Westell is a provider of DSL routers and other DSL-based devices that telephone companies and DSL subscribers use for wireless Internet in homes or offices, instead of using cable or satellite Internet. Westell products generally have the same features as other routers, such as dual antennas, four Ethernet ports, and WPA encryption, but connect to the Internet through a telephone wire. The Westell wireless router has been used since mid-2004 as BellSouth’s default Internet router. The router features 802.11 wireless support, four Ethernet ports, and a built-in firewall. Similar to Read More
How to Add a Printer to a Wireless Network
If you want to add a printer to a wireless network, you need to: 1) Ensure that the printer has at least one USB port. 2) Purchase a wireless adapter and connect it to the printer’s USB port. Since wireless adapters work on Plug-and-Play technology, the printer should automatically detect it and begin installing all of the drivers necessary for the wireless adapter to function properly. 3) In order to specify which wireless network the printer should connect to, connect the printer to the router via an Ethernet cable and Read More
What is a Rollover Cable?

A rollover cable is a network cable that connects a computer terminal to a network router’s console port. It is also referred to as a Cisco console cable and is normally flat and light blue so as to distinguish it from other network cable types. The pin-outs on one end of the cable are reversed from the opposite end, which is how the cable derived its name. Rollover cables are also known as Yost cables or Yost Serial Device Wiring Standard connectors. How to Identify a Rollover Cable A rollover Read More
Understanding the IPX-SPX Protocol
IPX/SPX is a protocol suite that is implemented on many corporate internetworks. IPX/SPX was developed to operate in Novell Netware in LAN environment. But today, the IPX/SPX is also used in Microsoft NT, Microsoft XP and Lotus Notes environment along with Vista. IPX/SPX on Cisco IOS The Cisco IOS also provides a wide range of configuration tools and options for IPX/SPX protocol suite. The Cisco IPX/SPX router configuration tools are very much similar with Cisco IP router configuration. Some of them are listed: The Cisco IOS provides static route support Read More
Ethernet at the Physical Layer
Ethernet is the most popular Local Area Network architecture that was jointly developed by Digital Equipment Corporation, Intel Corporation and Xerox Corporation. It consists of certain specifications and standards as well as hardware devices and components. Ethernet provides services corresponding to physical layer and data link layer of the OSI reference model. Each Ethernet physical layer protocol has a three part name that summarizes its characteristics. The components specified in the naming convention correspond to LAN speed, signaling method, and physical media type. The following table summarizes the differences between Read More
802.1X
802.1X is an IEEE standard for EAP encapsulation over wired or wireless Ethernet. 802.1X is also known as EAPoL (EAP over LAN). This only makes sense when you recall that EAP was originally designed for use over PPP. 802.1X Roles 802.1X defines three roles: Name Description Supplicant User or client requesting authentication Authentication Server The server providing authentication Authenticator The device which the Supplicant requests access to, and which requests access from the Authentication Server. 802.1X and RSN 802.1X is particularly well suited for wireless LAN applications because it requires Read More
Mi-Fi
While Novatel Wireless has copyrighted to name MiFi, it has gone on to mean so much more. Mi-Fi literally stands for my-wifi. In other words, it is a personal credit card shaped piece of hardware that acts as a personal WiFi hot spot for you and a few other computers that you allow onto the network. Once connected to the Mi-Fi, a user can have access to high speed Internet that they would typically find from a traditional WiFi setting. How Does Mi-Fi Work? Mi-Fi works by having this compact Read More
The OSI Model – What It Is; Why It Matters; Why It Doesn’t Matter.
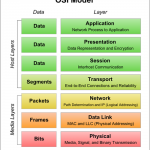
The OSI Model was created based on recommendations from the International Organization for Standardization (ISO) in 1980, which started expanding on the DoD model in the late 1970s. The current standard was published in 1996. The official title for the model is the ISO OSI (Open Systems Interconnection) Reference Model since it describes or relates to connecting systems that are open for communication with other systems. In the model, the functions of the communication system are standardized by categorizing them into abstract layers. The functions which are similar are grouped Read More
Net Neutrality
The term "net neutrality" or "network neutrality" arose from a set of concerns regarding the role of telecommunication and cable companies or Internet service providers (ISPs) in the delivery of data over the internet. It generally refers to the idea of equal access to content delivered over the Internet and non-discrimination of Internet content providers, types of content (text, video or audio) or methods of their transfer (HTTP, FTP, bittorrent). Advocates of net neutrality typically call for a legal mandate that would ensure net neutrality by restricting ISP's from practices Read More
Token Ring
Token Ring is a local area networking system originally conceived in the late 1960s by IBM and patented in 1981, with IBM promoting its use throughout most of the 1980s. Although initially very successful, it was eventually displaced by Ethernet as the favored technology and architecture for local area networks (LAN); although IBM undertook a valiant effort to compete, this was not successful and IBM itself eventually stopped using token ring as its LAN standard. How Token Ring Works The token ring network is simple in design and conceptual operation. Read More


Share on: