This method works on sorted lists by progressively making better guesses to find the location of a search key. Illustration Consider the following array: 3 10 15 20 35 40 60 Suppose we want to search the element "15" We take beg = 0, end = 6 and compute the location of the middle element as We then compare the search key with mid i.e. a[mid]=a[3] is not equal to 15. Since beg<end, we start the next iteration. As a[mid]=20>15, therefore, we take end = mid-1 = 3-1 = 2 Read More
JRE (Java Runtime Environment)

The JRE is the Java Runtime Environment. The JRE consists of the Java Virtual Machine, the Java libraries, and all other components necessary to run Java applications and applets. Sun distributes the JRE seperately, or as part of J2EE, J2SE, and J2ME.
Type Conversion – Class to Basic Type
The constructor handles the task of converting basic types to class types very well. But you cannot use constructors for converting class types to basic data types. Instead, you can define an overloaded casting operator that can be used to convert a class data type into a basic data type. The general form of an overloaded casting operator function is shown below. This function is also known as a conversion function. Syntax: .cf { font-family: Lucida Console; font-size: 9pt; color: black; background: white; } .cl { margin: 0px; } .cb1 Read More
Circular Queue
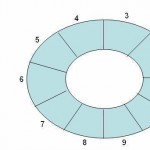
The difficulty of managing front and rear in an array-based non-circular queue can be overcome if we treat the queue position with index 0 as if it comes after the last position (in our case, index 9), i.e., we treat the queue as circular. Note that we use the same array declaration of the queue. Empty queue: Non-empty queues: Implementation of operations on a circular queue: Testing a circular queue for overflow There are two conditions: (front=0) and (rear=capacity-1) front=rear+1 If any of these two conditions is satisfied, it means Read More
Decompiler
A decompiler is a program which takes executable code and produces source code from it. A compiler creates executable code from source code; A decompiler attempts to reverse this process. A decompiler is a specialized version of a disassembler. While a disassembler converts executable code to assembly language, a decompiler attempts to go further and convert the executable code to source code in a higher level language, such as C or C++. Decompilers Boomerang The goal is the Boomerang project is an attempt to develop a real decompiler for machine Read More
Searching
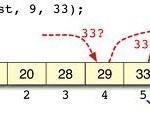
Searching is the process of finding the location of a given element in a set of elements. The search is said to be successful if the given element is found i.e., the element does exist in the collection (such as an array); otherwise it is unsuccessful. Two simple approaches to searching are: Linear search: This method traverses a list sequentially to locate the search key. Binary search: This method works on sorted lists by progressively making better guesses to find the location of a search key.
CGI Scripting

CGI stands for Common Gateway Interface, which is the standard for creating dynamic files or web pages. It can be seen in use on thousands of web pages – website guest books which allow a visitor to enter a message which is displayed the next time anyone accesses the guest page, or search engine pages where one types in a query and the search engine responds by displaying the results pages. CGI scripting actually refers to writing a program that will control how a website’s content can be displayed to Read More
Inserting in a Doubly Linked List
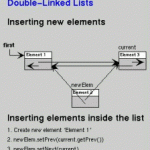
Inserting an Element To insert an element in the list, the first task is to allocate memory for a new node, assign the element to be inserted to the info field of the node, and then the new node is placed at the appropriate position by adjusting appropriate pointers. Insertion in the list can take place at the following positions: At the beginning of the list At the end of the list After a given element Before a given element Insertion at the Beginning of the List First, test whether Read More
File Manipulation
A file is basically a set of records stored on your computer's secondary memory. There may be situations requiring a program to open more than one file. The strategy for opening multiple files depends upon how they will be used. If the situation requires simultaneous processing of two files, then you need to create a separate stream for each file. However, if the situation demands sequential processing of files (i.e., processing them one by one), then one can open a single stream and associate it with each file in turn. Read More
Format String Vulnerability
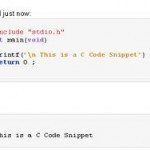
To understand what a format string vulnerability is, you first need to know what a format string is. A format string is a way of telling the C compiler how it should format numbers when it prints them. Format Strings in C In the C programming language there are a number of functions which accept a format string as an argument. These functions include fprintf, printf, sprintf, snprintf, vfprintf, vprintf, vsprintf, vsnprintf, setproctitle, syslog, and others. The most common of these is printf. The usage of printf is: printf format Read More


Share on: