Configuring Dial-up Connections and Dial-up Entries Before you can configure ISA Server dial-up connections, you have to create the necessary policy elements. ISA Server dial-up connections are typically configured when you want to access services that are not Web services, on clients that do not have the Firewall Client installed. These services are usually the Post Office Protocol (POP3) service or the Network News Transfer Protocols (NNTP). When you create dial-up entries, you can apply connection rules and policies for these connections with ISA Server. A dial-up entry uses policy Read More
How Do I Share my Calendar in Outlook Express?

Your calendar is probably so full of reminders like doctor’s visits, parties, meetings and birthdays that your friends, families and co-workers need to see it just to figure out where they “fit in your schedule”. Outlook makes it easy to share your calendar with family and friends! Go to your Calendar and in the Navigation Pane, click Share My Calendar. If it doesn’t appear, that means you aren’t using an Exchange server email account. If you are using a POP3 (Yahoo, MSN, etc.) or some other account, it won’t work. Read More
Authentication Types
What is Authentication Authentication is the process whereby the system identifies legitimate users from unauthorized users. It is the process in which a user identifies his/her self to the system. How effective an authentication process is, is determined by the authentication protocols and mechanisms being used. Windows Server 2003 provides a few different authentication types which can be used to verify the identities of network users, including: Kerberos authentication protocol NT LAN Manager (NTLM) authentication protocol Secure Sockets Layer/Transport Security Layer (SSL/TLS) Digest authentication Smart cards Virtual Private Networking (VPN) Read More
Monitoring IPSec
Using the IP Security Monitor Snap-In to Monitor IPSec The IP Security Monitor snap-in, a new feature in Windows Server 2003, can be used to monitor and troubleshoot IPSec activity. The IP Security Monitor snap-in provides enhanced IPSec security monitoring. As long as the IPSec policy is active, you can monitor how the IPSec policy is functioning within your networking environment through the IP Security Monitor. The main administrative activities which you can perform through the IP Security Monitor snap-in are listed here: Customize the IP Security Monitor display. Monitor Read More
Securing WINS Servers
WINS Server Role Security Issues A WINS server is an enhanced NetBIOS name server that can resolve NetBIOS computer names to IP addresses. The WINS database hosted on the WINS server is used to store and maintain NetBIOS computer names to IP addresses mappings. WINS registers NetBIOS computer names, and then stores these client name registrations in the WINS database. A WINS server is basically needed if there are applications that require WINS for name resolution to operate correctly. WINS is also typically needed if all your domains have not Read More
Error 0x0000007e
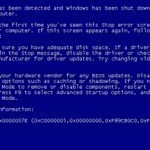
Error 0x0000007e is an error message that is displayed whenever a computer cannot access one of its hard drives, ports, optical drives, system files, or other critical components necessary to run the operating system. Usually, the computer’s error handler discovers these problems immediately upon booting from a device and will display a specific error message before the user is able to log in. However, if an exception occurs that prevents the error handler from discovering these problems immediately, it will display Error 0x0000007e after the computer has booted up and Read More
DOS Commands
Over the years there have been many versions of DOS, including PC-DOS, MS-DOS, DR-DOS, and 4DOS. Although DOS is not used frequently any more, the DOS commands are still available in the Microsoft Windows XP command shell. Listed below are the commands for the DOS command shell included with Microsoft Windows XP. DOS Commands ASSOC Displays or modifies file extension associations Syntax ASSOC [.ext[=[fileType]]] .ext – Specifies the file extension to associate the file type with fileType – Specifies the file type to associate with the file extension Type ASSOC Read More
How to Use the Windows XP Recovery Console
The Windows XP Recovery Console can be used to repair problems which prevent a Windows XP system from booting. Boot Windows XP from CD or Floppy First, boot the computer from the Microsoft Windows XP CD. Before you start the process, go into your BIOS settings and ensure that your CD-ROM drive has the highest drive priority and not the disk drive or some other drive. If you don’t have a Microsoft Windows XP CD, or if the computer you are working on does not have a CD drive, you Read More
How to Change Your Windows Password
Whether you want to change the password on your own computer at home, office computer, or a computer that’s networked with other users, you can easily customize your Windows settings to protect specific files and folders from others either viewing or editing them. Creating or changing the windows password is very simple. It should be noted that changing your password on Windows will differ, depending on whether you are on a stand alone computer or a computer that is connected to a network domain (workgroup). Change your Windows password on Read More
Active Directory Organizational Units
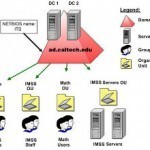
An object is a set of attributes that represents a network resource, say a user, a computer, a group policy, etc and object attributes are characteristics of that object stored in the directory. For example, some of the attributes of a user object might include the user's first name, last name, department, and e-mail address in addition to others. Organizational units act as a container for objects. Objects can be arranged according to security and administrative requirement in an organization. You can easily manage and locate objects after arranging them Read More


Share on: