On Overview on Group Policy Object (GPO) Implementation and the Group Policy Object Editor Group Policy settings are stored in a Group Policy Object (GPO). The types of Group Policy settings which can be stored in a GPO are listed below: Computer configuration settings are located in the Computer Configuration node. User configuration settings are located in the User Configuration node. A Windows 2000 and Windows Server 2003 computer has a local GPO. A local GPO exists only on that particular computer, and therefore only affects the computer on which Read More
How to Activate Windows 7
Activating Windows 7 is different than registering Windows 7. When you register, you let Windows know you exist so they can add you to their roster. When you activate Windows 7, you verify that the copy you have is legal. In other words, you punch in a key code that lets Windows know that you purchased a legal copy rather than getting a pirated copy. It's necessary to activate because if you don't, you won't have access to all of the Windows features after thirty days. You can activate two Read More
Configuring and Maintaining Exchange Server 2003 Virtual Servers
Configuring Exchange Virtual Server Settings Exchange System Manager can be used to create new Exchange Server 2003 virtual servers. A Protocols container exists below each server object. Expand the nodes in the console tree of Exchange System Manager to view this. Each Internet protocol is signified by a different container. Any related virtual protocol servers are bundled together. To add a new virtual server, right click on the particular protocol container, select New, and then select the associated Virtual Server command. A unique IP address and name has to be Read More
Blue Screen Stop 0x00000024
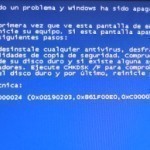
Blue Screen Stop 0x00000024 refers to a BSOD (Blue Screen of Death) error message that is displayed whenever there is a conflict with the NTFS.sys file, which is the file responsible for reading and writing to NTFS hard drives. A number of problems can cause this error, with the most common reason being that the user’s hard drive has failed or has become corrupted. What Causes Blue Screen Stop 0x00000024? While it is possible that software that is incompatible with NTFS systems can corrupt or negatively impact the NTFS.sys Read More
Planning an Exchange Server 2003 Infrastructure
Understanding the Different Combinations of Exchange and Windows Server The different supported combinations of Exchange and Windows Server are listed here: Exchange Server 5.5 is supported on the following Windows versions: Windows NT 4 Server. Windows 2000 Server. Can only replicate data to Active Directory and from Active Directory through the Active Directory Connector (ADC). Exchange 2000 Server is supported on the following Windows versions: Windows 2000 Server with Service Pack 1 or higher. Reliant on Active Directory. Can be installed on a member server or on domain controller. Exchange Read More
How to Make a Timeline on Microsoft Word
A timeline is a tool used in a visual presentation in order to present data or unique events in a sequential fashion over a defined time frame. In the past, unique programs such as the Adobe or Corel tool suites were the only programs available to individuals capable of creating a professional product. Microsoft Word is capable of creating a timeline that can be used on business or school presentations at the same level as Adobe and other professional tools. How to Make a Timeline on Microsoft Word Step 1 Read More
How to do a System Restore
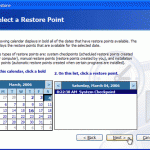
A system restore is a Windows Operating System feature that allows the user to reverse settings and actions that resulted in undesirable outcomes. A system restore is highly beneficial to the user as it quickly and efficiently reverses changes made to the Windows Registry, partition, or operating system, thereby eliminating the need to manually undo changes and retrieve deleted files. A system restore is most beneficial in situations that involve virus or other malicious software removal, software installation or uninstallation, or other major changes to the Windows Operating System. How Read More
Error Number 0x80072ee2
The Microsoft Corporation has designed the Windows Operating System (OS) to query the Microsoft Update web site on recurring intervals in order to check for and install required updates on your computer. If your computer experiences difficulty in connecting to the Windows Update server, then it can result in throwing error number 0x80072ee2 on your computer and will prevent you from updating the computer until the error clears. What Other Error Codes Are Associated With the Windows Update Server? Error 0x80072ee2 is not the only error code that is associated Read More
Monitoring Network Security with ISA Server
Configuring ISA Server Logging ISA Server, by default, creates one log file for the following activities each day: Firewall service activity Web Proxy service activity Packet filtering activity Information is logged in the ISALogs folder in the ISA Server installation folder: FWSEXTDyyyymmdd.log – contains information on packets processed by the ISA Server Firewall service. WEBEXTDyyyymmdd.log – contains information on packets processed by the Web Proxy service. IPPEXTDyyyykmmdd.log – the default is set to log deny packets only. If you want to log information on allowed packets, then you have to Read More
The Windows Routing Table
When routers need to forward packets, they interpret the packets’ addresses then use the information in the routing tables to pass the packet on. Data packets contain both source and destination addresses in their packet headers. This is the information that is used when routing decisions need to be made. The destination address is compared with the local address to determine the following information on how to route the packet: Should the packet be sent up the stack on the local host? Should the packet be sent to a different Read More


Share on: