Set focus on a notification. Windows Key+B View properties for the selected item. ALT+ENTER Open the next menu to the left, or close a submenu. LEFT ARROW Collapse current selection if it's expanded, or select parent folder. LEFT ARROW Display the items in the active list in a dialog box. F4 Refresh the active window. F5 Cycle through screen elements in a window or on the desktop. F6 Display the top of the active window. HOME Switch MouseKeys on and off. Left ALT +left SHIFT +NUM LOCK Switch High Contrast Read More
How to Run as Administrator
Running as administrator simply means that you are in logged into your Microsoft Windows computer as the administrator role which has the ability to install programs and do anything else. The administrator is the account that can make all changes to the computer. However, security experts warn against running in an administrator account because if a virus gets into the computer, it typically functions off of a permission based system. In other words, because the administrator can do anything on a computer, a virus can execute anything if it comes Read More
Creating and Managing Access Policies in ISA Server
Access Policies Overview Protocol rules and site and content rules determine access policy in ISA Server: Protocol rules define which protocols clients can use to access the Internet. Site and content rules define which sites and content can be accessed. Because no protocol rules are defined and applied when you install ISA Server, traffic will not be able to pass through. Packet filters are used to manage the flow of IP packets to ISA Server and from ISA Server. Packet filtering inspects the header of each packet for protocol, port, Read More
Understanding Trust Relationships
In the Windows NT domain model, domains had to be bound together through trust relationships simply because the SAM databases used in those domains could not be joined. What this meant was that where a domain trusted another Windows NT domain, the members of the domain could access network resources located in the other domain. Defining trust relationships between domains eliminates the need for an Administrator to configure user accounts in multiple domains. In a trust relationship, the two domains are referred to as the trusting domain and the trusted Read More
Restoring Exchange Server 2003
Documenting your Exchange Server 2003 Environment To successfully restore or recover any aspect of your Exchange Server 2003 environment, it is important that you document the following: The Exchange Server 2003 environment. The backup process. The recovery process. A well documented or complete Exchange Server 2003 environment document should include the following information: The Exchange server name. The Windows version and service pack running on your servers. The Exchange version and service pack running on your servers. The Exchange organization name. Site names. Database names and sizes. Database locations. Storage Read More
How to Solve “Windows Installer Service Could not be Accessed”
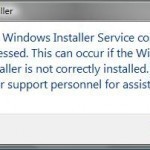
Windows Installer is a very important component of all Windows operating systems. It installs, uninstalls, and supports applications and software. If the Windows Installer is corrupted or the service stops for an unknown reason, an error message comes up. The error message typically appears as: “The Windows Installer Service could not be accessed. This can occur if Windows is running in safe mode or if the Windows Installer is not correctly installed. Contact your support personnel for assistance.” The error message may happen when Windows XP is in Normal mode Read More
How to Remove Programs from Startup
A common problem that most owners of Windows computers experience is that the older the computer, the longer it takes for it to start or boot. Typically this condition results from a large number of programs being installed on the computer over time that are configured to be started on-boot of your computer. Although you may use a number of these applications, free-trial programs that you may no longer use will continue to be in the start-up listing of programs on your computer until removed. Another scenario that occurs for Read More
Developing a Test Network
Planning the Test Network Environment Any successful network design deployment includes a testing strategy, and the execution of the testing plan. To test the network design, you have to plan the test network or environment, and then create the test network. A testing environment can contain one lab or multiple labs. You can build various labs to test specific components within the network design. When planning your test environment, take time to create an environment that can prove whether or not the network design being tested is effective. You should Read More
Backing Up the Exchange Server 2003 Environment
Understanding the Data Types to Back Up There are a number of reasons why Exchange data should be backed up: To provide protection in the event of a system crash. To be able to recover corrupt databases. To be able to recover the following: Mailboxes. Folders. Messages. To restore Exchange in a lab for testing. The different types of data that should be backed up can be classified as follows: Static data: Consists of data that hardly ever changes: Windows Server 2003 operating system software. Software updates and service packs. Read More
How to Uninstall Microsoft Office
Microsoft Office has been one of the leaders of commercially available desktop bundles of productivity programs for the past two decades. Despite the popularity of the application suite, a number of computer users have made the shift to open solutions such as Open Office which provide equivalent performance for little to no cost. Once users are able to make the shift to a compatible alternative to MS Office, a common problem that arises is how to uninstall Microsoft Office. Automatically Uninstall Microsoft Office on Windows The first place to start Read More


Share on: