Over the past several years, the popularity of MP4 formatted music and video files has continued to increase. All iDevices to include the iPhone, iPad, and iPod support playback of the MP4 format as well as the Sony Playstation Portable. As a result, a common task that arises for consumers is converting legacy MP3 formatting music to MP4. Once a music track is converted, it can then be used on any device supporting the MP4 format. Steps to Convert MP3 to MP4 With iTunes Step 1– Download, install, and launch Read More
This Device Cannot Start – Code 10
When someone receives the Windows error, “This device cannot start. Code 10 in audio driver,” it means that he/she has a bad, missing, or incompatible driver for his/her sound card. The very technical and confusing explanation for this message, according to Microsoft, is this: “If the device has a FailReasonString value in its hardware key, that string appears as the error message. The driver or enumerator puts this registry string value there. If there is no FailReasonString in the hardware key, you receive the following error message: This device cannot Read More
How to Use Favorites
The new version of Internet Explorer has a feature built in known as Favorites Center. This controls the favorites of the web browser, but then incorporates other features such as a RSS feed and then your recent history. All of these components, when combined together, make for an exceptional Favorites Center. Making it work to your liking, though, can be a little bit tricky. Internet Explorer Favorites The first feature that is obvious for a favorites center is the section of favorites. These are all the web pages that you've Read More
SERPs
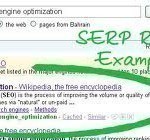
SERPs are “Search Engine Result Pages” If a search engine user types in a search for “rubber baby buggy bumpers” and your web site is the first result, then you can be said to have the #1 SERP for “rubber baby buggy bumpers.” The whole purpose of Search Engine Optimization (SEO) is cause web pages to rank highly in the SERPS. The higher your web pages rank in the SERPS for their chosen keywords, the more traffic your web site will receive. Tracking SERPs Check How can I track my Read More
How Can I View My House via Satellite?
Viewing one’s house via a satellite is very easy now with programs such as MapQuest.com and Maps.Google.com. Both of these websites provide a user the chance to type in their address and then zoom in on the house with an aerial view taken by a satellite. Google Maps can zoom in a bit more than MapQuest, but they both allow for someone to view their own house. To begin with, open up either MapQuest or Google Maps. The choice is entirely yours. Once the site has loaded, begin to punch Read More
Butterworth Filter
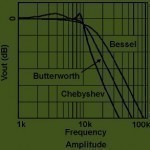
A Butterworth filter is a signal processing filter that has an extremely flat frequency response in the passband. It is referred to as a maximally flat magnitude filter and is commonly used in both analog and digital audio crossover filters in home, commercial, and car stereo systems. Who Invented the Butterworth Filter? British engineer, Stephen Butterworth developed a reputation for being able to solve extremely difficult if not impossible mathematical problems. When Butterworth was conducting his research, most filter designs were a result of trial and error due to the Read More
HTTP Error 404

HTTP Error 404 is an error message which means that the web page you are looking for cannot be found. The 404 error is also known as “File not found”, “Not Found” and “Gone”. The Official Definition of 404 Quoting from RFC 2616 – Hypertext Transfer Protocol — HTTP/1.1: 404 Not Found The server has not found anything matching the Request-URI. No indication is given of whether the condition is temporary or permanent. The 410 (Gone) status code SHOULD be used if the server knows, through some internally configurable mechanism, Read More
Types of SCSI Cables
Small computer system interface or SCSI is a standard cable system that facilitates physical connection and transfer of data between a computer and its several peripherals. As you may know, a computer system is made up not just of the computer itself but also of other components. The computer is connected to a separate printer, scanner, fax machine and other equipments that are made and installed to complement the basic operations of the personal computer. The computer itself is made of many peripherals. The central processing unit is connected through Read More
RF Connectors
RF connectors, also known as a radio frequency connectors, include a number of different types of connectors constructed to work with a wide range of multi-megahertz applications. RF connectors provide a quick and easy way to connect coaxial cables to each other and to other devices. There is a range of capability among the different versions of the RF connector. Some of the more efficient types help to minimize the variance of transmission at the point of connection. The type of fastening mechanism will vary from one type of RF Read More
Configuring and Managing IPSec
IPSec Review IPSec is a framework of open standards for encrypting TCP/IP traffic within networking environments. IPSec works by encrypting the information contained in IP datagrams through encapsulating to provide data integrity, data confidentiality, data origin authentication, and replay protection. IPSec uses cryptography to provide authentication, data integrity, and data confidentiality services. Authentication deals with verifying the identity of the computer sending the data, or the identity of the computer receiving the data. IPSec can use digital certificates, the Kerberos v5 authentication protocol, or pre-shared keys as an authentication method. Read More


Share on: