As many people are fed up with their cell phone providers, a new trend has opened up for tracphones. A tracphone, or TracFone, is a prepaid phone that gives you the accessibility of a contract plan without the commitment. Tracphones have become much more popular in the past few months as more people are finally ending their two year contracts with their cell phone providers and switching to prepaid plans. To properly define how tracphones can help you, this article will analyze the various features that tracphones have to offer. Read More
PSTN (Public Switched Telephone Network)
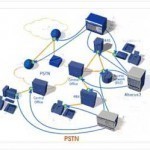
The PSTN is the Public Switched Telephone Network. The PSTN is the entire telephone system, except for private telephone systems which are managed by their own PBX.
MTSO: Mobile Telephone Switching Office
The Mobile Telephone Switching Office, or MTSO, is a system that automatically keeps track of a cell phone user’s relative signal by monitoring readings from cell phone towers near the user. MTSO systems also automatically switch a cell phone’s service from one cell phone tower to another depending on which tower will provide the user with the best possible reception. Additionally, the MTSO is responsible for connecting all individual cell phone users in an area to a “central office”, which then connects those users to long-distance areas. How MTSO Read More
IMEI (International Mobile Equipment Identity)
Each GSM and UMTS mobile phone has a unique IMEI (International Mobile Equipment Identity) number. An IMEI number facilitates an important function – it easily identifies a mobile phone being used on a GSM (Global System for Mobile Communications) network. The IMEI is a useful tool to stop a stolen phone from accessing a network being used. Mobile phone owners whose phones have been stolen can contact their mobile network provider and ask them to ban or shut off a phone using its IMEI number. With an IMEI number, the Read More
ACD (Automatic Call Distributor)
ACD, or Automated Call Distribution, is a telephony system that automatically forwards incoming calls to a specific group of telephones. ACD is most commonly used in corporate environments in which a company has a billing department, customer service department, retail department, and a managerial department or multiple branches. In these cases, an ACD may collect information from the caller through automated questions or detect the caller’s area code in order to forward the call to the correct department or branch. How ACD Works When a caller first calls a Read More
LEC (Local Exchange Carrier)

An LEC, or Local Exchange Carrier, is a telephone company that is responsible for managing calls within a specific territory, such as a city or county. The vast majority of the United States is managed by LECs, which differ from IXCs, or Interexchange Carriers. While LECs manage local calls between two parties, IXCs are responsible for managing long-distance calls between multiple LEC territories, known as LATAs, or Local Access and Transport Areas. How LEC Works An LEC manages all calls, equipment, and customer queries within its respective LATA, although Read More
How to Make Ringtones

Smart phone and related technologies have significantly increased over the past few years world-wide. From the poorest to the richest countries, the cost and penetration of mobile technology has resulted in cell phone usage dramatically increasing across all social-economic boundaries. One of the commonalities across the various models of cell phones is the ability to use tailored ringtones for a mobile phone. In order to obtain new ringtones for a phone, however, consumers find that many cell phone service provides will charge a fee for ringtone downloads or require one Read More
IVR Software
IVR software enables companies to build custom Interactive Voice Response (IVR) systems, which can be used to provide automated self-service to inbound callers. IVR enables callers to interact more intuitively with automated phone systems, while at the same time providing significant cost reductions over human operators. IVR Call Flows A sample IVR call flow might sound like this: IVR: Hello, and thank you for calling the NRA. Would you like to Join the NRA, Contribute to the NRA, or Locate your Election Volunteer Coordinator? Caller: Election Volunteer Coordinator IVR: Thank Read More
CLLI Codes
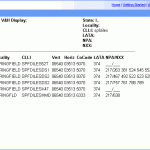
CLLI codes, or Common Language Location Identifier, pronounced “silly codes”, are codes used by telecommunication companies to identify specific industry equipment. CLLI codes are 11 characters long, may be comprised of a combination of letters and numbers, and are used by all telecommunication companies in North America. While CLLI codes were first created and used by Bell, they were soon adopted by all telecommunication companies due to their need to be interconnected with Bell. Today, CLLI codes are maintained, issued, and trademarked by Telcordia, previously known as Bell Communications Research, Read More
Call Back Security
Call back security, also known as dial back security, is a security mechanism used to authenticate users over dialup lines. The way call back security works is the dialup user calls into the system and enters his username and password. The system then hangs up on the user and calls the user back at a preconfigured number. Call back security can sometimes be defeated using this technique: Configure your modem to auto-answer. On Hayes-compatible modems, the command to do this is ATS0=1. Dial the remote system. When the remote system Read More


Share on: