DNA computers will be the next-generation computers made of genes' building blocks. Because of their speed, miniaturization and data storage potential DNA computers are being considered as a replacement for silicon-based computers. Current DNA computer research has already proven that DNA computers are capable of solving complex mathematical equations and storing enormous amounts of data. Limitation of Silicon Chips Silicon-based computer chips have been around for more than 40 years and manufacturers have been successful in making silicon-based chips smaller, more complex and faster than their predecessors. According to Moore's Read More
Socket-A
Socket-A is a 462-contact CPU socket which is used by AMD CPUs, such as the K7, Athlon, Athlon XP, Duron, and Sempron. The Socket-A is a Pin Grid Array (PGA) Zero Insertion Force (ZIF) socket. A ZIF socket features a lever on one side of the socket. When this lever is pulled up, the spring contacts inside the socket are opened. This allows the CPU to be inserted easily into the socket. The lever is then pushed down, closing the spring contacts and clamping the CPU into place.
How an Optical Mouse Works
Optical mice are the de facto standard for mice to communicate between the end user and the computer. The optical mouse is a great improvement of the mechanical mouse that was created in the early 1970s. Agilent Technologies introduced the Optical mouse in 1999. The technology uses a tiny camera that takes thousands of pictures per second to determine position and speed. The optical mouse uses a very small light emitting diode more commonly referred to as an LED, which is red in color. This LED bounces light off of Read More
Network Backup
Network backup is any backup system where the data to be backed up traverses the network to reach the backup media. Network backup typically requires a client-server software architecture. The backup server resides on a centralized server and the backup clients reside on every system to be backed up. Advanced network backup systems can manage backup media which are also connected to the backup server via a network. Network backup systems are much more scalable and manageable than local backup systems where tape drives are attached to each comouter ystem. Read More
How to Reset a Dell BIOS Password
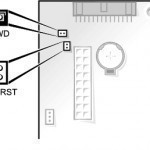
Dell Dimension BIOS Password Recovery The BIOS password may be cleared from a Dell Dimension by moving the password jumper on the motherboard. The password jumper’s location on a Dell Dimension motherboard can be found by reviewing the Dimension User Guides. For most Dell Dimension desktops, the steps to reset a BIOS password and clear all CMOS settings are: Locate the 3-pin CMOS password reset jumper on the system board. Remove the jumper plug from pins 1 and 2. Place the jumper plug on pins 2 and 3 and wait Read More
Digital Audio Cables
One of the significant developments with the widespread adoption of the personal computer for home, business, and school use is the digitalization of media and the subsequent mass adaptation by consumers and industry. While digital media is not a new concept, it has only recently made its way into the “normal” household and is commonly supported by digital audio cables. As a result, higher quality audio playback is now supported while watching movies or listening to music that can approach (or at times exceed) the experience found in a high-end Read More
How to Convert FLV to MPEG
Two common video files that are found on the Internet include FLV (Flash Video) and MPEG (Motion Pictures Expert Group). While both are extremely easy to view and store, many computer users still prefer to convert Flash files to MPEG (specifically MPEG-2) for viewing on either PC Based media player or home DVD players. While it is easy to convert one type of file to the other, it is important to be aware of each file's attributes. What is a Flash File (FLV)? Flash files are used primarily on the Read More
Online Data Storage
Online data storage, also known as Internet data storage, is a technology which allows people to store their data in the Internet. With broadband speeds becoming faster and bandwidth pricing dropping every year, more people are interested in purchasing online data storage. Online data storage not only provides an additional flexible source for storing data but also acts as a backup mechanism and provides an effective method of sharing data with others. This is the reason why Internet data storage is increasingly popular even as the costs of physical local Read More
Difference Between SD & SDHC Memory Cards

The Secure Digital (SD) memory card format was developed for portable devices across a wide range of product categories and is the unofficial industry standard for memory card format. SDHC is the high capacity variant of the memory card format. It has a slightly different communication protocol from the SD type and does not necessarily work on the same devices. Newer computing devices typically support both formats, however, older devices will not necessarily do so. Consumers often want to determine the differences between SD and SDHC memory cards. SD Memory Read More
What is a RAM Defragmenter?

A RAM “defragmenter” is a software that frees up wasted RAM on the computer in order to improve performance and prevent system failures. However, a RAM defragmenter does not defragment a computer’s memory. Rather, it stops processes that are using too much memory, not running properly, or associated with programs that are no longer on the computer. How RAM Defragmenter Works A RAM defragmenter runs in the computer background and analyzes its running processes in order to detect which ones are using too much memory. If the RAM defragmenter Read More


Share on: