When a coin is inserted into a payphone, the payphone emits a set of tones to ACTS (Automated Coin Toll System). Red boxes work by fooling ACTS into believing you have actually put money into the phone. The red box simply plays the ACTS tones into the telephone microphone. ACTS hears those tones, and allows you to place your call. The actual tones are: Nickel: 35-160ms 1700hz & 2200hz tone burst, followed by 240ms of silence. Dime: Two 35-160ms 1700hz & 2200hz bursts, with a spacing of 20-110ms between the Read More
Motes

Motes are also sometimes referred to as smart dust. One mote is composed of a small, low powered and cheap computer connected to several sensors and a radio transmitter capable of forming adhoc networks. The computer monitors the different sensors in a mote. These sensors can measure light, acceleration, position, stress, pressure, humidity, sound, and vibration among others. Data gathered are passed on to the radio link for transmission from mote to mote until data reaches the transmission node. These radio links between motes have a transmission distance of 10-200 Read More
How to Stream Audio
Streaming audio involves transmitting music files over the Internet in real-time and playing it on a client-side computer as it arrives. Streaming is different than podcasts because it allows for continuous, live music rather than scheduled uploads. Streaming is often used for music, talk radio, and live web events by radio hosts, politicians, and even average people. Streaming audio can be entertaining, useful, and fun but to do it, the user needs a service that allows them to stream audio to the Internet. Several of these services are listed below. Read More
Managing the IIS Metabase
An Overview of the IIS Metabase With the introduction of IIS 4, came the introduction of the metabase. IIS configuration information was no longer stored in the Registry, but in the new metabase structure. Some IIS configuration settings however still remained stored in the Registry, under the following keys: HKLMSOFTWAREMicrosoftInetMgrParameters HKLMSYSTEMCurrentControlSetServicesInetInfoParameters HKLMSYSTEMCurrentControlSetServicesASPParameters HKLMSYSTEMCurrentControlSetServicesHttpParametersLogBufferSize HKLMSYSTEMCurrentControlSetServicesW3SVCParameters HKLMSYSTEMCurrentControlSetServicesMSFTPSVCParameters In IIS 4, separating the majority of IIS configuration settings into the metabase; speeded up access to the information. The issue with the metabase in IIS 4 and IIS 5 was that it was a Read More
What is Bluejacking?

Bluejacking is a relatively new term that describes the act of sending an anonymous message to other Bluetooth equipped devices such as mobile phones, laptops, printers, cars, and Personal Data Assistants (PDAs). To date, mobile users have primarily Bluejacked others in their general proximity for friendly purposes. Bluejacking is possible because Bluetooth technology is open to receiving communications within the device’s effective range in the 2.4 GHz frequency band. How does Bluejacking Work? If a device is Bluetooth enabled, it can send or receive Bluejacking messages. The message is sent Read More
ReadyBoost
Ready Boost is an operating system feature introduced with Microsoft's Windows Vista operating system. The best way to improve the functioning of a PC is to increase its memory as increased memory enables more applications to operate on the computer. But this is not possible in many PCs as they have a maximum limit of memory and to increase it will call for upgrading memory which is very costly and some machines have limited expansion capabilities which don't enable the expansion. It is here that the Windows Vista comes to Read More
How to Change the Swap File Settings
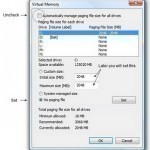
Prior to revising your Virtual Memory settings, you should check on how much Virtual Memory you would need, based on how much RAM you do have and how memory-intensive your normal applications are. Specifying Virtual Memory Settings The best way to do this is by installing the built-in System Monitor applet from the Add/Remove Program component in the Control Panel. Go to Windows Setup, highlight System Tools and click Details. Put a check on System Monitor and then hit the OK button, and exit the program. A prompt will appear Read More
How to Develop Android Apps
An Android is a smartphone that Google created that combines the functionality of a cell phone and a computer. While the Android does not include many features that a real computer does, it allows the user to take advantage of a wide variety of applications that can be used to perform diverse tasks that the Android itself does not support. Apple as well as its users create these applications. In order to create Android applications, users can implement the following programs and reference materials: What is the Android Software Read More
Potassium Benzoate
Potassium benzoate is the potassium salt of benzoic acid. Benzoic acids are weak acids that are used as food preservatives. Potassium benzoate is also commonly used for preserving food. It is primarily used to inhibit mold and bacteria growth. This allows the product that potassium benzoate preserves to last longer on the shelf, thereby increasing profits for the company that produced it. The ideal pH for products using potassium benzoate as a preservative is below 4.5 because that is where it exists as benzoic acid. Acidic food or beverages such Read More
Spot Beam
A spot beam is a beam of radio signals that is directed towards a specific area on the Earth’s surface. Spot beams are the opposite of broad beams, which are beams that are directed towards a large area of the Earth’s surface. While broad beams are used for general telecommunication and surveillance, spot beams are used for magnified views of the Earth and are ideal for targeting purposes and close-up surveillance of specific areas. Spot beams are also used in telecommunications for direct links between a specific satellite and a Read More


Share on: