FLAC (Free Lossless Audio Codec) is an audio format similar to MP3, but it is a lossless encoding format, meaning that audio is compressed in FLAC without any loss in quality. FLAC is unique as it is the fastest and most widely supported lossless audio codec, and the only one that at once is non-proprietary, and is not patented. It has an open-source reference implementation, and is a well documented format and API, and has several other independent implementations. Being a lossless compression format, FLAC does not remove any data Read More
Device Drivers

Device drivers are simple software code that allows a higher level program on your computer such as an operating system to control a device. Today there are many peripherals for home computers and laptops such as printers, scanners, keyboards, etc. All of these devices require the operating system and sometimes other software programs that run on a computer access and control of a device. A device driver offers this access and ultimately makes the use of a device smooth and reliable. When you buy a peripheral device such as a Read More
Petabyte

A petabyte is a measurement unit that describes a piece of information that is equal to 1,000 terabytes or one quadrillion bytes of data. A single petabyte is equal to 1,000,000,000,000,000 bytes . When a petabyte describes computer memory, it is also used in reference to a corresponding power of 1024. The approved scientific symbol for the petabyte is PB. Pebibyte also describes a power of 1024 and is described through the symbol, PiB. Examples of Petabyte Use As computer data storage and network transmission capabilities continue to exceed the Read More
E-Voting
E-voting or electronic voting refers to any voting process where an electronic means is used for votes casting and results counting. E-voting methods include optical-scan voting systems, specialized voting systems like DRE or direct recording electronic voting systems, punch cards, national IDs, the Internet, computer networks, and telephony systems. Electronic voting is already in use in many countries all over the world and has proven to speed up the counting of votes as well as improve turnout among disabled voters. Several countries however have expressed concern over the possibility that Read More
Hard Disk Partition
A hard disk partition is a defined storage space on a hard drive. Most operating systems allow users to divide a hard disk into multiple partitions, in effect making one physical hard disk into several smaller logical hard disks. Reasons to Use Hard Disk Partitions A user may decide to split a hard disk into multiple partitions in order to organize his/her data more effectively. On Microsoft Windows machines, it is common to store the OS and applications on one hard disk partition and user data on another. When a Read More
How to Convert iTunes to MP3
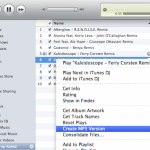
A large number of consumers have digital music purchased through or uploaded to the iTunes multimedia player on Mac and Windows computers. Unfortunately, the native iTunes format, AAC, for music files is not compatible with many non-Apple brands of MP-3 player. As a result, a common task that arises for end-users is to convert iTunes to MP3. How to Convert iTunes to MP3 Step 1 – Launch the iTunes application on your computer by double clicking the program icon on the computer’s desktop. Step 2 – Select the “Edit,” “Preferences,” Read More
Google Bomb
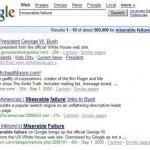
A Google bomb is when a group of people attempt to cause a target web page to become the #1 search result for a chosen search phrase. Every good Search Engine Optimization specialist tries to make his web pages become the #1 search result for the relevant search terms. A Google bomb is different, because it is usually a group of people trying to make a web page the #1 search result for an irrelevant or abusive search phrase. The leftist loons used a Google bomb to cause President Bush Read More
Implementing Account and Security Policies
Understanding Security Policy Types With Windows Server 2003, you can implement and manage security settings at the following levels: Local computer (local security policies) Active Directory site, domain, or organizational unit (domain security policies) Local security policies are managed through Local Computer Group Policy Objects (GPOs), and domain security policies are managed through Group Policy with the Active Directory Domain Controller GPOs. However, domain security policies override local security policies. In Windows Server 2003 Active Directory environments, group policies include configuration settings for the following: Software policies Scripts Security policies Read More
Implementing Windows Cluster Service
Planning for a Cluster Service Implementation A number of factors have to be determined when you plan for your Cluster Service implementation. A few items which you should include in your planning phase are listed here: Determine which applications and network services are the mission-critical applications of the organization that need high availability. Determine which clustering technology to implement that would ensure high levels of availability for the mission-critical applications previously identified. Here, you should identify those applications which should be used with Cluster Service, and those applications which should Read More
iPod Dock Connector
The iPod dock connector is the plug used to connect an iPod to its dock, just as the name implies. It was originally developed by JAE according to the iPod’s specifications. The first version of the iPod dock connector was made available with the third generation (3G) iPod. With the iPod dock connector, a large amount of functionality can be achieved. The dock connector can allow the iPod to be connected to USB or Firewire ports on a computer, to a stereo with the use of a line-out connector, or Read More


Share on: