In these modern times of information and data, everyone seems to have something to say. Most people find that the Internet provides more than enough outlets for sharing thoughts and ideas through the use of websites, blogs, social networking sites, and similar venues. Some people, however, want a more organized manner of expressing themselves. These people write their thoughts down in essays, articles, and seemingly endless pages of text. To formally organize these expressions, text must be formatted into a book and printed so that it may be shared with Read More
What Are Variable Speed Drives?

Variable speed drives, which are sometimes referred to as variable frequency drives, regulate an electric motor’s torque output (speed and rotational force). These drives significantly increase an electric motor’s efficiency by controlling the power fed into the machine based on the current demand or work required. As a result, the motor is not driven at full capacity except when needed, which significantly increases energy savings and prolongs the motor’s life. Why Variable Speed Drives were Invented In today’s corporate and industrial environments, millions of motors are used for tasks such Read More
How to Copy a CD

How to Copy an Audio CD A CD can hold up to 80 minutes of uncompressed audio. Because of that, it is still a favorite for recording studios to put music on. Copying an audio CD is possible now with burning software and the necessary hardware built into the computer. To copy an audio CD, all you need is to the original CD, your computer to have a CD burner and then a blank CD that can hold the audio. The first step is to put the CD into the Read More
How to Install Fonts
Fonts are typefaces that we see on the monitor screen. Arial and Times New Roman are examples of fonts, and they outline the shape of the characters that appear on the screen. A font could be a serif font or a sans serif font and can be used in several different sizes. There are basically three types of fonts: TrueType fonts that you can use on any version of the Microsoft Windows operating system. OpenType fonts that you can use with Microsoft Windows 2000 and later versions. PostScript Type1 fonts Read More
What is Acesulfame Potassium?

Acesulfame potassium (Acesulfame K or Ace K, where “K” is the elemental symbol for potassium) is commonly used as an artificial sweetener or flavor enhancer. It is used in low calorie food products as it replaces sugar and other natural sweeteners that commonly add large amounts of calories. Acesulfame potassium’s trade names include “Sunett” and “Sweet One” and has the additive code E950 in the European Union. It looks like a white crystalline powder when pure. Acesulfame potassium’s chemical formula is C4H4KNO4S and is technically a potassium salt. Why is Read More
What is Wardriving?

The act of searching for WiFi networks with a laptop or mobile device while driving is referred to as wardriving. The term originated from “wardialing,” which came from the hit movie War Games in which random phone lines that were connected to a modem were searched for. Although wardriving was originally developed in order to search for unprotected Wireless networks, the current practice of mapping unprotected networks with GPS location data was developed in the spring of 2001. What is Wardriving? Wardriving captures information about network and Internet usage. Although Read More
Deleting an Element from a Heap
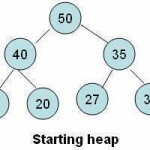
Deleting an Element from the Heap Deletion always occurs at the root of the heap. If we delete the root element it creates a hole or vacant space at the root position. Because the heap must be complete, we fill the hole with the last element of the heap. Although the heap becomes complete, i.e. it satisfies the shape property, the order property of heaps is violated. As the value that comes from the bottom is small, we have to perform another operation to satisfy the order property. This operation Read More
Petaflop
A FLOP refers to the number of floating point operations per second that a computer processor can accomplish. The floating point method is used for current measures of computer performance vice the legacy instructions per second due to the greater precision required by the CPU to execute the more scientific instruction. A petaflop is the measure of a computer processor's speed expressed in the thousand trillion floating point operations per second or one quadrillion operations per second. As a baseline reference, the average calculator just needs to be capable of Read More
mfefire.exe

Mfefire.exe is McAfee Anti-virus Firewall Service’s process. The McAfee Firewall prevents malicious programs from installing themselves or third party components on the computer. Mfefire.exe is not a system process, but is required to run the McAfee Firewall. Mfefire.exe generally runs on the Windows Operating System and can be found in the primary hard drive’s Program Files folder. How Mfefire.exe Works Mfefire.exe runs in the computer background and, when activated, prevents programs from running and/or installing themselves on the computer without permission. It detects processes as they attempt to run, Read More
Master Blaster Virus

The Master Blaster virus is a malicious program that was developed from the initial Blaster worm. It was repackaged by Jeffrey Lee Parson during 2003. It was also released to infect computers running on MS Windows OS versions across the globe during the same year. The repackaged or reprogrammed Master Blaster virus was then known as Blaster B or LovSan. This variant of the Master Blaster virus exploited known vulnerabilities of MS Windows OS versions. This activity was similar to other known variants of the Master Blaster Virus. Upon infection, Read More


Share on: