Business Process Integration (BPI) refers to the act of connecting technology systems that were not designed for integration in order to transfer information between different technology resources within an organization. BPI helps coordinate traditionally “stove piped” applications. This can improve overall efficiency and reduce costs. How Do Businesses Align Processes? Business Process Management (BPM) is a common approach used in industry. It focuses on aligning all technological and intrinsic aspects of an organization with its goals and customers' needs. It promotes efficiency and encourages flexibility, integration, and innovation by applying Read More
Black and White
Step 1: Open the Picture in Photoshop which you want to convert into black and white. Step 2: Go to the Image menu and select Channel mixer option as shown below. Step 3: In the Channel Mixer Dialog box first click on Monochrome to make the picture black and white. This option just makes the picture black and white but now we need to enhance the picture. Step 4: To enhance the picture now move the three sliders in any direction till you get a good effect. Here, is the Read More
Constructors and Destructors
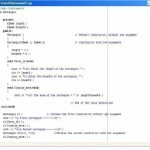
A member function with the same name as its class is called a constructor. It is used to initialize the objects of that class-type with a some initial value. If a class has a constructor, each of the objects of that class will be initialized before they are used within the program. A constructor for a class is needed, so that the compiler automatically initializes an object as soon as it is created. A class constructor is defined without any return-type. They are called whenever a program creates an object Read More
PKI Authorities
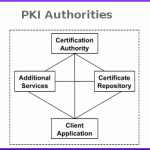
PKI Authorities consists of three different authorities that essentially make up a PKI system. These are the Registration Authority, Certification Authority and Certificate Directory. Registration Authority The jobs of the Registration Authority are to processes user requests, confirm their identities, and induct them into the user database. Certification Authority The tasks of a Certification Authority are to issue public key certificates and to attest that the public key embedded in it indeed belongs to the particular entity as stated in the certificate. The Certification Authority also has the right to Read More
What is ntoskrnl.exe?
Ntoskrnl.exe (Windows boot up kernel) is a vital component utilized in the boot process for NT based Microsoft operating systems. It is also responsible for a host of system services such as process and memory management, security management, object management, hardware virtualization and so on. It holds several sub systems: Cache Manager, I/O Manager, Configuration Manager, Local Procedure Call, Memory Manager, Process Structure, Object Manager and Security Reference Monitor. Collectively, they form part of Executive services and System Services. As a result of such critical responsibilities, ntoskrnl.exe is a fundamental Read More
Telemetry

Telemetry is a highly automated communications technique with the help of which measurements and data collection are done at remote locations and transmitted for monitoring. This technique commonly uses wireless transmission, though original systems used wired transmission. The most important uses of telemetry include weather-data collection, monitoring power generation plants and keeping track of manned and unmanned space flights. How It Works A telemetering system typically consists of a transducer as an input device, a transmission medium in the form of wired lines or radio waves, signal processing devices, and Read More
SMS (Short Messaging Service)
SMS, or Short Messaging Service, is a text-based messaging service that is used by over 2.4 billion mobile phone users worldwide. SMS allows users to send and receive text-based messages, pictures, videos, and audio clips from other mobile phone users and desktop computer users who have applications that can interact with mobile phones. SMS differs from emails and other text-based communication methods because it is compliant with 3G and 4G networks and has a maximum limit of 240 characters per page, making it ideal for short messages. How SMS Read More
How to Convert PowerPoint to DVD

Microsoft office does not include software to assist you in converting your PowerPoint presentations to DVD. Today, there are no freeware utilities that perform this activity for you, but there are many commercial packages available that have free trial periods. Software of this type ranges in price from from $40 – $200 for personal licenses, and much more for commercial or multi-user licenses. All of the following packages perform this function, and offer a free trial period. Software to Convert PowerPoint to DVD PowerVideoMaker Professional allows you to export PPT Read More
Excel Tutorials
Working With Text & Numbers Tutorial A tutorial that shows how to use excel & covers all basics in just a few easy steps Steps: To begin open Microsoft Excel. Then, if necessary, click on the in the upper right corner of the task pane to close the task pane. The screen shown here will appear… Text Formatting & Mathematical Calculations Tutorial A tutorial that shows how to how to format text and perform basic mathematical calculations Steps: Microsoft Excel enables you to choose a default font. The default font Read More
Troubleshooting Active Directory Availability
As an Administrator, ensuring the availability and reliability of the Windows Server Active Directory directory service is extremely important if you are running Active Directory within your environment. Performance problems and poor availability leads to users being unable to perform their tasks or duties within the organization. For instance, when a DNS server fails, it is transparent that Active Directory would be negatively affected. In order for a domain controller to replicate with other domain controllers within a domain, the domain controller has to be able to resolve host names Read More


Share on: