Wireless Access Point (WAP) is essentially hardware equipment that enables wireless devices to connect to wireless networks, via standards such as Wi-Fi, Bluetooth and so on. The WAP device typically connects to a wired network, and acts as a communication interface between the wireless devices and wired devices on the network. The WAP device enables the transmission of data between wireless and wired devices. For example, in an office setup multiple users can print documents from their workstations or laptops that are physically connected to the network, with the help Read More
How fast is ADSL Speed?

ADSL (Asymmetric Digital Subscriber Line) options are available in many locations. The speeds will vary for the service in many ways depending on several factors. The reason why it is called an Asymmetric Digital Subscriber Line is simple, as the speed for downloads will be significantly faster than the upload speed. This is because consumer DSL services are usually used for downloading more so than uploading. The typical speeds will range from 375Kbps download and 128Kbps upload to 3072Kbps download and 448Kbps upload. The speed could go much higher when using wide area network ADSL Read More
How to Get Free VoIP
Free VoIP calls are never completely free of cost. Often, the goal is not to achieve completely free calls to all destinations, but to use the VoIP operator that suits one’s needs best. Keeping that in mind, one will learn that most VoIP companies let users talk for free in their own network, but will charge for making calls outside their proprietary network. Companies offering free VoIP calls usually offer free calls inside their own network and towards other specially selected destinations. Using this tactic, users are drawn to make Read More
Federated Identity Management
Federated Identity Management is a version of Single Sign-On where each device, system, and application queries a centralized database for authentication and authorization information. In addition to the goals of any other identity management system, Federated Identity Management systems are tasked with enabling authentication and authorization data across organizational boundaries. In a true Federated Identity Management system, authentication data can be passed across security domains from within a company to its business partners. This can enable Single Sign-On to extend past organizational boundaries. Federated Identity Management is often abbreviated FIM. Read More
What is VLSM?
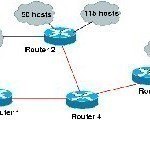
VLSM (Variable Length Subnet Mask) is a technique that network administrators employ in order to use their IP subnet(s) in a more effective manner. By using VLSM, a long mask can be used on a network that has a few hosts and a short net mask on subnets that have a large number of hosts. To use VLSM, however, a routing protocol that supports it has to be used. Cisco routers support the concept with the following protocols: Integrated IS-IS (Integrated Intermediate System to Intermediate System), EIGRP (Enhanced Interior Gateway Read More
Fiber Optic Patch Panel

Fiber optic patch panel, also known as the fiber distribution panel, is used mainly in fiber optic cable management. It helps network technicians in minimizing the clutter of wires when setting up fiber optic cables. It terminates the fiber optic cable while providing access to the cable’s individual fibers for cross connection. They are also called the termination units and they are used to secure the splice units, and connectors. The fiber optic patch panels can accommodate connector panels, connectors, patch cords, associated trunk cables, and usually come with cable Read More
Patch Panel
A patch panel is a panel that houses multiple cable connections. It is also known as a jackfield or patch bay. The back of the panel has wiring or other connective cabling that runs to disparate equipment. The front of the patch panel allows easy access to connect the different equipment with the use of short patch cables. Before automatic telephone switching became widespread, huge arrays of patch panels were used, in which early telephone operators would connect callers to their intended parties manually by plugging in a cable on Read More
Mobile Firewall
A mobile firewall is a hardware and software system that is designed to protect wireless communication networks from unauthorized access and use. The whole system works when it is used connectively and if the mobile node, the firewall hardware and software system, and the network itself are present and operational. The mobile communications firewall system is made and designed to safeguard the network's system together with all of the mobile clients or subscribers that make use of the services offered by the network. The mobile firewall system acts as an Read More
Broadcast Domain
A broadcast domain is a logical part of a network (a network segment) in which any network equipment can transmit data directly to other equipment or device without going through a routing device (assuming the devices share the same subnet and use the same gateway; also, they must be in the same VLAN). A more specific broadcast domain definition is the area of the computer network that consists of every single computer or network equipment that can be reached directly by sending a simple frame to the data link layer’s Read More
What Are the Effects of Computer Hacking?
Hacking as a Destructive Tool The common stance on hacking with the average person is that it is morally wrong. There have been several instances where hacking has proven to have caused problems. Hacking can create a variety of damages to people, groups and systems of broad spectrum. Negative Hacking Interactions: Identity Theft – Some hackers can gain access to sensitive information which could be used to fuel identity theft. This identity theft can cause damages to credit ratings from consumer agencies, run-ins with the law because the person who stole the identity Read More


Share on: