What is a Yagi HDTV Antenna? A Yagi antenna is one that uses directional, single-plane dipoles to pick up over-the-air radio transmissions for TV and radio. Yagi antennas have been extremely popular since the 1950s but have declined in use as more users have switched to cable and satellite plans. Yagi antennas are still widely used, however, in areas that are impractical or inconvenient for cable and satellite connections. Yagi HDTV antennas simply refer to Yagi antennas that are capable of receiving an HD signal. How Does a Yagi HDTV Read More
Electromagnets
Electromagnets are magnets whose magnetic properties come from or are generated through electricity. A magnet is a material (this is usually metal), which has at least one pair of negative and positive poles. These opposite poles' attraction produces a magnetic field. This gives the magnet the ability to 'attract' metals such as iron or steel. Electromagnets are soft magnets whose magnetic field can be strengthened or weakened depending on the electric current applied; the stronger the current, the stronger the magnetic field produced. Electromagnets are distinct from hard magnets (manufactured Read More
How to Use a Web Camera
A web camera is one that allows you to stream yourself onto the Internet so someone that you're chatting with can see you. As they become cheaper to make, more monitors and laptop screens are coming with them built in; however, you can buy an inexpensive web camera that you can put on top of your monitor for around $50. Using one isn't difficult once you've got it set up. For the most part, set up of the web camera requires installation of software and plugging it in. Most web Read More
Identity Management
Identity management is a discipline which encompasses all of the tasks required to create, manage, and delete user identities in a computing environment. Identity Management is often abbreviated IdM. Identity Management Tasks During Account Provisioning Identity management begins with the creation of the user account and the assignment of appropriate attributes to the account. The user account is then provisioned into all of the systems to which that user is to be given access. Identity Management Tasks During the Account Lifetime Identity management tasks during the lifetime of the user Read More
Cloud Computing SLA’s

Service Level Agreements (SLAs) have been an effective tool for managing IT service vendors for two decades now. Many companies also use internal SLAs for managing relationships between departments. Service Level Agreements define the duties of both organizations. External SLAs also define penalties which occur when the service provider organization fails to provide the defined level of service. Cloud computing represents a new playing field for SLAs. Cloud computing integrates far more deeply into an organization than traditional IT outsourcing, but at the same time it does not provide the Read More
GPG (GNU Privacy Guard)

GPG, or GnuPG, is GNU Privacy Guard. GnuPG is a complete and free replacement for PGP. Gpg4win is an installer package for GPG that adds a graphical shell and plugins for Microsoft Outlook and Windows Explorer. Because GPG does not use the patented IDEA algorithm, it can be used without any restrictions. GnuPG is a RFC2440 (OpenPGP Message Format) compliant application. GPG Encryption Protocol Support GnuPG supports the ElGamal, DSA, RSA, AES, 3DES, Blowfish, Twofish, CAST5, MD5, SHA-1, RIPE-MD-160 and TIGER algorithms. Additional Reading on GPG For more information on Read More
File Manipulation
A file is basically a set of records stored on your computer's secondary memory. There may be situations requiring a program to open more than one file. The strategy for opening multiple files depends upon how they will be used. If the situation requires simultaneous processing of two files, then you need to create a separate stream for each file. However, if the situation demands sequential processing of files (i.e., processing them one by one), then one can open a single stream and associate it with each file in turn. Read More
Configuring and Troubleshooting Active Directory Replication
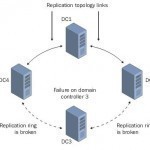
Active Directory is a distributed multimaster replicated database. All domain controllers host a full replica of the domain information for its own domain. Domain controllers in Windows 2000 and Windows Server 2003 environments hold a read/write copy of the Active Directory database. In these environments, changes can be made to the Active Directory database on any domain controller within the Active Directory environment. Replication is the process that ensures that changes made to a replica on one domain controller are transferred to replicas on the remainder of the domain controllers. Read More
Radar Laser Detector
A radar laser detector (although separately known as a radar detector and a laser detector) is commonly used by motorists to see if their speed is being spied on by some radar unit. Simply put, the police would "shoot" a radio wave to the moving vehicle with a radar gun, and the speed would be calculated using the principles of the Doppler Effect. In addition, recent speed detectors have evolved into using the laser technology. Also known as LIDAR (Light Detection and Ranging), it uses pulsed laser instead of the Read More
Corel Draw Tutorials
Corel Draw Tutorials This section contains various Corel Draw topics and tutorials. Here you will learn how to create animated GIFs, Yahoo Style buttons, create cracked text, gel text, complex shapes, port a Masked (Cropped) Bitmap, and animate an egyptian eye using Corel Draw. Animated GIFs Tutorial This contains how to topics on how to create a simple Animated GIF logo. This can be done easily and all you have got to do is follow the instructions in the tutorial. Creating Yahoo! Style Buttons Tutorial Want to learn how to create Read More


Share on: