The installation of an antenna starts with the analysis of few things that are decisive in ensuring reception quality. First you must decide which type of antenna will be used. Choosing the antenna type for the requirement is crucial, as the antenna used generally requires a specific antenna for the specific use. Next you must decide on antenna positioning. Selecting a position that provides the longest range and incurs the lease ambient noise is a key factor. It is generally considered best to place an antenna in a location that Read More
Ettercap
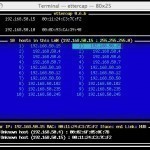
Ettercap is a network security tool that intercepts network traffic. Ettercap can be run from a wide variety of operating systems including Windows, Linux, Unix, Mac OS X, Solaris, and BSD. It is a completely free, open source and is one of the most used and recommended security programs in the world. Ettercap intercepts network traffic, performs eavesdropping operations, audits a network for security limitations, captures passwords, and even denies service to a specific user. How Ettercap Works Ettercap uses a technique known as “ARP poisoning” or “Address Resolution Protocol Read More
MP4
MP4 or MPEG-4 (Moving Picture Expert Group-4), first published in 1998, was designed to encompass all the features that were part of earlier releases of MPEG files and add a few more that would prove helpful with the advancing online technology of the day. As a standardized group of video and perceptual coding formats, MP in general quickly became a hit with the average Internet user. The introduction of MP4 made it possible for the audience to continue growing by providing quicker, faster, and higher quality broadcast media for the Read More
Error 0x80070052

Error 0x80070052 can occur when adding or accessing files on a USB flash drive. Although the error indicates that the drive is full or that files may not be created or saved, it can be triggered when the drive is not near capacity. The error is normally generated based on how the flash drive is formatted. When FAT or FAT16 format types are used to format a drive, there is a limitation on the total number of files or folders that can be saved on it despite its capacity to Read More
Acceptable Use Policy

An acceptable use policy is a set of rules applied by website owners and networks, created to restrict the ways in which the site or the network may be used. AUP documents are also used by universities, corporations, Internet Service Providers, and schools. The acceptable use policies are also integral parts of information security polices; it is a common practice to ask the new members of an organization to sign an AUP before giving them access to its information. And for this reason, an AUP have to be clear and Read More
How to Turn Off Automatic Updates
Automatic updates are a feature of the Windows Operating System (OS)designed to help ensure that home and business computers running the Windows OS are kept up-to-date with software patches and security vulnerability fixes. For most computer users, the recommended status of the Automatic Updates helper application is to keep it in the enabled or on state. Many times, however, Windows users will have the need arise to turn off automatic updates for a short period of time. Turn Off Automatic Updates in Windows XP Step 1 – Log-in to your Read More
Configuring DHCP
Configuring the DHCP Server Environment The primary steps required for configuring and managing your DHCP server environment are: Install the DHCP service on a server. Authorize the DHCP server in Active Directory. Configure the necessary DHCP scopes for your subnets. Configure superscopes and multicast scopes. Configure the DHCP lease duration. Configure the DHCP options. Configure the DHCP reservations. Configure the BOOTP tables. Configure DHCP and DDNS integration. Configure split scopes for fault tolerance. How to install the DHCP service Click Start, Control Panel, and then click Add Or Remove Programs. Read More
How to Change a Hotmail Password

Windows Live Hotmail is a free email service provided by the Microsoft Corporation. The service was previously titled “MSN Hotmail” but has primarily been referred to as “Hotmail” by society. The service was one of the first web email services being launched in July of 1996 and purchased by Microsoft in 1997. Windows Live Hotmail was launched worldwide in 2007. Windows Live Hotmail has more than 350 million world-wide users, supports more than 35 languages, and surpasses both Yahoo!Mail and Gmail it total use in the Webmail industry. A common Read More
Null Modem Adapter
An adapter is a hardware device or software component that converts transmitted data from one presentation form to another. The data presentation can be, for example, a message sent between objects in an application or a packet sent through a network. A null modem adapter enables users to transform a normal serial cable into a null modem. It contains the necessary crosslinks between the signals. A null modem adapter converts any straight-through wired cable with connectors into a null modem "cross-wired" configuration. This configuration is suitable for many serial PC Read More
Proximity Sensors

A proximity sensor is an electronic device that is designed to detect the presence of objects, people, or other living things within a given distance and detection threshold. Proximity sensors are able to detect objects without physically touching them by transmitting a detecting field/beam such as infrared, acoustic, and inductive transmissions. When the sensor receives the transmission, it analyzes the return signal for interruptions that indicate that a new object has entered the search area and activates the sensor. The type of sensor deployed depends on the nature of the Read More


Share on: