Opening TCP ports in Windows may be necessary for certain applications to run correctly. Each application may require a specific port to operate on. While a computer can and does open ports on its own, it may have to be done manually in certain situations. Here is a simple procedure. Step 1. Launch Windows and click Start, then My Network Places. A new window should pop up. Select Network Tasks then click View Network Connections. Step 2. Select the connection used for the Internet. If unaware of the connection that Read More
Windows Mobile
For the Internet user on the go, modern mobile computing devices have been a welcome addition to technology manufacturer's line of products. Devices such as PDAs (Personal Digital Assistants) and smart phones have exploded in popularity in recent years. These devices now offer a wide range of features in ever-increasingly compact models. These features typically include web browsing, email, RSS feeds, and incorporated mobile phones. Windows Mobile is the name Windows assigns to its line of operating systems devoted solely to mobile computing devices. Windows Mobile began with the popular Read More
How to Fix Runtime Error R6025
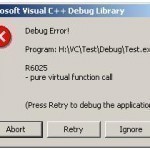
Even though the Microsoft Windows operating system (OS) is one of the most used in the world, computer users may encounter the Runtime Error R6025. The error results from a program or application becoming corrupted. After the error is thrown, the application causing the problem must be deleted and reinstalled in order to clear the error from the Windows OS. How to Fix Runtime Error R6025 Step 1 – Exit the program that triggered the R6205 runtime error by clicking the “X” in the upper right hand corner or clicking Read More
What Are Dynamic Disks?
What are Dynamic Disks A dynamic disk refers to a hard drive that can be altered at any time to include additional partitions or volumes. This differs from basic disks that only include standard and extended partitions that are setup when the disk is first formatted. Dynamic disks can handle all of the following volumes. Simple Volumes A simple volume refers to the standard volume in which computers often work with. A simple volume is basically a folder on a hard drive that holds all of the user's information. For Read More
Data Error Cyclic Redundancy Check
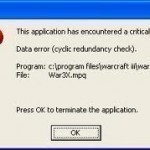
The “Data Error Cyclic Redundancy Check (CRC)” is a problem with the mathematical process the computer does in order to ensure that data is properly transferred from a particular source to a specified destination. During the cyclic redundancy check, the computer determines if the data being transferred is not damaged. When users get a “Data Error Cyclic Redundancy Check” message, this could very well mean that the data they are transferring is corrupted. Often times, users encounter “Data Error Cyclic Redundancy Check” while attempting to read and/or copy data derived Read More
How to Uninstall Windows Media Player
Windows Media Player has been deployed with all installations of the Microsoft produced Windows Operating System for the past decade. The current versions of the application mix in social media sharing applications along with the ability to watch movies and listen to music. Although Microsoft has expanded the “friendliness” of Windows Media Player with non-proprietary multi-media file formats in recent versions, many users will have the desire or need to remove the player from their computer. Unfortunately, it is not a straight forward task to remove the player like it Read More
Novell Netware and Windows Server
Interoperating with Novell NetWare Windows Server 2003 includes a few specific services that enable Novell NetWare servers and clients, and Windows computer to interoperate: NWLink IPX/SPX/NetBIOS Compatible Transport Protocol (NWLink): NWLink IPX/SPX is the Microsoft implementation of Novell's NetWare Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX) protocol. NWLink IPX/SPX is simply called NWLink. NWLink is used in Novell NetWare, and can be considered IPX for Windows. NWLink is an IPX/SPX compatible transport protocol that was developed to enable Windows 2000 computers to communicate with NetWare services. It is therefore used when Read More
Blue Screen of Death
If you have been working on computers or are just starting to use them, one of the most disturbing events that can occur is the BSOD or Blue Screen of Death. The BSOD is actually an error screen that is displayed by specific operating systems informing the user that a critical system error has occurred. The Blue Screen of Death can be found on many different types of operating systems, but is most notably infamous for occurring on Microsoft Windows Operating Systems. Common Causes of the Blue Screen of Death Read More
How to Limit Internet Access in Windows XP User Accounts

User accounts allow Microsoft Windows to differentiate between computer users in order to determine the rights they should have. Each user account is assigned its own location on the hard disk for file storage. There is a collection of settings pertaining to each account that is stored in the computer’s Registry. Methods for Limiting a Windows XP User Account’s Internet Use Windows SteadyState Windows SteadyState is a free, discontinued Microsoft product that can still be downloaded from many online sources. It allows users to make changes to how their computer Read More
Migrating from Exchange 5.5 to Exchange Server 2003

Differences between Exchange 5.5 and Exchange Server 2003 Environments Exchange version 5.5 worked well in smaller organizations. Exchange 5.5 deployments typically consisted of Exchange servers being at each remote location, and with no more than thirty users. The main Exchange 5.5 design limitations are summarized here: The degree of stability offered by Exchange 5.5 is open to discussion. Exchange 5.5 stability was typically realized through the following means: Keeping public folders and message routing isolated from the mail-message services. Keeping the size of the Databases small. With Exchange 5.5, designs Read More


Share on: