Overclocking is the process making a computer component run at a higher speed than that specified by the manufacturer. The components that can be overclocked include the CPU, the memory and the video cards. Although there may be many different reasons for overclocking, the most common reason is to increase hardware performance. For example the AMD Athlon 2500+ processor which normally runs at a CPU clock speed of 1.83 GHz may me made to run at a clock speed of 2.20 GHz or the GeForce 6800 cards may be converted Read More
How Self Inking Stamps Work

A rubber stamp is a ubiquitous item. Almost every office has one. They are the perfect tools for administering to forms, making a signature for a check and helping to advertise your company. While the regular stamp and ink pad has been around it seems forever, the newer self inking stamp is definitely a practical innovation. Besides a date stamp, most stamps are static, the text or image never changes and combining the two components of the stamp and the ink has made for an effective and efficient product. Self Read More
How to Disable Autorun

Autorun is a feature that has been included in the Windows Operating System (OS) since the deployment of Windows 95. The utility program will automatically launch media such as DVDs, CDs, USB devices, and memory sticks in order to let the end-user automatically view, manipulate, or run programs stored on the devices. The application uses the atorun.inf file that is stored in the rood directory of the media which contains a list of commands for Windows to execute when the device or drive is opened. Although Autorun is designed to Read More
Routing and Remote Access Service
Routing and Remote Access Service Overview The Routing and Remote Access service (RRAS) is a multi-protocol software router integrated in Windows 2000 and Windows Server 2003 that provides connectivity for remote users and remote offices to the corporate network. RRAS make it possible for remote users to perform their tasks as though they are actually physically connected to the corporate network. A remote access connection enables services such as file and print sharing to be available to remote users. To access network resources, remote access clients can use standard Windows Read More
What is an Asterisks Decrypter?
If you use Microsoft Windows or other applications that require passwords to gain access to specific functions, you may have noticed that these passwords are never shown, but represented by an asterisk (*). Asterisks are used quite commonly not only with Window’s passwords, but almost any passwords that you come across online or in applications. For instance, when you sign into a web email program such as Yahoo! Mail, you will be asked to input your username and password. Your username will be represented by the exact characters you originally Read More
L band

L band is a fequency range between 390MHz and 1.55GHz which is used for satellite communications and for terrestrial communications between satellite equipment. The high frequencies utilized by C band, Ku band, and Ka band would suffer from high signal loss when transported over a copper coax cable such as an Intra-Facility Link. An LNB is used to convert these higher frequency bands to L band, which can be transmitted over the IFL and processed by the IDU. Some satellites transmit on L band, such as GPS satellites.
Trojan Virus

A Trojan virus is a piece of software designed to look like a useful file or software program but performs a possibly nefarious function once installed on a client computer. The virus takes its name from the “Trojan Horse” from Greek mythology setup outside of the city of Troy. Trojan horse viruses differ from other computer viruses in that they are not designed to spread themselves. Instead Trojan horse malware is either delivered as the payload of another virus or piece of malware or through manual end-user action by downloading Read More
Bandwidth Monitor

A bandwidth monitor is a computer application that is able to monitor the bandwidth of a particular network. Bandwidth monitors are able to keep track of the current network speed for both uploads and downloads, the amount of data transferred, the computer’s IP address, and the network card address. By observing the results of a bandwidth monitor, users are able to define what time their connection is the strongest and plan their Internet activity accordingly. This article will list a number of bandwidth monitors that are able to perform all Read More
The Coriolis Effect
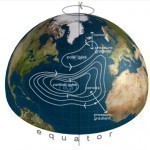
The Coriolis effect is the tendency for a moving body that is on or above the Earth’s surface to drift sideways from its intended course due to the Earth’s rotation. The direction of drift is to the right in the Northern Hemisphere and to the left in the Southern Hemisphere. This is because the Earth’s surface rotates to the east at a faster speed near the equator than near the poles. Who Discovered the Coriolis Effect? French scientist, Gustave-Gaspard Coriolis, is given credit for first discovering the Coriolis effect by Read More
VB Tutorials
VB Tutorials This is your one stop Visual Basic tutorial resource guide that will teach you the basics in Visual Basic programming. This section contains information that will teach you right from scratch, how to make your very first program in Visual Basic. Windows Controls Tutorial This guide will give you a bird’s eye view of Windows Controls & its uses. A Windows control or the “control,” is an object in VB that allows users to interact with their computers. These are objects that we see on our screens that Read More


Share on: