Connection Manager Overview If you want to configure clients to connect to a RRAS server, you can use the Connection Manager to do this. Using the network connection properties to configure clients to connect to a RRAS server works well in situations where you need to configure a small number of clients, and when the default security settings are being utilized. Connection Manager is a Windows application and client dialer included in Windows 2000, Windows XP Professional, and Windows Server 2003 that you can use to allow a client to Read More
Understanding Volume Shadow Copies
Volume Shadow Copies Overview Volume shadow copies, a new Windows Server 2003 feature, are used to create copies of files at a specific point in time, or set time interval. Shadow copies can only be created on NTFS volumes to create automatic backups of files or data per volume. When enabled, the Shadow copies feature protects you from accidentally losing important files in a network share. Remember that when users delete files from over the network, those files are permanently deleted. Because shadow copies enable users to view previous versions Read More
Using the Terminal Services Manager Tool
The Terminal Services Manager tool (Tsadmin.exe) is the main administration tool used to manage existing Terminal Services sessions, users, and processes that are connected to or running on the Terminal Services server. The Terminal Services Manager tool can manage one or more Terminal Services servers. The administrative tasks that the Terminal Services Manager tool can perform are listed below: View information on existing Terminal Services servers, users, and any connected or running sessions and processes. Connect and disconnect from sessions. Terminate existing sessions and processes. Log off users from sessions. Read More
ExFAT
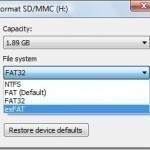
The Microsoft Corporation in conjunction with Windows Vista Service Pack 1 (SP1) released the exFAT file system. The exFAT file system was produced in order to address the short comings of the FAT32 file system; specifically on portable media such as USB sticks or portable hard drives where NTFS file structure use is inappropriate. The exFAT file system is also referred to as FAT64 in some circles. The Microsoft Corporation has a patent pending, which will require licensing for the use of the format. The exFAT structure is supported on Read More
Configuring Outbound Internet Access with ISA Server
Understanding ISA Object Permissions You can assign permissions for a number of ISA Server objects, such as those listed here: ISA server H.323 gatekeeper ISA Server arrays Enterprise polices Sessions Alerts The ISA Management MMC snap-in is used to assign permissions for ISA Server objects. The ISA Management console is the primary tool used to administer ISA Server. To assign ISA Server object permissions: Click Start, click Programs, click Microsoft ISA Server and then click ISA Management. To connect to the ISA server, click the Internet Security And Acceleration Server Read More
How to Play DOS Games under Windows
MS-DOS (Microsoft Disk Operating System) has many enjoyable game software titles that may not be playable on Microsoft Windows without having a few changes made to their configuration. Try the following options in order to play a DOS based game on a Windows Operating System: Compatibility Settings In Windows, compatibility may be possible with some DOS titles. The process requires having the ability to install the DOS game from the install media or having the game files available to be launched through explorer. Go to the installation directory for the Read More
Task Manager Has Been Disabled By Your Administrator
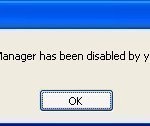
Computer malware has evolved at a rapid rate in recent years. A common trend among the fake anti-virus programs that the Trojan virus deploys on the Internet is disabling the computer’s Task Manager. The associated virus does this in order to make it more difficult to remove infections from computers. When this happens to a computer, the registry editor must be used to remove the malware. Depending on the nature of the computer infection and the configuration of the Windows computer, several methods can be used to repair the problem. Read More
Monitoring and Tuning ISA Server Performance
Tuning ISA Server Performance You can optimize ISA Server performance and tune the ISA Server cache. The ISA Server performance settings that you can tune to optimize the performance of the ISA Server computer exist on the Performance tab of the Array Properties dialog box. ISA Server caches objects to RAM and on disk. The default ISA Server configuration caches objects that are below 12,800 bytes in size in RAM. An object that is stored in RAM is retrieved faster by ISA Server than an object which is stored on Read More
Error 1068 the Dependency Service or Group Failed to Start
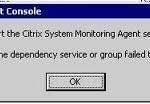
Although it has been significantly easier to add and remove new printers on the Windows Operating System (OS) since Windows XP’s release, PC users still encounter Error 1068. This error also states that a dependency service or group failed to start, which may include the print spooler. When this error occurs, the user has to manually restart the computer’s print spooler in order to correct the problem. The print spooler program is used to transfer the data for the document/image to be printed to the user’s or network’s printer memory. Read More
Implementing Internet Connections

E-mail and Web sites have evolved into being important mechanisms for a vast number of organizations. Internet connectivity or connections support a company’s business in a number of ways. Company employees use the Internet to exchange e-mail with other employees at different branch offices, and with business partners and suppliers; to access the LAN when working from home; to conduct research using the Web; and mobile users utilize the Internet to remotely access the LAN. Each organization would have different requirements when it comes to Internet connections. Some organizations might Read More


Share on: