Erasing the history on a computer is very important for personal safety. There are two main types of history that computer users may want to remove from a system: the Windows and Web Browser history. There are several different locations where computer usage information is stored in Windows. Modern Windows operating systems are preconfigured to track everything from recently opened documents, search items, save history, and run history. The process of removing this personal information is relatively simple if these steps are followed: Recently Opened Documents in Start Menu – Read More
Chosen Plaintext Attack

A chosen plaintext attack is an attack where the cryptanalyst is able to define his own plaintext, feed it into the cipher, and analyze the resulting ciphertext. Mounting a chosen plaintext attack requires the cryptanalyst to be able to send data of his choice into the device which is doing the encryption, and it requires the cryptanalyst to be able to view the output from the device. Because of these requirements, a chosen plaintext attack is in some cases impossible to attempt. A good example is the attacks on the Read More
Key Servers
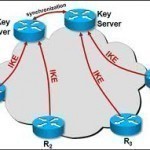
A key server is a networked computer used to provide cryptographic keys to other computer programs or end-users. Key servers can be used on both internetal networks as well as across the Internet. Today, the primary keys that are served by key servers are keys in Open PGP, x.509, or PKCS key certificate formats and help serve to verify information by a company or individual in the public key infrastructure architecture. How Key Servers Were Created Key servers were initially developed as part of the overall creation of public Read More
Brute Force Attack

A brute force attack consists of trying every possible code, combination, or password until the right one is found. Determining the Difficulty of a Brute Force Attack The difficulty of a brute force attack depends on several factors, such as: How long can the key be? How many possible values can each key component have? How long will it take to attempt each key? Is there a mechanism that will lock the attacker out after a number of failed attempts? As an example, imagine a system that only allows 4 Read More
How Do I Get Rid of About Blank?
About: Blank is a homepage hijacker that severely slows down your computer and shows popup advertisements randomly while using one’s Internet browser. While it does not do actual damage to the computer, it does limit what can be done on the computer because, at times, the About: Blank could be using as high as 80% of the CPU’s power. Therefore, removing it is an important task. Removing About: Blank There are two main ways to remove About: Blank. The first is to do it the manual way. To do this, Read More
Technologies That Can Help Protect Your Privacy

In a previous article on privacy we’ve established what it is, how does digitally networking our world affect it, and in a nutshell, why should we care. We established that the best way to ensure your privacy is through technological means, and in this article I offer an overview of what such technologies are. What is common to all of them is that they let you control access to information about yourself, whether it is your location, sites you visit, conversations you have online, things you post about yourself, and Read More
Forensic Science
The word forensic comes from the Latin word forensis, which means “before the forum,” and refers to something “of, pertaining to, or used in a court of law.” In this day and age, it almost always refers to a method of obtaining criminal evidence in order to use it in a court of law. Forensic science is typically just referred to as “forensics” and is the practical application of numerous sciences to solve legal system related questions in either a civil or criminal action. Using the term “forensics” in place Read More
Bump Keys

A bump key is a specially crafted key that is commonly used to open any lock the key blank will fit in. Criminals use bump keys to quickly open key based locks that utilize a cylendar and tumbler design without causing damage or leaving any other indication that the lock was tampered with. Criminal use of bump keys has been going on for decades so it is not a new technique of opening locks. Lock owners have been in the dark about how easy it is to defeat their home Read More
Rubber Hose Cryptology

Rubber Hose Cryptography refers to a file system in which multiple archives are encrypted and hidden on the same disk in a way that makes each archive appear to be the size of the entire disk. Rubber Hose Cryptography is often used to hide illegal or confidential information in an attempt to prevent theft or detection of the hidden data. Because each archive must be decrypted separately and rest atop one another in layers, no archive in a Rubber Hose file system knows anything about the other archives. This prevents Read More
S-MIME

S/MIME, (Secure / Multipurpose Internet Mail Extensions) is a protocol which provides digital signatures and encryption of Internet MIME messages. S/MIME, which utilizes the RSA (Rivest-Shamir-Adleman) public-key encryption technology, is a secure method for sending email. S/MIME defines how a digital certificate and encryption information can be provided as part of the message body. The S/MIME protocol follows the syntax as laid down in the PCKS #7 (Public-Key Cryptography Standard format number 7). S/MIME has been proposed by RSA as a standard to the Internet Engineering Task Force (IETF). PGP/MIME Read More


Share on: