Scan Disk is one of the most common maintenance tools bundled with an operating system such as Windows. This is an application that checks the computer’s hard drive for errors and bad sectors. Once Scan Disk finds an error in the hard drive, it will attempt to fix it. There are a number of reasons for the errors found inside a hard drive. These include: frequent system crashes critical system applications that have been improperly closed the existence of harmful programs such as viruses, trojans, etc. What Does Scan Disk Read More
How to Restore a Deleted Recycle Bin

The Recycle Bin icon is one that sits on the desktop of most Windows based operating systems. The Recycle Bin’s purpose is to offer simple access to items that were deleted to either: A. Free up space so that new information can be saved on the hard disk, or B. Restore items that were accidentally deleted. Sometimes a Recycle Bin can be deleted accidentally or removed by malicious software. Access to the Recycle Bin functions is not entirely disabled when this happens, but it takes additional steps to get to Read More
Understanding and Implementing Smart Card Authentication
An Overview on Authentication and Smart Cards Administrators have to secure the network from attacks launched by hackers, spies, terrorists, thieves and criminals. Security encompasses numerous technologies, protocols, standards, policies, passwords, and secret keys. All these mechanisms typically focus on the following: Authentication Access Control Data Protection Auditing/Accountability Authentication is the process by which an entity identifies itself, before network logon is permitted. After a user is authenticated, access control defines what resources can be accessed, what actions can be performed on the resource, and whether these actions are audited Read More
How to Read Windows Log Files
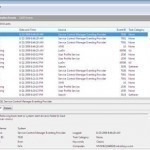
Reading Windows log files is an important part of maintaining proper operation and ensuring system security. In addition, log files can be extremely useful in troubleshooting Windows errors. Only a Windows Administrator can read some Windows log files, such as the Security Event Log. Any system user can view other log files, such as logs that software applications created. Each log contains a list of events that occurred, along with problems, failures, and warnings. How to Read the Windows Application, Security, and Sytem Log Files The Windows application, security, and Read More
Bad_Pool_Header
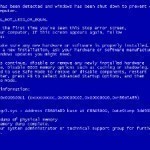
One of the most famous fatal errors that occurs on computers running the Windows Operating System (OS) is the Blue Screen of Death (BSOD). A BSOD may be the result of a number of problems including hardware, software, or driver incompatibility with the computer’s OS. The BSOD often prevents users from rebooting their computer or using it normally. One common BSOD error that occurs is the Bad_Pool_Header. When this error occurs, the OS will not load and users will not be able to access the information stored on the NTFS Read More
Implementing Account and Security Policies
Understanding Security Policy Types With Windows Server 2003, you can implement and manage security settings at the following levels: Local computer (local security policies) Active Directory site, domain, or organizational unit (domain security policies) Local security policies are managed through Local Computer Group Policy Objects (GPOs), and domain security policies are managed through Group Policy with the Active Directory Domain Controller GPOs. However, domain security policies override local security policies. In Windows Server 2003 Active Directory environments, group policies include configuration settings for the following: Software policies Scripts Security policies Read More
Implementing Windows Cluster Service
Planning for a Cluster Service Implementation A number of factors have to be determined when you plan for your Cluster Service implementation. A few items which you should include in your planning phase are listed here: Determine which applications and network services are the mission-critical applications of the organization that need high availability. Determine which clustering technology to implement that would ensure high levels of availability for the mission-critical applications previously identified. Here, you should identify those applications which should be used with Cluster Service, and those applications which should Read More
How to Make a Schedule in Excel

Microsoft Excel is commonly used to make a chart or spreadsheet, calculate formulas, generate time sheets or calendars, and make agendas. Many people do not realize that Excel is also great for keeping organized. One can use Excel to make a work schedule for employees or a personal schedule to keep one’s self on track. Excel can also be used to create a reminder about specific dates, appointments, and any type of schedule that one may need. Excel schedules can even be made to keep track of the dates and Read More
0xc0000135
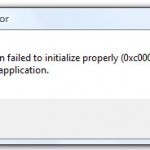
Windows error 0xc0000135 is displayed when an application fails to initialize properly. It is also displayed when a new program, game, or plug-in is installed and fails to work properly due to the wrong version of .Net being installed on the computer or as a result of a computer malware infection. Is the .Net Environment Always Installed on a Windows Computer? The .Net environment is not installed by default on the Windows XP Operating System. .Net 3.0 is installed by default on Windows Vista but may be too old to Read More
How to Make Desktop Icons
Desktop Icons are some of the necessary files that are required to spice up and personalize folders, shortcuts and programs on your computer. There are many options available to produce icons from multiple sources including photos, graphics and can even be made from scratch with drawing tools. There are several free desktop icon makers available on the Internet. One of the free options that work very well is IcoFX, which is available at the www.icofx.ro website. Making Desktop Icons Using Free Software Options If you are using IcoFX, you will Read More


Share on: