Adding songs to an MP3 player is easy, no matter which type of an MP3 player you have. There are several ways to do this. Traditional Method The easiest method of transferring music to an MP3 player is to simply plug your MP3 player into your computer and go to “My Computer” (the icon is located either on your desktop or Start menu). Next, find your MP3 player’s icon which should be listed next to other drives. Click on this folder, open it and then drag your music files into Read More
Long Distance Wireless Power Transmission

Simple wireless power transmission works because of the principles of magnetic resonance and magnetic induction. This power transmission system relies on two coils in range with each other and resonating at the same frequency. The coils need to be in range because the magnetic field of the source must be strong enough for the receiving coils to induce current flow. Matching resonating frequency is also needed to enable further transmission of power through magnetic induction. Modifications or an entirely new set of principles are, however, required in order to enable Read More
How Nuclear Fusion Works
Nuclear Fusion relates to nuclear power. So let us start with the process involved for getting nuclear power. There are, mainly, two processes involved: 1) Nuclear Fission Most of the present day nuclear power plants use this process to get power. This process uses a conventional method of splitting one atom into two. Here high-energy neutrons split heavy atoms of uranium. This results in release of huge amount of energy. However, this also releases large radioactive wastes and high radiation waves, which remain for long period. To avoid such leakages Read More
WINS (Windows Internet Name Server)
In the Windows Server family, the primary means for client computer to locate and communicate with other computers on a internet Protocol (IP) network is by using Domain Name System (DNS). However, clients that use older versions of Windows, such as Windows NT 4.0, use network basic I/O system (NetBIOS) names for network communication. Some applications that run on Windows Server 2003 may also use NetBIOS names for network communication. Using NetBIOS names requires a method of resolving NetBIOS names to IP addresses. One can implement Windows Internet Name Service Read More
Mind Uploading
Mind uploading is the term used for the theoretical transfer of a human mind to an external carrier. Mind uploading can also denote whole brain emulation, electronic transcendence, mind transfer, etc. Mind uploading does not refer to the transfer of the actual physical brain but rather the transfer of its consciousness to a robotic brain which will generate responses that cannot be distinguished from the actual original brain. In cases where the subjects' consciousness is transferred to a memory device, the result is an artificial intelligence. In cases where the Read More
Storage Management

Storage management refers to a collection of machines, software, analysts, procedures, structure, techniques, and goals that are used to store, organize, analyze, and backup data. Storage management can be implemented by any company and varies in the size of the company, the amount of data to be stored, and the techniques that are implemented. While many programs pass themselves off as storage management solutions, storage management encompasses the entire system a company uses to store, organize, analyze, evaluate, and process information. How Storage Management Works Essentially, storage management is Read More
Federated Identity Management
Federated Identity Management is a version of Single Sign-On where each device, system, and application queries a centralized database for authentication and authorization information. In addition to the goals of any other identity management system, Federated Identity Management systems are tasked with enabling authentication and authorization data across organizational boundaries. In a true Federated Identity Management system, authentication data can be passed across security domains from within a company to its business partners. This can enable Single Sign-On to extend past organizational boundaries. Federated Identity Management is often abbreviated FIM. Read More
How to Remove IPv6 in Vista
IPv6 stands for Internet Protocol version 6. IPv6 is the latest version of the network-layer protocol for packet-switched networks. The version that is generally used is IPv4. One of the reasons for the upgrade to IPv6 is that it allows greater space and flexibility in assigning IP addresses. For instance, IPv4 is based on a 32-bit address system that limits the number of possible unique addresses to 4,294,967,296. In a few years, the number of available unique addresses will decrease. IPv6 solves this problem by making the number of possible Read More
VMWare Error 1335
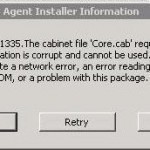
Computer professionals have used the VMWare workstation for a number of years to test software on different types of operating systems on a single computer. Those who purchase and download the VMWare software from the online store often encounter VMWare error 1335. This error is typically as a result of downloading the incorrect software build, which fails the software’s MD-5 hash test. How does the VMWare Workstation work? The VMWare workstation creates a fully isolated virtual machine that contains an operating system and its associated programs. The computer’s hardware is Read More
MP3 Converter
Digital media files come in many different formats but not all formats are supported by certain programs or hardware. Likewise, some formats simply function better than others. For these reasons, many people find themselves in the position of needing to convert a file from one format to another. For example, MP3 players generally only support the MP3 file format so when a user has a particular song, video, or other file that he/she wants to put on his/her MP3 player and the file is not in MP3 format, the user Read More


Share on: