MIC (Message Integrity Check) is part of a draft standard from IEEE 802.11i working group. The MIC (Message Integrity Check) is an additional 8 byte field which is placed between the data portion of an 802.11 (Wi-Fi) frame and the 4 byte ICV (Integrity Check Value). The MIC has a function very similar to the older ICV. However, the ICV only protects the packet payload. The MIC protects both the payload and the header. The algorithm which implements the MIC is known as Michael. Michael also implements a frame counter, Read More
How to Access Wireless Router Settings

What is a Wireless Router? A wireless router is a device that wirelessly connects multiple computers and devices to the Internet. Wireless routers’ design and capabilities vary and they drastically range in price, but are used for the same function. Wireless routers are usually very easy to setup and many provide the user with built-in security methods such as data encryption or a firewall. As a result, wireless routers allow users to easily setup a wireless network that all of the computers and devices in a home, office, or other Read More
GPRS (General Packet Radio Service)
GPRS (General Packet Radio Service) is a specification for data transfer on TDMA and GSM networks. GPRS utilizes up to eight 9.05Kb or 13.4Kb TDMA timeslots, for a total bandwidth of 72.4Kb or 107.2Kb. GPRS supports both TCP/IP and X.25 communications. Fixed/Mobile Mobile Circuit/Packet Packet Max Bandwidth 107.2Kb Range Coverage area of host network Frequency Frequency of host network Host Network TDMA, GSM Definer ETSI The Future of GPRS EDGE (Enhanced Data-Rates for GSM Evolution) enabled GSM networks are able to implement EGPRS (Enhanced General Packet Radio Service), an enhanced Read More
Access Point
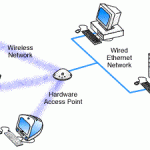
As technology has advanced, devices have become more complex and integrated. Access points make a good example of such devices. These can be described as hardware that includes a modem, router, and other optional functions that are all compiled into one device. Access points are becoming more popular than modems or routers and they are common in medium and large businesses. This article will explain what an access point is, how to create or setup an access point, and describe some of the most popular access points available on the Read More
Rogue Wireless Access Point
A Rogue Access Point is a Wi-Fi Access Point which is setup by an attacker for the purpose of sniffing wireless network traffic. 802.11 (Wi-Fi) utilizes SSIDs (Service Set IDentifiers) to authenticate NICs to wireless access points. There is no similar protocol for authenticating wireless access points. It is possible to place a rogue wireless access point into an 802.11 network. This rogue wireless access point can then be used to hijack the connections of legitimate network users. When a legitimate network user turns on his computer, the rogue wireless Read More
EDGE (Enhanced Data for Global Evolution)
Fixed/Mobile Mobile Circuit/Packet Packet/Circuit Max Bandwidth 384Kb Range Coverage area of host network Frequency Frequency of host network Host Network GSM Definer ETSI (European Telecommunications Standards Institute) URL http://www.etsi.org/ EDGE (Enhanced Data rate for GSM Evolution) is a specification for data transfer on GSM networks. EDGE features both a packet capability, EGPRS (Enhanced General Packet Radio Service), and a circuit switched capability, ESCD (Enhanced Circuit Switched Data). EDGE packs up to 69.2Kbps into eight timeslots, for a total theoretical bandwidth of 473.6Kb. GERAN (GSM/EDGE Radio Access Network) is the name Read More
Where can I Find a Wi-Fi Hotspot?

With the growing ubiquity of wi-fi access, finding a hotspot is becoming easier by the day. However, users who are travelling or have changed equipment may encounter difficulty in finding a hotspot. There are several directories and apps that users can look to for solutions. Users should first check their device settings, to ensure that the device is set to search for all local Wi-Fi signals available. Many merchants, restaurants, and hotels now provide complimentary and/or free Wi-Fi access to their patrons and adjoining public spaces, as well as most Read More
How to Reset a Belkin Router
Belkin brand routers are capable of a hardware reset if there are any problems with the current settings or if access to the router has been disabled inadvertently. The hardware reset function can be performed on Belkin routers by following these steps: Note: Resetting a Belkin router will remove all of the current settings and return it to the factory default settings. Do not perform the reset unless you have the information needed to setup the router to the correct settings needed once the reset has been completed. Manual Hardware Read More
WEP Key Passphrase
A wireless network key is an encryption key for that prevents unauthorized users from accessing a specific wireless network. The user creates wireless network keys, which either a wireless router or a computer that is connected to that wireless router can manage. Wireless network keys can be any length greater than eight characters and can be used with both WEP and WPA encryption methods. A wireless network key serves as a password for a specific wireless network and prevents unauthorized users from accessing it. Wireless network keys can be used Read More
Linksys Default Password
Linksys is a leading producer of networking devices, including wireless routers, modems, and network storage devices. Millions of people worldwide use Linksys products for both residential and commercial purposes. Linksys Default Password Linksys routers have a built-in control panel that allows you to change configuration settings, set the router to work with other devices, and set up network security. You can access this control panel by entering 192.168.1.1 into the address bar of any web browser. You will then be prompted for your username and password (this information is printed Read More


Share on: