CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) is the preferred encryption protocol in the 802.11i standard. CCMP Cryptography CCMP is based upon the CCM mode of the AES encryption algorithm. CCMP utilizes 128-bit keys, with a 48-bit initialization vector (IV) for replay detection. The Components of CCMP The Counter Mode (CM) component of CCMP is the algorithm providing data privacy. The Cipher Block Chaining Message Authentication Code (CBC-MAC) component of CCMP provides data integrity and authentication. CCMP and RSN Unlike WRAP (Wireless Robust Authenticated Protocol), CCMP Read More
SIP Gateway
Every office and small business needs a method of running multiple communication programs such as conference calling, video conferencing, media distribution, instant messaging, and account management software. To perform these tasks, servers need the help of a SIP gateway to bridge the gap between data streams and the Internet. SIP gateways are also essential in VoIP networks as they allow for mutiple audio and video connections to take place at one time over the Internet. Moreover, using a SIP gateway is an affordable and efficient method of networking in and Read More
ARP (Address Resolution Protocol)
ARP is the Address Resolution Protocol. The ARP protocol maps addresses between the Data Link Layer and the Network Layer of the OSI Model. The Data Link layer of TCP/IP networks utilizes MAC addresses; the Network Layer of TCP/IP networks utilizes IP addresses. ARP and RARP The ARP protocol is used to map IP addresses to MAC addresses. RARP, the Reverse ARP Protocol, is used to map MAC addresses to IP addresses. The ARP Cache To reduce the number of ARP requests, every system which implements the ARP protocol keeps Read More
How to Find Your MAC Address
MAC is an acronym for Media Access Control. A MAC address is an address that is given to a network adapter (NIC) that helps a computer to identify it. Since many functions of a computer can be determined by the MAC address on the network adapter, it is important to be able to find your MAC address in case it is requested. Finding a MAC address is, for the most part, simple. However it depends on which operating system you are using. Here are a few tips on how to Read More
What is Port Knocking?
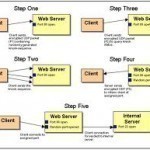
The term port knocking refers to a type of host-to-host communication where the information flows across closed ports. The primary purpose of port knocking is to keep attackers from successfully conducting a port scan since the server will require the correct port knocking protocol or sequence before the port is opened. There are a few types of port knocking methods, including encoding information in a packet-payload or a port sequence. When the port knocking method is used, the data is sent to a closed port and a daemon that is Read More
Email Hosting
Many people find themselves in the position of either registering for an email account for the first time or wanting to switch to an alternative email host. Either way, these people should be careful to not fall victim to several email hosts who try to con prospective email users into paying for their services. There are dozens, if not hundreds, of free email hosting services available on the Internet for anyone to join at any time. The majority of these email hosts also do not have any restrictions on how Read More
PPP (Point-to-Point Protocol)
PPP (Point-to-Point Protocol), is the most widely used method for transporting IP packets over a serial link between the user and the Internet Service Provider (ISP). Although PPP is primarily used over dialup lines, variants such as PPoE (PPP over Ethernet) and PPoA (PPP over ATM) extend PPP to new data-link layer protocols. PPP was designed to enable the transmission of different protocols over one point-to-point link by utilizing encapsulation. Encapsulation is the process of storing packets from the foreign protocol inside PPP frames. In addition to this encapsulation function, Read More
What is EIGRP?
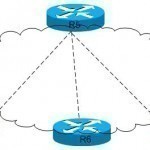
Local and international networks require information to be constantly updated in order to properly route communications. Routing protocols were developed in order to help keep information flowing to the proper locations and to maintain network connectivity on both LAN and WAN. The Enhanced Interior Gateway Routing Protocol (EIGRP) is one of the most popular internal routing protocols used on medium to large businesses and education networks today. EIGRP Basics EIGRP was developed as a hybrid distance vector routing protocol that uses many of the same composite metrics as the Interior Read More
Used Cisco Switches and Routers

Used Cisco Cisco is a worldwide leader in providing the hardware and software solutions of LAN and WAN. The head office of Cisco Company is in San Francisco and the branches and authorized dealers of Cisco currently exist in most of the countries in the world therefore Cisco hardware devices are used in every region around the globe. The software solution provided by Cisco is the Cisco IOS software based on CLI (Command Line Interface) that is used in Cisco manageable devices. Used Cisco Equipment Cisco currently deals in various Read More
SMS Shortcuts
SMS (Short Message Service) is a protocol for sending and receiving brief text messaging over digital cellular networks. Most people send SMS messages from the very small keypads on their mobile phones, and most people who receive SMS messages read them on the tiny screens of their mobile phones. Because of those considerations, and because SMS messages are limited to 160 characters, most people who use SMS learn to type messages using a number of popular SMS shortcuts. SMS Shortcuts These are some of the more common SMS shortcuts. 2D Read More


Share on: