Microsoft's Windows Installer components comprise the small constituents of a program, which are installed or removed collectively. They provide a useful way to not only install programs, but also gives the user the ability to manage these programs as well. Therefore, Microsoft Windows Installer has numerous functions to improve the tasks completed by the user: The Windows Installer can be used to remove programs already installed on the hard drive. By using the Windows Installer, all of the components of the program will be removed such as files, folders, and Read More
Crosstalk
Crosstalk is a form of interference caused by signals in nearby conductors. The most common example is hearing an unwanted conversation on the telephone. Crosstalk can also occur in radios, televisions, networking equipment, and even electric guitars. Causes of Crosstalk Crosstalk is caused by coupling, the transfer of electrical energy between conductors. The three main types of coupling are capacitive, inductive, and conductive. Capacitive coupling occurs when two separate conductors are close enough together to act as a capacitor. Inductive coupling occurs when the current in one conductor induced a Read More
What is a QSIG?
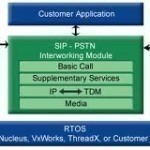
QSIG is a signaling protocol that is based on ISDN. It communicates signals between private branch exchanges (PBXs) within a Private Integrated Services Network (PISN) using the application-level ROSE and connection-level Q9.31 protocols. QSIG uses ISDN as the physical link layer in the exchanges and is often used in enterprise voice or integrated service networks. The Q reference point that the protocol derives its name from is the formal dividing or demarcation point between two PINXs (Private Integrated Network Exchanges). Who Invented the QSIG Protocol? ECMA International first created the Read More
How Do You Make a Heart on Facebook?
Facebook users often see the heart symbol “?” on status updates and want to know how to apply it to their own updates. The process is simple and can be accomplished in three ways: Direct Input into Facebook The fastest way to enter the heart character on Facebook is to use the less than three method. Users should place “<3” wherever they want a heart to appear on their status. For example, if a user wants to say “I ? this song” they should type “I <3 this song”. Alt Read More
How to Zip Files on a Mac
With the advent of the Internet, there have been many different archive programs created over the past few years, the majority of which are accessible for free. While most of these programs are nearly identical, each has its own advantages and disadvantages. Likewise, not all of these programs are compatible with the same operating systems and other programming environments. This article will focus specifically on archive programs that are compatible with the various Mac operating systems. ZipIt ZipIt runs on Mac OS X and is made specifically for moving files Read More
How to Securely Erase Data

When you erase a file on your computer, the actual data in the file is not overwritten. The space utilized by that file is simply marked as “free” for use by other data. Once other data is written in that space, the original data becomes unrecoverable — by most people. Those little bits of magnetic media that store 0’s and 1’s are a bit more complex, however. With sensitive and sophisticated equipment, it is theoretically possible to recover data even after it has been written over. The method to securely Read More
Database Trigger

A database trigger is a procedural code that automatically changes information in one or more databases in response to a change on another database or table. For example, when an employer creates a slot in a list of employees for a new employee, the database trigger in that list should automatically add the new employee to lists for vacations, sick days, salaries, and/or other information. Database triggers prevent computer administrators from having to manually add new information to multiple tables, charts, or databases. How Database Triggers Work A database Read More
RADIUS (Remote Authentication Dial in User Service)
RADIUS (Remote Authentication Dial In User Service), defined in RFC 2865, is a protocol for remote user authentication and accounting. RADIUS enables centralized management of authentication data, such as usernames and passwords. When a user attempts to login to a RADIUS client, such as a router, the router send the authentication request to the RADIUS server. The communication between the RADIUS client and the RADIUS server are authenticated and encrypted through the use of a shared secret, which is not transmitted over the network. The RADIUS server may store the Read More
Implementing Proxy Server
Designing a Proxy Server Implementation Before you can design a Proxy Server implementation and install Proxy Server, you need to be knowledgeable on a number of concepts: IP routing concepts Firewalls concepts Packet filtering concepts Files and protocols utilized in Web applications To design a Proxy Server implementation, there are a number of factors that has an impact on the Proxy Server design: The characteristics of data that will pass to the Proxy Server. Data characteristics should include factors such as the quantity of data which you expect the Proxy Read More
What is Electrotherapy?

Electrotherapy is a medical technique in which an electric current is used to perform a wide variety of tasks associated with pain, neurological disorders, muscle-related conditions, and drug delivery. Electrotherapy includes a range of medical techniques, some of which are under much debate and criticism. While electrotherapy itself is an accepted form of medical treatment, electromagnetic therapy (a subset of electrotherapy) is usually discredited due to little evidence of either positive or negative effects. How Electrotherapy Works In electrotherapy, an electric current is applied directly to a muscle or tissue Read More


Share on: