"Low Tech" is the best way to describe a basic television antenna. Television antennas feature a series of elements cut to exact lengths which are designed to receive a compatible frequency from a transmitted television signal. Each element has a pair of metal rods (primarily aluminum based) extending from a boom. The key difference between various brands of television antenna is based on the quality of construction and how well anodized the metal is. As the metal oxidizes and the rivets rust, the active elements tend to lose contact. When Read More
How to Solve a Buffer Overrun Detected Problem
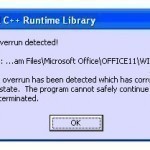
Buffer overrun detected problems may occur when software that is coded in C or C++ permits unsafe data. This problem happens with all operating systems, but it is particularly common on Windows operating systems. The unsafe data that is introduced externally can exploit vulnerabilities in software or cause program crashes. This can permit malicious software to enter and harm the computer. Buffer overrun detected error messages should be corrected as soon as possible to ensure that greater security issues do not arise. Follow the instructions below to solve the buffer Read More
How to Use the Grep Command
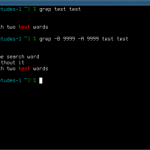
The grep command is a search command built into a variety of Unix based operating systems. This command line utility, whose name stems from the original Unix term which means “search globally for lines matching the regular expression, and print them,” can be accessed using the command line or terminal from anywhere in the Unix operating system. When given a particular list of files to search through, the grep command becomes especially useful, as it can search through any amount of text to find exactly what you are looking for. Read More
DTMF (Dual-Tone Multi-Frequency)
DTMF tones, or Dual-Tone Multi-Frequency signaling, are audible tones that are used by touch-tone telephones to identify which number key was pushed by the operator. DTMF tones have been used since 1963 and are used by all standard touch-tone telephones in the United States as well as in many other countries around the world. DTMF tones can be heard while the operator enters each digit, but must be decoded by a DTMF decoder at the telephone company’s switching center before a call can be completed. How DTMF Tones Work Read More
Fingerprint Scanners
Fingerprint scanners are biometric security systems designed to use the distinct features of an individual's fingerprints to provide security. Fingerprint scanners are now being used in police stations, security-intensive industries and, most recently, on computer shops as a peripheral device for computers. Biology of a Fingerprint Every person has marks on his fingers. These marks on the fingers are mainly for gripping things as they provide frictional resistance. These marks have a pattern and this pattern is called the fingerprint. The person's fingerprint is determined by his or her genetic Read More
How to Change the Font Color in Windows Explorer
While Windows Explorer is generally easy on the eyes, many computer users like to customize certain aesthetic features on their computer's operating system. One way to do this is to the change the font color in Windows Explorer. Here are some tips. Changing the font colors and even the font in Windows Explorer is extremely easy to do and takes less than a minute. It should be noted however that not every font in Windows Explorer can be changed, but the items that can be changed will definitely alter the Read More
VSAT (Very Small Aperture Terminal)

VSAT (Very Small Aperture Terminal) is basically a two-way satellite ground station with a less than 3 meters tall (most of them are about 0.75 m to 1.2 m tall) dish antenna stationed. The transmission rates of VSATs are usually from very low up to 4 Mbit/s. These VSATs’ primary job is to access the satellites in the geosynchronous orbit and relay data from terminals on earth to other terminals and hubs. They often transmit narrow-band data such as credit card transactions, polling, RFID (radio frequency identification) data, and SCADA Read More
VB.NET Tutorials

VB.NET Tutorials This tutorial sections assumes that you are already familiar with VB.NET. This tutorial is based on HTTPModule for Digest Authentication in VB.Net. The coolest thing about using an HttpModule for either DIGEST or BASIC Authentication against one’s own Data Store is that as long as the HttpModule is configured at all the destination sites/applications and as long as each location has access to the same database information ( The “Users” table), the user can authenticate once and travel anywhere he/she wants without having to ever see a logon Read More
Dielectric Constant
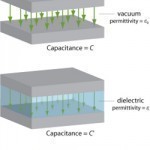
A dielectric constant measures the extent that a material concentrates electrostatic flux and is also known as the relative static permittivity, static dielectric constant, and relative dielectric constant. It is essential when determining if a substance can be used in a capacitor or various chemistry and physics applications. A material’s dielectric constant value must be known before using it to make optical fibers or coaxial cables. Although the term is commonly used, it may have different mathematical connotations depending on the context of its application. The dielectric constant refers to Read More
How to Delete Internet History

Deleting Internet history clears the record of web sites visited. This procedure helps keep Internet browsing private. Below are steps to manually delete Internet files from the computer: Delete Internet History in Internet Explorer By default, Internet Explorer keeps Internet history for 20 days. To delete Internet history in Internet Explorer, open the Tools menu, select “Internet Options,” click the “Delete…” button under “Browsing history,” make sure that “History” is selected in the dialog that pops up, and click the “Delete” button. Under “Browsing history” it is also possible to Read More


Share on: