To remove Windows Genuine Advantage, particularly the validation tool from your Windows-based machine, you need to: Go to your Windows folder, usually at C:Windows. Search for the folder named 'Downloaded Program Files'. Note that Windows Genuine Advantage, which is found embedded on Microsoft Windows OS products, consists of two distinct elements, namely the Validation Tool and the Notification tool. If you are running a Microsoft Windows Server 2003-operated system, locate the ProductIDGatherer.WindowsGatherer file. Right click on it and choose 'Remove'. If you are running a Microsoft Windows XP-based machine, choose Read More
SSL Applications

Using SSL to Encrypt LDAP and Global Catalog Queries While Secure Sockets Layer (SSL) certificates are mainly installed on IIS machines to encrypt traffic between a Web server and client, you can also use SSL certificates to secure the Lightweight Directory Access Protocol (LDAP) protocol. LDAP is used in Active Directory environments by applications that need to query domain controllers for information stored in Active Directory. Because LDAP is also utilized to query for sensitive or Active Directory information such as user names, and network service locations; it is easy Read More
How to Save Desktop Icons in Windows XP
To save desktop icons in Windows XP here are the steps you can take. Step 1 Download the icon set. It is advised that you download the file to somewhere like your desktop so you can easily find the file. Create a new file on your desktop call it "my icons" or whatever you want. Decompress/unzip the file to "my icons." Step 2 Create a new folder on your desktop or find a file that you want to change to one of the new icons. Step 3 Right click on Read More
Managing BizTalk Server
Managing BizTalk Servers and Server Groups A few BizTalk Server administrative tasks that you need to perform to manage BizTalk Server are summarized below. The BizTalk Server Administration console can be used to perform most of the BizTalk Server administrative tasks listed here. You have to be a member of the BizTalk Server Administrators group to perform BizTalk Server administrative tasks. The BizTalk Server administrative tasks are: You can use the BizTalk Server Administration console to add BizTalk server groups and remove BizTalk server groups. The BizTalk Server Administration console Read More
Error 734
Error 734 is a Point-to-Point Protocol error, usually associated with workstation connectivity to a internet provider or wide area network connection. The exact error message is "Error 734: The PPP link control protocol was terminated.". Source of the problem Error 734 is usually produced due to an error in authentication. Generally the username or password you are using to authenticate for the connection to initiate is incorrect. Resolving the problem First and foremost, validate that the username and password you are using for the connection are correct. Most passwords are Read More
Active Directory Management Tools
Active Directory or directory service management is a vital component of any administration process if Active Directory is implemented in the networking environment. The two types of management or administration methods that can be utilized to manage the directory service are: Administrative tools that utilize a graphical user interface (GUI). Command-line tools. Windows Server 2003 includes a number of new command-line tools that manage Active Directory objects as well as the various Active Directory directory parts. The Administrative tools that utilize a GUI can be accessed via the Administrative Tools Read More
Active X Controls

An Active X control can be defined as a small applet or software component that can be reused over and over again. These encapsulated software programs or applets can either be visual or non visual. They are easy to create and can be included in many applications that run on the Windows platform. For instance, if you have created an Access Database and would like to add more functionality to it, there are many different Active X Controls available. One control that is used widely in MS Access is the Read More
What is Funcres.xla?
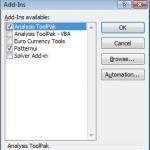
Funcres.xla is a Microsoft Excel add-in that adds additional features to the software. Funcres.xla (Analysis Toolpak) includes 19 various features and a number of statistical functions that allow the user to correlate data and perform calculations that are not otherwise found in Microsoft Excel. However, Funcres.xla is included in most Microsoft Excel copies and the user must simply activate it in order to use it. If Funcres.xla is activated, it will be displayed when the user starts Microsoft Excel, which may confuse some users. Fortunately, Funcres.xla is not harmful and Read More
How to Add a User to Windows
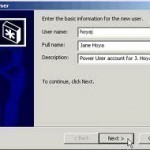
The procedure for adding a new user to Windows depends on the Microsoft Windows version. In addition, there are several ways to add new users to most Windows versions. The instructions presented here show only a few of the possible paths to creating new users on Windows. Add a User to Windows XP Click the Start button Click the Control Panel menu item Double-click the User Accounts icon Click the Create a new account menu item Type a name for the new account in the data entry box Click the Read More
Defining a Baseline Security Template
Security Templates Review A security template is collection of security configuration settings that can be applied to a domain controller, member server or a workstation. The settings within a security template control the security configuration of a computer through both local policies and group policies. A security template can be applied to a local computer, or incorporated into a Group Policy object in Active Directory. You can manage one computer or multiple computers through the security settings contained within a security template. For computers that do not belong to an Read More


Share on: