Cell phone tracking is used to track the current position of a cell phone. An active call is not required to track the current position of the cell phone, but the cell phone must be turned on for a successful tracking. GSM localization uses multilateration to establish the position of GSM cell phones, generally with the objective to trace the user. GSM localization is then done by triangulation to locate the user/cell phone, on the basis of the strength of the signals. Triangulation is the process of finding one’s position Read More
Planning and Implementing an Authorization Solution
An Overview on Authorization Authentication is the first step in implementing a security strategy to protect your network resources and elements from unauthorized users, because it is the process that deals with identifying valid authorized network users from unauthorized users. Authentication therefore verifies the identity of users. The next step in securing your network resources and elements from unauthorized access is authorization. Authorization is the process that controls which objects an authenticated network user can access. Just because a user is authenticated, does not necessarily mean that the particular user Read More
How to Download a Video from a Camcorder to a Computer

The process of downloading a video from a camcorder to a computer depends on whether the camcorder is digital or analog (old-style camcorder that uses tapes). For an analog camcorder, install a signal digitizer card in the computer, which is fairly common with today’s readily available off-the-shelf TV tuner cards. This card converts the analog camcorder signal to a digital one, and can be purchases for under $100. However, try to bear in mind the availability of space on the hard drive, due to the fact that even short video Read More
How to Use Powerpoint
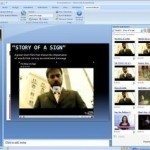
What is Powerpoint? Powerpoint is a powerful program that comes with Microsoft Office. Powerpoint allows users to create animations, presentations, and slideshows for lectures, home movies, meetings, and other purposes. Powerpoint includes a wide variety of tools, features, and special effects that make powerful and entertaining presentations easy to create. With this software, users have the ability to modify virtually every aspect of their presentation, including text options, color schemes, and placement of objects such as videos and pictures. Users also have the ability to create an unlimited number of Read More
How to Send a Fax via Outlook Express
You can send a fax through Microsoft Outlook with a few simple, easy steps. Unfortunately, if you have Microsoft Outlook Express, you need special software to be able to send a fax. There are several software programs available online. Here are some of the top programs you can use. Mighty Fax Mighty Fax is one of the worlds most popular and user-friendly Windows fax software programs available today. Mighty Fax lets you send and receive faxes directly from Microsoft Word or any of your other Windows programs without the need Read More
Cryptology

Cryptology Cryptology is the science which incorporates both cryptography and cryptanalysis. Cryptologists Practitioners of cryptology are known as cryptologists. Cryptology in Context A cryptographer will use cryptography to convert plaintext into ciphertext and a cryptanalyst will use cryptanalysis to attempt to turn that ciphertext back into plaintext. Both the cryptographer and the cryptanalyst are cryptologists. Cryptography and cryptanalysis are the two sides of cryptology.
MediaGuard

MediaGuard is a conditional access system used by television broadcasters such as the Canal+ Group, Orbit, Malaysia’s Astro, and China’s BGCTV. MediaGuard is a product of Nagra France. Nagra France is a division of the Kudelski Group, a Swiss company. The Kudelski Group also owns Nagravision. MediaGuard competitors include Conax, CoreTrust, Cryptoworks, Irdeto Access, Latens, SafeAccess, Verimatrix, Viaccess, VideoGuard, and Nagravision.
Free Backup Software
Constantly backing up is important because computers are not always perfect, and thus can crash, fail, and malfunction without a warning. Therefore, valuable information such as work documents, pictures of families, and videos that you've been working hours on can be lost. Currently, many operating systems already have pre-installed backup programs that are sufficient for a home user. As in the case with Microsoft Windows, Microsoft has pre-installed a backing up utility which can be found by going to: Start, All Programs, Accessories, System Tools, and clicking Backup. This utility Read More
Voice Recognition Software
Voice Recognition Algorithm Investigation with cosine transform, and anti transform algorithm, with some voice recognition code. Translator: Croatian, English. 2D to 3D picture algorithm. Perlbox Voice Perlbox Voice is an voice enabled application to bring your desktop under your command. With a single word, you can start your web browser, your favorite editor or whatever you want. This is the Linux and Unix voice recognition solution. Voice Conference Manager Voice Conference Manager uses VoiceXML and CCXML to control speech recognition, text to speech, and voice biometrics for a telephone conference Read More
Shoulder Surfing

Shoulder surfing is a security attack that is implemented by observing a victim as he/she enters a PIN, fills out a form, or performs another activity that exposes their confidential information. A shoulder surfer may observe a victim by looking over their shoulder, taking pictures, or using binoculars from a distance. For example, credit card fraud is usually started by taking a picture of a victim’s credit/debit card as he/she is standing in line at a store and then using the numbers on the card to make purchases over the Read More


Share on: