Unix has many dedicated fans who have written quite a few excellent Unix tutorials for beginning users. Here are a few of the better Unix tutorials: Unix Tutorial for Beginners Unix: The Bare Minimum Introduction to Unix commands Unix Tutorial UNIXhelp for Users Unix Tutorial and Command Reference Unix Tutorial
How to Use the Unix Find Command
The Unix find command, as the name implies, is a command that you can enter into the command line, or terminal, of a Unix operating system, allowing you to process any given set of files or directories. It is a highly useful command that you can take advantage of on Unix based operating system, making it a valuable tool in a lot of situations. Using the find command on Unix allows for a multitude of possibilities. The Unix find command can take advantage of many parameters to help you make Read More
How Unix System Logs Files work
Unix system log files include: utmp wtmp lastlog Unix records information about current users in the file utmp, logins and logouts in the file wtmp, and last logins in the file lastlog. The time stamps of date changes, shutdowns and reboots are also logged in the wtmp file. The usual locations of these files are: Log file Usual location utmp /etc/utmp wtmp /usr/adm/wtmp lastlog /usr/adm/lastlog Editing Unix System Log Files These log files are not text files that can be edited by hand with vi; these are binary files which Read More
Unix Signals
A signal is a message that can be sent to a running process. Programs, users, or administrators can initiate signals. For example, the proper method of telling the Internet Daemon (inetd) to re-read its configuration file is to send it a SIGHUP signal. For example, if the current process ID (PID) of inetd is 4140, type: kill -SIGHUP 4140 Another common use of signals is to stop a running process. To stop the inetd process completely, use this command: kill 4140 By default, the kill command sends the SIGTERM signal. Read More
NIS (yp)
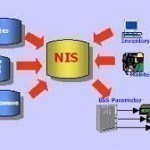
NIS (Network Information System) in the current name for what was once known as yp (Yellow Pages). The purpose of NIS is to allow many machines on a network to share configuration information, including password data. NIS is not designed to promote system security. If your system uses NIS you will have a very short /etc/passwd file that includes a line that looks like this: +::0:0:::i To view the real password file use this command `ypcat passwd` NIS and NIS+ are being replaced by LDAP (Lightweight Directory Access Protocol).
Where to Get a Unix Emulator
It is very useful to have a Unix emulator installed on your machine to serve as a tool for learning how to use Unix and getting used to its environment. Once you are familiar, you can go ahead and install a full version of Unix. The best Unix emulator for your needs is Cygwin (pronounced ‘sig win’), which is a nearly complete Unix-like environment that can be run on Windows. Cygwin is made to work with all the officially released 32-bit x86 versions of Windows, except Windows CE. The Cygwin Read More
Unix File Permissions
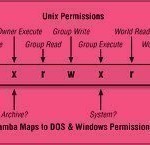
Unix file permissions are based upon an octal code. Unix file permissions are stored in a ten character array. The first character of the file permissions stores the file type. The standard file types are: Character Meaning – Plain file d Directory c Character device b Block device l Symbolic link s Socket = or p FIFO The next nine characters are divided into three groups of three characters, each of which represents a different role on the system: User permissions govern what a user can do with his own Read More
How to Audit Unix Passwords

To audit Unix passwords, you must compare each encrypted password in the Unix password file with a set of potential encrypted passwords. These potential encrypted passwords are created by encrypting every password in a list of plaintext passwords. This is an example of a dictionary attack. The Unix passwd File Location The traditional location for the Unix password file was /etc/passwd. Unix password file format An entry in the Unix password file consists of seven colon delimited fields: Username Encrypted Unix password (And optional password aging data) User number Group Read More


Share on: