Modern society has brought many luxuries and accodomations to the lives of millions of people all over the world. One of these accomodations is the wide network of email addresses that have accumulated over the years. Nearly everyone, even those who do not have regular access to a computer, has an email address, if not multiple email addresses. Reaching someone through email can be frustrating, however, if a user does not know the recipient's email address. This article will list several ways that a user can locate a person's email Read More
Microblog

A microblog is, as the name suggests, a blog that is much smaller than a typical, traditional blog. It is not smaller in the number of hits that it receives, but instead, in the size of the individual blog posts. While a blog post on a traditional blog might be anywhere from 250-1000 words (some longer, some shorter), your typical microblog entry is a sentence or two. Sometimes, there are no words, but instead, a picture. In other words, a microblog is a site that publishes numerous short little entries Read More
Click Fraud

Click fraud is a internet crime targeting pay-per-click advertising systems. Click fraud occurs when a person or a group of persons, computer software or a internet bot clicks on an ad for the sole purpose of generating income for the publisher or putting a competitor out of business and not because of any real interest in the products advertised. Click fraud is considered a felony in many places such as California and the United Kingdom. Pay-per-Click Advertising and Click Fraud PPC advertising is a contract between two parties – usually Read More
What is Iertutil.dll?
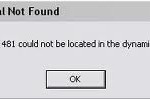
Iertutil.dll is a Runtime utility for Internet Explorer that is essential for Internet Explorer 7 to function properly. If Iertutil.dll is missing, the user may not be able to run Internet Explorer or even boot his/her computer. Iertutil.dll was missing from the Beta version of Internet Explorer 7, causing many users to have to manually replace the file, but the file is included in the final version of Internet Explorer 7 that is now available. Iertutil.dll runs on the Windows Operating System and can be found in the primary hard Read More
How to Ask a Question on Yahoo Answers

Yahoo Answers is a social networking platform that Yahoo sponsors. It allows users to ask other Yahoo users questions and receive answers based on specific categories. Yahoo Answers is ideal for those who wish to receive answers to personal questions and allows others to rate the best answer, specify their individual sources and qualifications concerning their response, and provide links with further information for the user asking the question. Yahoo Answers requires users to have a Yahoo account, but allows users to ask questions anonymously and hide their email address. Read More
How to Check Your IP
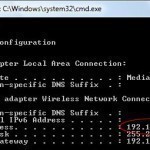
What is an IP An Internet Protocol (IP) is used for communicating data with other computers–otherwise known as a packet-switch internetwork–using a protocol such as TCP/IP. The most common type of packet-switch internetwork is the Internet. Therefore, an IP address is the protocol used to communicate with the Internet. Another way to think about it is that the IP address is the computer’s address. When files come to your site, it comes to your IP address because that’s what it recognizes. How to Check Your IP There are two ways Read More
How to Download Torrent Files

Torrent files are part of a P2P (peer to peer) trading system that make transferring files from one person to another on the Internet very easy, quick, and effective. It is important to note that torrent sharing is different from other types of P2P services, most notably Kazaa. For instance, with Kazaa, the user searches for other Kazaa users with the P2P application to see what files they are sharing. With torrent sites, the user goes to an index website that has torrent files (sometimes referred to as archives), which Read More
How Do RSS Feeds Work?

RSS (Really Simple Syndication) is an addition to Internet technology that is used to keep people updated on their favorite websites. RSS works in conjunction with XML code, which continuously checks the contents of a website for updates. If updates are found, they are broadcast to all the subscribers of the website through a feed. RSS feeds work by taking content that appears on a website, converting it to a simple text format, and then releasing it to a RSS reader–such as Google Reader–to then view the article. If the Read More
How Does AIM Password Recovery Work?
AIM password recovery works by one of two methods: Resetting your AIM password online Recovering stored passwords from the Windows Registry Reset your AIM password The easiest way to recover an AIM password is to visit the AOL Lost Your Password? page. To use this page, enter your AOL screen name and AOL will e-mail your AIM password to the e-mail account associated with it. If you no longer have access to the e-mail account associated with the screen name, AOL will refuse to assist you. For AOL subscribers only: Read More
Black Hat SEO

Within the SEO community, some optimization tactics are considered Black Hat SEO. These are tactics which are not considered to be good or fair by search engine operators, search engine optimizers, or web site visitors. There is no generally accepted definition for black hat SEO. What may be considered appropriate by one webmaster may not be considered appropriate by another webmaster. In addition to personal differences, guidelines for appropriate conduct vary across web site categories. What might be considered acceptable for a web site in the gambling industry may not Read More


Share on: