor snap-in are listed here: Customize the IP Security Monitor display. Monitor Read More
Service Management
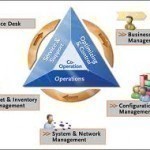
Service management, also called IT service management, is the discipline used in industries that provide services or a combination of goods and services. While widely used in the IT industry, specifically the ICT (information and Communication Technology) sector, service management can be integrated into many other industries. Service management is usually used in conjunction with operations support systems. Systems that use service management include order management, inventory management, activation, maintenance, performance diagnostics, and several other types of support systems to make sure that these systems are running proficiently and error Read More
How Do I Get My Songs on iTunes?
New users and those who have not yet used iTunes may have a difficult time getting their music into their iTunes library. The process is relatively simple and can be done in a variety of ways. The most common ways to transfer music to the iTunes library are: Songs from Music CD Music from CDs can be imported to iTunes with the handy features that iTunes software provides. Simply load a CD into the computer's CD reader and allow iTunes to locate it. Once it is located, the CD will Read More
Classes
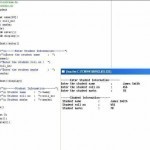
A class is an approach to bind the data, describing the entity or an object, and its associated functions together. In C++, a class creates a data-type that is used to create objects of that particular type. Class represents a group of similar objects. Example: class account { private: int accoutno; char type; float balance; public: float deposite(float amount) { balance += amount; return balance; } float withdraw(float amount) { balance -= amount; return balance; } }; In the above example, the data describing an account object (i.e. accountno, type Read More
What is a Field-Effect Transistor?

A field-effect transistor (FET) is a semi-conductive device that is used in integrated circuits to control the conductivity of a conductive channel. FETs are highly dependent on negative and positive charges. They have many purposes, including limiting a device’s power levels, storing data, and being used as a switch for a wide variety of electronic devices. Various FET designs have been presented and produced since 1925 and have collectively allowed modern electronics to be possible. How Field-Effect Transistors Work FETs are dependent on four essential components: the base, the source, Read More
How to Open a Simplex Lock

Simplex locks, now manufactured by Kaba Ilco, are simple push-button combination locks. Simplex locks are used to protect equipment rooms, labs, and FedEx-type boxes. Simplex locks are used whenever having a large number of keys would create logistical problems. Simplex Lock Combinations The Simplex lock would be a normal 5-button combination lock, except for one weakness. Each button on a Simplex lock may only be used once in a combination. A combination of 1-4-3-2 is acceptable. A combination of 1-4-3-1 will not work. This limits the Simplex lock to only Read More
Securing WINS Servers
WINS Server Role Security Issues A WINS server is an enhanced NetBIOS name server that can resolve NetBIOS computer names to IP addresses. The WINS database hosted on the WINS server is used to store and maintain NetBIOS computer names to IP addresses mappings. WINS registers NetBIOS computer names, and then stores these client name registrations in the WINS database. A WINS server is basically needed if there are applications that require WINS for name resolution to operate correctly. WINS is also typically needed if all your domains have not Read More
Ozone Generators

Ozone or O3, is a molecule similar to oxygen that is made up of three oxygen atoms. While ozone in the lower atmosphere is harmful to humans, plants, and animals, causing respiratory problems in humans and animals while burning some types of plants, ozone in the upper atmosphere, known as the “ozone layer”, is highly effective at preventing harmful electromagnetic radiation from the Sun and other stars from reaching the Earth. By doing this, ozone is responsible for limiting the effects of global warming. While ozone in the lower atmosphere Read More
Cloaking
Cloaking is a black hat SEO technique where one set of content is shown to human visitors and another set of content is shown to search engines. In cloaking, human visitors are shown the actual web page, but search engines are shown a web page which is full of spammy SEP techniques such as keyword stuffing. Cloaking by User Agent To effectively cloak a web page, the web server must be able to determine if the visitor is a human or a search engine. One technique for doing this is Read More
Error 0x0000007e
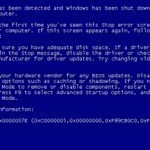
Error 0x0000007e is an error message that is displayed whenever a computer cannot access one of its hard drives, ports, optical drives, system files, or other critical components necessary to run the operating system. Usually, the computer’s error handler discovers these problems immediately upon booting from a device and will display a specific error message before the user is able to log in. However, if an exception occurs that prevents the error handler from discovering these problems immediately, it will display Error 0x0000007e after the computer has booted up and Read More


Share on: