Authenticating users in IIS is one of the initial steps in securing IIS. When a user attempts to access a website or an FTP site on an IIS machine, authentication is the process that verifies whether the user can indeed access the site. Authentication and permissions are closely coupled. After a user is authenticated, NTFS permissions determine whether the user can access folders and files and Web permissions indicate whether a Web or FTP client can read the website’s home or virtual directory. The authentication methods that authenticate users in Read More
Compile Error in Hidden Module
When starting up Microsoft Word or Excel (or other Office products), the “Compile Error in Hidden Module” issue may arise. Starting up the program will prompt the error message to appear and display one of the following or a similar message: Compile error in hidden module: AutoExec Compile error in hidden module: AutoExecNew Compile error in hidden module: DistMon Image: Example of Error Message in Excel In the versions of Microsoft Windows 95, 98 and ME, the following error message may be displayed instead: Excel has performed an Read More
Understanding IIS 5.0 and IIS 6.0
An Introduction to Internet Information Services (IIS) Microsoft's integrated Web server, Internet Information Services (IIS) enables you to create and manage Web sites within your organization. It allows you to share and distribute information over the Internet or intranet. With Windows 2000 came Internet Information Services (IIS) 5.0 which was basically the fastest Web server at the time when Windows 2000 Server was introduced. IIS 5.0 was fully integrated with the Active Directory directory service. Because of this integration, and the additional features and enhancements introduced with IIS 5.0 you Read More
Configuring Power Management
An Introduction to Power Management and its Features Power management is a component of system performance that affects how Windows makes use of power when the computer is running under normal conditions. You can use the Power management settings to preserve energy. This in turn extends the life of hardware components of the system because they are powered down during periods when there is no user activity. The power management feature is extremely beneficial for laptop users. Microsoft Windows XP and OnNow capable computers can manage the power of a Read More
How to Speed Up Vista
When it comes to computer performance, speed is all-important. Vista is the newest and most technologically advanced operating system ever released by Microsoft. Vista is quite streamlined and tuned for performance. However, for those who want the fastest speed possible, there are some tweaks that can be applied. Here are some of the most effective ones available. Update Drivers Drivers are small programs that run computer peripherals or applications. Whether it is a driver to run your printer or virtual media player, having the most current driver will enhance the Read More
Backing Up and Restoring the WINS Database
Protecting the WINS database To protect your WINS databases from disasters and corruption, you should regularly back up your WINS databases. The methods which you can use to back up the WINS database are: You can use the WINS console to perform: A manual back up of the WINS database Schedule an automatic backup of the WINS database. You can use the ntbackup.exe utility to back up the WINS database. The Windows Server 2003 Volume Shadow Copy feature allows you to back up the WINS database while it is online. Read More
Implementing Public Key Infrastructure
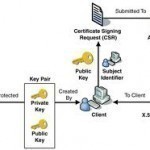
An Overview on the Public Key Infrastructure (PKI) A set of components, standards, and protocols make up the Public Key Infrastructure (PKI), which protects data as it is transmitted over the network. The PKI is an integral aspect of security within a network. Digital certificates form the basis of the PKI because these certificates use cryptographic algorithms and key lengths to protect data as it is transmitted over the network. The more important components of the PKI are summarized below: Cryptographic components are the encryption and hashing algorithms that are Read More
NTFS Permissions
An Overview of NTFS In order to store data on a local partition on a Windows server, you have to format it with a file system. The system that you use influences the manner in which data is stored on the disk. It also specifies the security that can be defined for folders and files stored on the partitions. Although Windows servers offer support for the File Allocation Table (FAT) file system, NT file system (NTFS), and CDFS (Compact Disc File System), the file systems generally utilized by local partitions Read More
Understanding DNS Queries and Lookups
DNS Queries Overview The naming system used by DNS is a hierarchical namespace, called the DNS namespace. The DNS namespace has a unique root. The root can contain numerous subdomains. Each subdomain also can contain multiple subdomains. Each domain registered in DNS is connected to a DNS name server. The DNS server of a domain provides authoritative replies to queries for that particular domain. The DNS server manages the DNS database that resides on it. DNS server is authoritative for the contiguous portion of the DNS namespace over which it Read More
How to Clean a Hard Drive
A hard drive refers to the main storage device for any computer system whether it be a desktop computer or handheld device. Hard drives are usually about the size of a small, paperback book and can exist in both internal and external models. Internal hard drives are usually connected to the computer via an IDE cable while external hard drives use a USB or FireWire cable. Regardless of what kind of hard drive it is or how much information it can hold, all hard drives must be maintained in order Read More


Share on: