If you want to add a printer to a wireless network, you need to: 1) Ensure that the printer has at least one USB port. 2) Purchase a wireless adapter and connect it to the printer’s USB port. Since wireless adapters work on Plug-and-Play technology, the printer should automatically detect it and begin installing all of the drivers necessary for the wireless adapter to function properly. 3) In order to specify which wireless network the printer should connect to, connect the printer to the router via an Ethernet cable and Read More
Dielectric
A dielectric is a material that restricts the flow of current. Dielectrics are defined by their dielectric constant, current leakage, and breakdown voltage. They are mainly used in capacitors, allowing charge to build up on the conductive plates. An insulator is a dielectric than can withstand a high electric field without letting current flow through it. Permittivity When the material is surrounded by an electrostatic field, the electrons in each atom shift towards the positive side and away from the nucleus. This creates a dipole moment in the atom and Read More
Authentication Types
What is Authentication Authentication is the process whereby the system identifies legitimate users from unauthorized users. It is the process in which a user identifies his/her self to the system. How effective an authentication process is, is determined by the authentication protocols and mechanisms being used. Windows Server 2003 provides a few different authentication types which can be used to verify the identities of network users, including: Kerberos authentication protocol NT LAN Manager (NTLM) authentication protocol Secure Sockets Layer/Transport Security Layer (SSL/TLS) Digest authentication Smart cards Virtual Private Networking (VPN) Read More
HDCP (High-Bandwidth Digital Content Protection)
High-Bandwidth Digital Content Protection, also known as HDCP, is a newer form of Digital Rights Management (DRM) that was designed to control digital video and audio content. The technology was originally created by Intel to ensure that digital audio and video travelling across a Digital Video Interface (DVI) or High-Definition Multimedia Interface (HDMI) would follow the various guidelines put forth by the Digital Content Protection group. What Is Required Of An HDCP Capable Device In order for a product to claim that it is HDCP capable, it must have a Read More
Satellite Radio

Satellite radio refers to a number of subscription-based radio broadcasting programs that are available in the US, Europe, and elsewhere that are dependent on satellites to provide mobile users with constant radio access. While terrestrial-based FM radio stations only provide radio broadcasts to a specific area, usually confined to the city they are located in, satellite radio is available even while the listener is moving between cities, states, and even countries. Satellite radio has been available for just over a decade, with the first artist ever broadcasted on satellite radio Read More
What is a Rollover Cable?

A rollover cable is a network cable that connects a computer terminal to a network router’s console port. It is also referred to as a Cisco console cable and is normally flat and light blue so as to distinguish it from other network cable types. The pin-outs on one end of the cable are reversed from the opposite end, which is how the cable derived its name. Rollover cables are also known as Yost cables or Yost Serial Device Wiring Standard connectors. How to Identify a Rollover Cable A rollover Read More
Monitoring IPSec
Using the IP Security Monitor Snap-In to Monitor IPSec The IP Security Monitor snap-in, a new feature in Windows Server 2003, can be used to monitor and troubleshoot IPSec activity. The IP Security Monitor snap-in provides enhanced IPSec security monitoring. As long as the IPSec policy is active, you can monitor how the IPSec policy is functioning within your networking environment through the IP Security Monitor. The main administrative activities which you can perform through the IP Security Monitor snap-in are listed here: Customize the IP Security Monitor display. Monitor Read More
Service Management
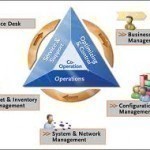
Service management, also called IT service management, is the discipline used in industries that provide services or a combination of goods and services. While widely used in the IT industry, specifically the ICT (information and Communication Technology) sector, service management can be integrated into many other industries. Service management is usually used in conjunction with operations support systems. Systems that use service management include order management, inventory management, activation, maintenance, performance diagnostics, and several other types of support systems to make sure that these systems are running proficiently and error Read More
How Do I Get My Songs on iTunes?
New users and those who have not yet used iTunes may have a difficult time getting their music into their iTunes library. The process is relatively simple and can be done in a variety of ways. The most common ways to transfer music to the iTunes library are: Songs from Music CD Music from CDs can be imported to iTunes with the handy features that iTunes software provides. Simply load a CD into the computer's CD reader and allow iTunes to locate it. Once it is located, the CD will Read More
Classes
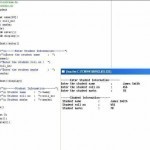
A class is an approach to bind the data, describing the entity or an object, and its associated functions together. In C++, a class creates a data-type that is used to create objects of that particular type. Class represents a group of similar objects. Example: class account { private: int accoutno; char type; float balance; public: float deposite(float amount) { balance += amount; return balance; } float withdraw(float amount) { balance -= amount; return balance; } }; In the above example, the data describing an account object (i.e. accountno, type Read More


Share on: