An integer overflow, or integer wrapping, is a potential problem in a program based upon the fact that the value that can be held in a numeric datatype is limited by the data type’s size in bytes. ANSI C uses the following minimum sizes: data type size (bytes) char 1 short 2 int 2 long 4 In practice, many compilers use a 4-byte int. It also should be noted that the actual ranges for the data types depend on whether or not they are signed. for instance, a signed 2-byte Read More
Race Condition
A race condition occurs when multiple processes access and manipulate the same data concurrently, and the outcome of the execution depends on the particular order in which the access takes place. A race condition is of interest to a hacker when the race condition can be utilized to gain privileged system access. Consider the following code snippet which illustrates a race condition: if(access("/tmp/datafile",R_OK)==0){ fd=open("/tmp/datafile process(fd); close(fd); This code creates the temporary file /tmp/datafile and then opens it. The potential race condition occurs between the call to access() and the call Read More
Random Number Vulnerability
Computers are deterministic and are therefore predictable. Computers cannot, in and of themselves, generate truly random numbers. In the absence of outside input, computers can only create pseudo-random numbers. In the words of John Von Neumann, “Anyone attempting to produce random numbers by purely arithmetic means is, of course, in a state of sin.” A random number vulnerability occurs when a program uses a method of generating random numbers which is either: Not random Predictable To generate good random numbers, the computer must have two things: A good random number Read More
Format String Vulnerability
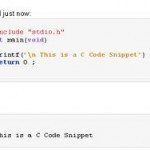
To understand what a format string vulnerability is, you first need to know what a format string is. A format string is a way of telling the C compiler how it should format numbers when it prints them. Format Strings in C In the C programming language there are a number of functions which accept a format string as an argument. These functions include fprintf, printf, sprintf, snprintf, vfprintf, vprintf, vsprintf, vsnprintf, setproctitle, syslog, and others. The most common of these is printf. The usage of printf is: printf format Read More
SQL Injection Attack / Vulnerability

A SQL injection vulnerability can occur when a poorly-written program uses user-provided data in a database query without first validating the input. This is most-often found within web pages with dynamic content. There are some excellent tutorials and descriptive articles on this subject, as well as many vulnerability postings for different applications from full-disclosure websites. A simple example of SQL injection is a basic HTML form login in which you provide a username and password: <form method=”post” action=”process_login.php”> <input type=”text” name=”username”> <input type=”password” name=”password”> </form> Given this snippet of HTML, Read More
How to Find Security Vulnerabilities in Source Code
The original, and still the best, method for finding security vulnerabilities in source code is to read and understand the source code. Source code security vulnerabilities will vary between languages and platforms. Items to look for in C code include: Potential vulnerability Function calls to examine for vulnerabilities Buffer overflows gets(), scanf(), sprintf(), strcat(), strcpy() Format string vulnerabilities printf(), fprintf(), vprintf(), snprintf(), vsnprintf(), syslog() Race conditions access(), chown(), chgrp(), chmod(), mktemp(), tempnam(), tmpfile(), tmpnam() Random number acquisition vulnerabilities rand(), random() Shell metacharacter vulnerabilities exec(), popen(), system() Automated Source Code Security Read More


Share on: