Getting the “Your System is Low on Virtual Memory” error is very frustrating. Fortunately, it will not destroy the computer. It merely indicates that the computer no longer has any memory to run the process requested and is trying to use virtual memory, but even that is running low because the program requires too much. This typically happens when numerous programs are being run or a program that has a glitch in it is running. Virtual memory (file swap or page swap) is a file on the hard drive. Its Read More
Troubleshooting IIS
Understanding HTTP Error Messages HTTP error messages are related to the HTTP status codes which are included in the response headers when pages are requested from the Web server. HTTP status codes are three digit numbers. HTTP status codes are categorized into the following categories: Informational (1xx): This category is used for testing, and is not used for production Web servers. Successful (2xx): Indicates that requests were successfully received. Redirection (3xx): Indicates that the client needs to perform additional steps for his/her request to be serviced. Client Error (4xx): Indicates Read More
Securing Web Servers
Web Server Security Issues Internet Information Services (IIS) is the Microsoft Web server provided in each Windows Server 2003 Edition. Internet Information Services (IIS) 6.0 was designed as the solution for intranets, extranets, and the Internet. Through IIS, organizations can implement Web sites and applications, and Web services. IIS supports Secure Sockets Layer (SSL) version 3. SSL is used to encrypt HTTP and NNTP authentication data and transmission data through public key cryptography. IIS also supports Transport Layer Security (TLS), which is used to encrypt SMTP data transmissions. Basic security Read More
NTLDR
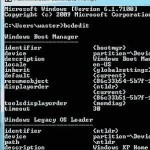
A boot loader is a special program whose purpose is to load other software and files that are required to bring the computing system into a ready-to-run state. NTLDR is an abbreviation for New Technology Loader, and it is the boot loader for all the releases of Microsoft’s Windows NT operating system up to Windows Server 2003 and Windows XP. In Windows Server 2008 and Windows Vista and Windows 7, NTLDR has been replaced by Windows Boot Manager and winload.exe. A boot loader usually resides in the nonvolatile portion of Read More
Managing Recipient Objects, Address Lists, and Distribution and Administrative Groups
Recipient Objects Overview Active Directory objects such as user accounts, contacts and groups become recipient objects when e-mail address information is added to the object. The public folder is another type of recipient object. A public folder does not however usually have its own an email address. Exchange Server 2003 supports the following types of recipient objects: User recipient objects: This recipient object type is created and managed using the Active Directory Users And Computers management console. User recipient objects are associated with the user accounts in the Active Directory Read More
BOOTMGR is Missing
The BOOTMGR (Windows Boot Manager) is part of Microsoft Windows Vista, Windows Server 2008, and Windows 7. It finalizes the steps in booting the computer and loading the Operating System by looking for the active partition in which Boot Configuration Data is stored. BOOTMGR runs the “winload.exe” process in order to do this. This process is essentially the operating system boot loader that loads the operating system kernel and device drivers that are in the boot-class.Small changes can easily corrupt the BOOTMGR configuration on Vista, Server 2008, and Windows 7. Read More
How Vista File Sharing works
File sharing is a necessity when there is a network. Whether it is the Internet or an intranet, people are sharing files all the time. It helps businesses function at an optimum level as people can share any information they want. File sharing makes files available for others to use. This is accomplished in many ways. In business networks it is done via file servers, on the wider Internet it is done via the peer-to-peer (P2P) model, in which the files are received, stored, and served by the personal computers Read More
TCP/IP
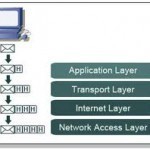
Understanding the Function of Protocols Protocols are rules, standards and procedures that enable information to be communicated in the network environment. The rules and standards that control the way in which computers communicate are referred to as protocols. A few relevant factors to consider when discussing protocols and the network environment are: There are numerous protocols Each protocol has a specific set of functions that assist in enabling communication over the network. The layer of the OSI reference model at which the protocol operates indicates its function. Certain protocols can Read More
How to Set an Environment Variable
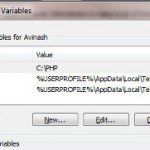
An environment variable is a variable that describes the way a computer environment, such as an operating system, works. Environment variables can be used to manage a wide variety of environment settings and control how functions are carried out. For example, an environment variable can be used to specify the directory in which temporary files are stored or the functions a user interface tool is able to perform. How Environment Variables Work Environment variables are integrated into any software’s script before the software is released. Since environment variables control Read More
Understanding and Designing a Public Key Infrastructure
An Introduction to the Public Key Infrastructure (PKI) It has grown more important to ensure the confidentiality and integrity for data communication where an organization's network contains intranets, extranets, and Internet Web sites. Because of the connectivity of networks today, an organization's network is exposed to unauthorized users who could possibly attempt to access and manipulate mission critical data or the confidential data of its clients. The need to authenticate the identities of users, computers and even other organizations, has led to the development of the public key infrastructure (PKI). Read More


Share on: