Determining Security Business Requirements When analyzing and determining the security business requirements of the organization, you have to include the following factors: Business model: The business model that the organization uses greatly influences the type of security an organization implements. An organization that has world-wide branches would have different security requirements to a business that has a single office. Business processes: To successfully implement security, you have to know how business processes within the organization work. You have to ensure that security does not prevent business processes from being carried Read More
How Microsoft Office 2003 Activation Works
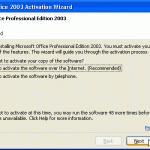
If you have just purchased Microsoft Office 2003, you will be required to activate this product directly with Microsoft. Microsoft product activation is set up as an anti piracy feature. This feature is created in order to verify that your Microsoft 2003 Office suite is not a fake copy and is legitimately licensed to you as the end user. The process of activating your Microsoft Office 2003 is generally quick, easy and anonymous. Below is a step by step process on how the activation process works. Licensing Agreement The activation Read More
Using the Terminal Services Configuration Tool
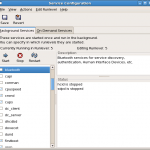
In order for clients to establish Terminal Services sessions on a server, listener connections have to be configured on the particular server. A listener connection can be configured for only RDP (Remote Data Protocol) over TCP/IP. One listener connection can be configured for a network interface card (NIC) in the Terminal Services computer. The Terminal Services Configuration tool creates new listener connections to change configuration settings on existing listener connections and to configure server policy settings. While it is recommended to configure Terminal Services connections through Group Policy, the Terminal Read More
No Audio Device
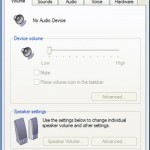
Computers usually display the “No Audio Device Error” message when it does not detect any properly working audio device attached to it. Users will not hear any sound from their computer when this message appears. Only the computer’s internal speaker makes bleeping sounds. When this message appears on the screen, check the computer’s BIOS and ensure that the audio is set to “auto” mode. Also, check if the correct drivers that the audio device attached to the computer needs in order work properly are installed. Audio Device Drivers The most Read More
Deploying Service Packs and Hotfixes
What are Service Packs and Hotfixes Service packs and hotfixes are network updates that need to be applied to network computers. Hotfixes are also sometimes referred to as security hotfixes or security fixes. Before delving into the differences between service packs, and hotfixes; you can think of a service pack as being a collection of updates, or large executable files that relate to an Operating System (OS), and a hotfix as being one or multiple files that are applied to the OS to fix a specific critical problem. Service packs Read More
How to Fix Windows Search
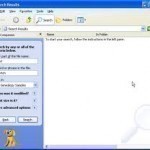
Windows Search (Windows Instant) is a program in the Windows Operating System that allows users to search for specific files, folders, or other remnants of data on one or more hard drives or some other storage device. It allows users to search for customized keywords, specify storage locations, browse for files, and toggle through a multitude of functions. Windows Search is very easy to use, can find virtually any type of file on the user’s hard drive (including emails and data files), and supports natural language, allowing users to enter Read More
Connection Manager
Connection Manager is versatile client dialer and connection software that you can customize by using the Connection Manager Administration Kit (CMAK) wizard. The CMAK wizard provides defaults that support quick and easy creation of a basic Connection Manager service profile. If you want to use all of the defaults and do not want to take advantage of the many customizable elements, you probably do not need this documentation. However, if you want a custom dialer that promotes your brand and supports more advanced functions, such as automatic phone book updates Read More
SSL and IIS

An Overview on Secure Sockets Layer (SSL) With IIS, you can further secure websites by using the Secure Sockets Layer (SSL) encryption technology. SSL was developed by Netscape Communications, and enables secure communication over the Internet. SSL operates at the transport layer of Transmission Control Protocol/Internet Protocol (TCP/IP) protocol suite, and uses public key cryptography to establish a secure SSL session between a Web server and client. A few features provided by SSL include authentication, message integrity, and data confidentiality through encryption. To utilize SSL in IIS, the Web server Read More
Planning and Implementing a DNS Namespace
Host Name Resolution Overview In networks running the TCP/IP protocol suite, IP address information is used to forward packet to the destination computer. The packets that are transmitted over the network contain the IP address of the computer sending the packet; and the IP address of the destination computer intended to receive the packet. The IP addresses of computers therefore have to be both unique and correct so that they can be forwarded to the correct destination. IP addresses contain the network address and the host address. A host name Read More
How to Edit the Registry
How to Edit the Registry The System Registry is a database used by the Windows operating system. It is used to store hardware, software, and operating system options, settings, and configurations. The registry was originally developed in order to decrease the amount of time that the OS would take to look-up settings while the end-user made selections on the computer. The registry also performs a function as a kernel gateway for the OS. Unfortunately, the longer that you own a computer and add or remove programs, the more junk that Read More


Share on: