In comparison to the logical structure, which performs administrative tasks, the Active Directory physical structure checks when and where logon and replication traffic occurs. The physical structure of Active Directory contains all the physical subnets present in your network like domain controllers and replication between domain controllers. The physical structure of Active Directory: Domain Controllers: These computers run Microsoft Windows Server 2003/2000, and Active Directory. Every Domain Controller performs specific functions like replication, storage and authentication. It can support maximum one domain. It is always advised to have more than Read More
How to Fix Error 0x80070570 in Windows 7
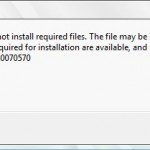
Error 0x80070570 is an error message that is displayed in Windows 7 whenever a file or folder is corrupted or unreadable, especially files in the Windows Registry. Because these files are important to the computer’s performance and are a necessary component for processing routine tasks, a corrupted or unreadable file can cause the user’s computer to stop working properly or interfere with specific programs. What Causes Error 0x80070570? A wide variety of activities, the most common being a malicious software attack, can cause Error 0x80070570. Additionally, moving a file Read More
How to Register a DLL
Dynamic Link Library files or DLLs are libraries of computer code and data that are used as shared resources on computers running the Windows Operating System (OS). A common task that arises for home computer users is figuring out how to register a DLL to allow the desired computer software to operate properly. The act of registering a DLL updates the Windows registry with the location and capabilities store in the file to permit proper application execution. The two options available to complete this task are through self-registration or manual Read More
How to Change the Taskbar Font
The Windows Taskbar is not only an extremely practical feature of Windows operating software, but it can also be customized to fit your specific preferences. Here is how: Start your computer and right click on any clear space (do not click on the taskbar or any icons). You should see a menu appear. In this context menu, select Properties and a new window should appear. Select the option for Appearance. Click on the Active Title Bar which should be located on the drop down menu. From here, you can easily Read More
Global Catalog in Active Directory
Domains and Forests can also share resources available in active directory. These resources are searched by Global Catalog across domains and forests and this search is transparent to user. For example, if you make a search for all of the printers in a forest, this search goes to global catalog server for its query and then global catalog returns the results. Without a global catalog server this query needs to go to every domain in the forest of its result. It is important to have a global catalog on at Read More
ntuser.dat
An Ntuser.dat file is a Windows Operating System registry file that contains preferences and settings for each user account on a computer. Each user account has its own unique Ntuser.dat file, which Windows references to display the Start Menu, desktop icons and background, Documents folder, browsing history, and other personalized configurations. Ntuser.dat files can be found in the Documents and Settings folder, but should not be removed under any circumstances. How Ntuser.dat Works An Ntuser.dat file is essentially a log file that contains the user’s preferences, settings, and configurations. Read More
Managing Exchange Server Connectivity Across Firewalls
Using Firewalls To Prevent Unauthorized Access The method, by which you can physically secure the network, is through the usage of firewalls. While firewalls provide some level of physical security, you should bear in mind that firewalls are just barriers which make it difficult for intruders to attack the network. Firewalls are categorized as follows: Network firewalls: These firewalls monitor traffic entering and exiting the network, in an attempt to protect the perimeter network. Software based Microsoft Internet Security and Acceleration (ISA) Server and the hardware based Nortel Networks Alteon Read More
Using SMS Diagnostic and Troubleshooting Tools
Status Messages Overview All SMS 2.0 components and services generate status messages as they perform their various functions. These status messages illustrate the movement of processing activity of the SMS site systems and clients. The status messages are automatically summarized for viewing through status summarizers and filtered through status filters. A status message can have one of the following severity levels: Informational status messages: These messages merely inform on events such as a component starting, and a task completing. Warning status messages: These messages point out potential problems that can Read More
Using IIS Command-Line Utilities to Manage IIS
The Types of Commands used to Manage IIS from the Command Line The types of commands that manage IIS from the command line are: IISReset, Windows Management Instrumentation (WMI) scripts, Active Directory Services Interface (ADSI), and the standard Windows commands and Support Tools utilities. IISReset Command-line Utility IISReset is a command-line utility that has been in existence from IIS 5 that can be used to stop IIS, restart IIS, and reboot the IIS server. Typical reasons for restarting IIS are: When problematic ASP.NET and ASP applications exist and resource leaks Read More
Publishing Resources in Active Directory
What Resources can be published in Active Directory When you make Active Directory objects available to users, you are publishing the Active Directory resource. The resources that can be published in Active Directory include the Active Directory resources listed below: User objects Computer objects Printer objects Folders and files Network services The two primary published objects are printers and shared folders. Publishing information on shared network resources such as printers, folders, and files; eases the process of users locating these resources. Having resource information in Active Directory makes it easy Read More


Share on: