The Zeus Virus is the popular term for the Zeus banking Trojan virus recently used to steal banking account details and passwords in the U.K. Resulting in a loss of more than $850,000 for those infected. The Zeus virus has been around for a number of years as part of the larger Zeus Crimeware Toolkit, and is available for purchase through rogue hacking forums across the Internet. Criminals who purchase the Zeus Crimeware kit are given a web interface panel to control the deployment and use of the Trojan as Read More
How to Recover a Zip Password

PKZip utilizes a proprietary stream cipher that is vulnerable to a known plaintext attack, as Eli Biham and Paul C. Kocher describes in A Known Plaintext Attack on the PKZIP Stream Cipher. In ZIP Attacks with Reduced Known-Plaintext, Michael Stay describes an improved known plaintext attack that works against files that non-PKZip zip programs such as InfoZip, WinZip, and NetZip create. The Stay attack requires the Zip archive to contain a minimum of five files. In addition to these two attacks, it is also possible to recover a Zip password Read More
How to Protect Myself from Viruses

The most common viruses are boot sector infectors. You can help protect yourself against those by write protecting all disks which you do not need write access to. Definitely keep a set of write protected floppy system disks. If you get a virus, it will make things much simpler. And, they are good for coasters. Only kidding. Scan all incoming files with a recent copy of a good virus scanner. Among the best are F-Prot, Dr. Solomon’s Anti-virus Toolkit, and Thunderbyte Anti-Virus. AVP is also a good program. Using more Read More
How Does PDF Password Recovery work?
PDF documents can utilize two passwords: Password to open Password to restrict printing and editing Password to Open The Password to open requires a user to enter a password to view the document. When the user sets a Password to open, all of the strings and streams in the PDF document are encrypted with the RC4 stream cipher. The Password to open is also know as the User password. Password to Restrict Printing and Editing The Password to restrict printing and editing can be configured to require a user Read More
How to Clear Your Cache
Most web browsers store web pages and images that we browse on the Internet. The web browsers cache (meaning, temporarily store) these files for a short time in your computer. If we revisit a pre-visited web page while these files are still in the cache, the web browser retrieves the files from the disk cache instead of getting these files from the web site. This can significantly speed up web browsing, but it may not render the updated web page in some cases. The web browser cache can cause privacy Read More
Browser Encryption

Browser encryption is a form of cryptography that uses simple encryption algorithms to protect a user’s information while he/she accesses the Internet. While a user may implement virtually any kind of browser related encryption protocol in his/her browser via security plug-ins and add-ons, most forms of browser encryption can already be found in the user’s browser. If a user wishes to have a more secure browser than the one he/she is currently using, he/she could simply download another browser or run a third party application to secure his/her personal information. Read More
PKI Certificate
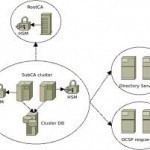
A PKI certificate, which stands for Public Key Infrastructure certificate, allows someone to combine their digital signature with a public key and something that identifies them, an example being their real life name. This certificate is used to allow computer users to show that they do own the public keys they claim to. In other words, it is a security mechanism for public keys. As mentioned before, a digital signature is required for the PKI certificate. This signature can either be made by an authority figure who assigns the certificates, Read More
How to Bypass Websense

Many businesses and government institutions use a content filtering program such as Websense to keep employees from visiting certain websites while at work. These programs can either prohibit the use of certain websites or monitor all of the sites that employees visit while in the office. Websense blocks several website categories: adult material, entertainment, drugs, games, sports, Internet communication, peer-to-peer file sharing, gambling, instant messaging, health, illegal, shopping, job search, Internet telephony, religion, special events, travel, violence, weapons, advertisements, freeware and software download, pay-to-surf, malicious websites, and many more. The Read More
Free Spyware Removal Software

Our current list of recommended free spyware removal software is: Spybot Search & Destroy AdAware Spy Sweeper Download, install, and execute this free spyware removal software and your system will be running better in about 15 minutes. Spybot Search & Destroy is free. AdAware has one version which is free for non-commercial use and two pay versions. Spy Sweeper is a subscription service, but you can get one database update as a demo. Many people run multiple free spyware removal software packages on their computers to increase their odds of Read More
The History of Computer Viruses

The first computer virus to openly make it to the public was a program called “Elk Cloner”. It was created by Rich Skrenta, a computer programmer who was in high school when this virs was created in 1982. Elk Cloner attached itself to the Apple DOS 3.3 operating system and was later spreaded by a floppy disk. When the virus was created, it was intentionally made as a joke by the high school student, who inputted the virus into a game in which the virus was set off after the Read More


Share on: