Have you ever wondered how some wireless video camera recordings leaked through the Internet when virtually no one ever touched the device itself? Technology has ushered the use of video and audio interceptors alike to intercept just any type of wireless video-audio cameras in your immediate neighborhood, just in the turn of a dial. Using a Wireless Video Interceptor A wireless video interceptor is used by law enforcement agencies in order to determine if a specific location is being monitored through wireless intercepting devices present nearby. Such a device is Read More
How to Format an SD Card

Secure Digital (SD) memory cards are very simple to format. There are 3 main options to format the SD cards to the format needed. To successfully format an SD card, the write protection lock on the side of the card must be in the “unlock” position. SD mini and micro SD cards must be used with an adapter or specialized USB card reader when a computer is formatting them. The first option is to use a format utility. On most computer systems, there are generic formatting utilities available for nearly Read More
Error 0x800ccc79
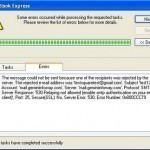
Error ox800ccc79 typically appears in Microsoft Outlook when messages are sent. The error message can also affect other messaging clients, regardless of the manufacturer. It usually states that the e-mail cannot be sent due to Simple Mail Transfer Protocol (SMTP) relay blocking. The message’s specific wording may vary, depending on the Internet Service Provider (ISP). These error messages are becoming more common because ISPs are starting to take action against SPAM. Many ISPs are blocking SPAM by requiring that each user be dialed directly to their system in order to Read More
The Peltier Effect
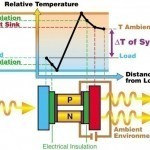
The Peltier effect is one of the three separately identified effects to which “Thermoelectric Effect” or simply, “Thermoelectricity” refers. The other two are the Seebeck and Thomson effects. Discovery This effect is named after French physicist Jean-Charles Peltier, who discovered it in 1834. Peltier found that the junctions of dissimilar metals were heated or cooled depending on the direction of electric current flow through them. The heat that the flow of current in one direction generated was absorbed if the direction of current was reversed. Peltier inadvertently discovered this while Read More
Do I Need a License to Use one of these Radios?

All radio spectrum is legislated or controlled. The FCC requires licenses to operate on some bands, and lets other frequency bands run unlicensed. Radio Services Which Require a License Some of the licensed radio services include: Acronym Full Name URL HAM Amateur http://wireless.fcc.gov/services/amateur/ GMRS General Mobile Radio Service http://wireless.fcc.gov/services/personal/generalmobile/ Radio Services Which Do Not Require a License Some of the unlicensed radio services include: Acronym Full Name URL CB Citizens Band http://wireless.fcc.gov/services/personal/cb/ FRS Family Radio Service http://wireless.fcc.gov/services/personal/family/ MURS Multi-Use Radio Service http://www.provide.net/~prsg/murs_faq.htm While unlicensed, there are still restrictions placed on Read More
Security Problems with SUID Scripts and Programs

There are many methods which have been used to gain root priviledges from a Unix SUID (Set User ID) script or program. It is the task of the programmer of the SUID script or program to prevent the hacker from gaining root access. Here are some methods which hackers utilize and which programmers should prevent: Changing IFS If the program calls any other programs using the system() function call, the hacker may be able to fool it by changing IFS. IFS is the Internal Field Separator that the shell uses Read More
MBR (Master Boot Record)
The MBR is the Master Boot Record. The MBR is a small program which runs whenever a computer boots up. The MBR is stored in the first sector of the boot disk. The boot disk may be a hard drive, a floppy drive, or even a CD or DVD drive. The Task of the MBR The normal job of the MBR program is to search the partition table for the active partition, copy the boot sector from the active partition into memory, and transfer control over to that program. If Read More
Where to get an Online Virus Scan
There are times when you do not want to download anti-virus software. These may include: Your computer is too infected or broken to install new software You are on someone elses computer and you don’t want to install software You just need to do a quick check, without the hassle of software installation The solution for virus scanning at those times is to utilize an online virus scanner. Note: Most online virus scanners require Internet Explorer with ActiveX enabled. Online Virus Scanners Trend Micro Housecall Trend Micro HouseCall thoroughly scans Read More
What is a Memory Card Reader?
A memory card reader is a device that acts as a connection between a flash memory stick or SD memory card and the computer. In other words, it is a memory hub that makes it possible to connect multiple memory cards to the computer at one time. Once the memory card is attached to the reader and the computer, the user can easily transfer files to and from the reader. Another reason that a memory card reader is beneficial is because it offers different size memory slots. Since there are Read More
Mashup
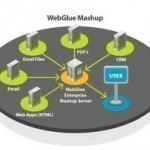
A mashup is anything that results from a combination of data from different sources. Mashups could be accessed and found across the World Wide Web. It is considered to be one of the new types of web content today – an indication of the Web 2.0 phenomenon. A mashup usually refers to the merging of two or more sets of content from different sources using a web application. A good example of a mashup site is the www.chicagocrime.org. This website is a result of the merging or “mashup” of Google Read More


Share on: