A direct carbon fuel cell is a cell that relies on a carbon based material as a fuel. Unlike other forms of producing energy, a carbon based fuel cell produces energy by mixing oxygen with some form of rich carbon which results in the creation of energy. The byproduct of the reaction that takes place in a direct carbon fuel cell is carbon dioxide. The reason direct carbon fuel cells are becoming the preferred method of energy creation is because it has an efficiency of 70%. While it is not Read More
How Video Conferencing Works
Video conferencing has become popular over the last decade. Video conferencing is when two or more parties communicate in real time in separate locations with both video and audio signals. Technology Used in Video Conferencing Video conferencing works by using a few different technologies. Some of these technologies are hardware, others technologies involved in the video conferencing process are software related. Here is a list of technologies that are common to a video conference set up. Video Input Video input usually consists of either a video camera or a web Read More
Java Servlet
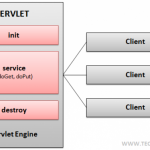
A Java Servlet is basically used to extend the functionality of a server. A Servlet is a Java programming language class. It is used commonly to expand the functionality of an application hosted on web server. A Java Servlet adheres to the Java Servlet API in Java EE. Java Servlet API is a protocol that defines how a server request is handled by a Java class. A Servlet is majorly used over the HTTP protocol; however it is also equipped to communicate over any client-server protocol. A programmer can create Read More
Understanding Internet Security and Acceleration Server (ISA Server)
Internet Security and Acceleration Server (ISA Server) Overview Microsoft Internet Security and Acceleration Server (ISA Server) is combination of a firewall and Web caching server that can be used to protect the enterprise from external access, while sharing a internet connection on the network. The multilayer firewall of ISA Server protects valuable network resources of the enterprise from unauthorized external access, attacks from hackers, and malicious viruses. You can also control client access to the Internet. The Web cache server enables faster Web access for users by serving objects locally Read More
MIC (Message Integrity Check)
MIC (Message Integrity Check) is part of a draft standard from IEEE 802.11i working group. The MIC (Message Integrity Check) is an additional 8 byte field which is placed between the data portion of an 802.11 (Wi-Fi) frame and the 4 byte ICV (Integrity Check Value). The MIC has a function very similar to the older ICV. However, the ICV only protects the packet payload. The MIC protects both the payload and the header. The algorithm which implements the MIC is known as Michael. Michael also implements a frame counter, Read More
What is Bioluminescence?

A living organism is bioluminescent when it produces and emits light. Most organisms that do this live in the sea. However, there are several land insects and plants that also have bioluminescent qualities, including the firefly. The trait has typically evolved in organisms that either need to communicate with each other or lure/detect prey. How does Bioluminescence Work? Light is created when an electron orbits an atom’s nucleus. When an electron receives enough energy to jump to a higher orbital shell then falls back to the lower shell, the resulting Read More
How to Dial a DSN Number
DSN stands for the Defense Switched Network which is a global phone service used by the United States government capable of both non-secure and secure communications. Traditionally, the DSN network has only been used for voice communications, but in the past decade data and video service have been incorporated into the network through Integrated Services Digital Network (ISDN) connections. Secure DSN phone calls are made through the combined use of a Secture Terminal Equipment (STE) or Secure Telephone Units (STUs). Although the U.S. Department of Defense (DoD) is the largest Read More
Implementing IAS
Internet Authentication Service (IAS) Overview In most organizations that have multiple network access servers, the centralization of authentication and accounting of connections being established at a centralized server is the better approach than each network access server performing authentication and accounting services. The Remote Authentication Dial-In User Service (RADIUS) protocol is the recognized protocol for providing a centralized authentication, accounting, authentication and authorization for remote network access. RADIUS is a internet Engineering Task Force (IETF) standard. Essentially, the RADIUS protocol can be used to control access for dial-up networks, VPNs Read More
SNMP (Simple Network Management Protocol)
Network management systems use SNMP (Simple Network Management Protocol) to communicate with network elements. For this to work, the network element must be equipped with an SNMP agent. Most professional grade network hardware comes with an SNMP agent built in. These agents must be enabled and configured to communicate with the network management system. Operating systems such as Unix and Windows can also be configured with SNMP agents. SNMP Messages Either the network management system (NMS) or the network element intitiates SNMP messages. An SNMP TRAP is a message that Read More
How to Remove MSN Messenger

MSN Messenger (Microsoft Network Messenger) is an instant messaging software that Microsoft developed that allows users to instantaneously communicate with friends, family, and co-workers. It is an extremely popular program that is used worldwide and performs many different communication tasks such as video conferencing, audio calls, file sharing, and remote assistance. Additionally, MSN Messenger includes dozens of built-in tools that allow users to change their font size, font style, and font color, as well as play games, insert emoticons, and meet new people. How MSN Messenger Works MSN Messenger Read More


Share on: