An Overview on Authorization Authentication is the first step in implementing a security strategy to protect your network resources and elements from unauthorized users, because it is the process that deals with identifying valid authorized network users from unauthorized users. Authentication therefore verifies the identity of users. The next step in securing your network resources and elements from unauthorized access is authorization. Authorization is the process that controls which objects an authenticated network user can access. Just because a user is authenticated, does not necessarily mean that the particular user Read More
How to Use Powerpoint
What is Powerpoint? Powerpoint is a powerful program that comes with Microsoft Office. Powerpoint allows users to create animations, presentations, and slideshows for lectures, home movies, meetings, and other purposes. Powerpoint includes a wide variety of tools, features, and special effects that make powerful and entertaining presentations easy to create. With this software, users have the ability to modify virtually every aspect of their presentation, including text options, color schemes, and placement of objects such as videos and pictures. Users also have the ability to create an unlimited number of Read More
How to Send a Fax via Outlook Express
You can send a fax through Microsoft Outlook with a few simple, easy steps. Unfortunately, if you have Microsoft Outlook Express, you need special software to be able to send a fax. There are several software programs available online. Here are some of the top programs you can use. Mighty Fax Mighty Fax is one of the worlds most popular and user-friendly Windows fax software programs available today. Mighty Fax lets you send and receive faxes directly from Microsoft Word or any of your other Windows programs without the need Read More
Troubleshooting VPNs
Troubleshooting VPN Services Overview Troubleshooting VPNs typically encompass troubleshooting of the following configuration settings, or aspects of your remote access strategy: IP connectivity. Setting up of remote access connections IPSec IP routing To create VPN connections, there are a few requirements that have to be met: VPN services need to be enabled on the server. VPN client software has to be installed on the VPN client. A VPN client utilizes the Internet, tunneling and TCP/IP protocols to establish a connection to the network The server and client have to be Read More
Error 1327 Invalid Drive
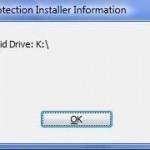
Error 1327 invalid drive can be triggered on a Windows computer when installing software that refers to a nonexistent drive, or when a computer attempts to reference the home drive’s default “H” drive when Windows Enterprise is installed. If the “H” drive is neither accessible nor installed on the computer, the software being installed would be looking for operating system components that are not in an expected location, therefore the error is triggered. Unfortunately, error 1327 cannot be corrected by disabling the non-existent drive via the computer’s Control Panel and Read More
What is a Hackintosh?

Hackintosh is a hacked PC that runs on MAC OS X OS (“Lion”, “Snow Leopard” , “Leopard”). At first, a lot of people thought that this was impossible to run MAC OS on a non-MAC hardware because of the different software, drivers, and utilities being used between the two. It all started when Apple decided to switch to Intel’s processors and chipsets instead of their PowerPC architecture. They were able to build a Boot Camp feature in Mac OS X Leopard which allowed them to run Windows on their Apple Read More
How to Make a Table in Excel

Microsoft Excel is one of the most established spreadsheet programs on the market. A common task that arises is creating a table in Excel in order to manage and analyze related information. Once a table is created, the information can be sorted, filtered, or queried to identify trends and create graphical representations between variables. How to Make a Table in Excel Step 1 – Double click the Microsoft Excel program icon on the computer desktop or choose the shortcut from the computer’s “Program Files” menu to open Microsoft Excel. Step Read More
How to Find a Windows XP Product Key
The Windows XP Product Key is necessary if the user wants to install or reinstall Microsoft Windows XP onto his/her computer. This key is a security tool designed to stop counterfeiting and software piracy. The Windows XP Product Key is necessary for installation and reinstallation, so the user must have the Product Key available for use. If the user purchased his/her computer from an OEM (Original Equipment Manufacturer) such as Dell or Sony, a Windows XP Product Key should be easily found on a sticker on the computer, Windows XP Read More
Analyzing Organizational Requirements for Network Infrastructure Planning

Determining Information Flow Requirements To determine the information flow of the organization, you need to include a number of factors, of which the main ones are listed below. Accessing data or information should be one of the main concerns when planning the network design: The data that needs to be accessed by users. The location of users. The time period when users need to access data. The method by which users access data. A few typical questions which you should ask when determining information flow of the organization are: How Read More
WINS (Windows Internet Name Server)
In the Windows Server family, the primary means for client computer to locate and communicate with other computers on a internet Protocol (IP) network is by using Domain Name System (DNS). However, clients that use older versions of Windows, such as Windows NT 4.0, use network basic I/O system (NetBIOS) names for network communication. Some applications that run on Windows Server 2003 may also use NetBIOS names for network communication. Using NetBIOS names requires a method of resolving NetBIOS names to IP addresses. One can implement Windows Internet Name Service Read More


Share on: